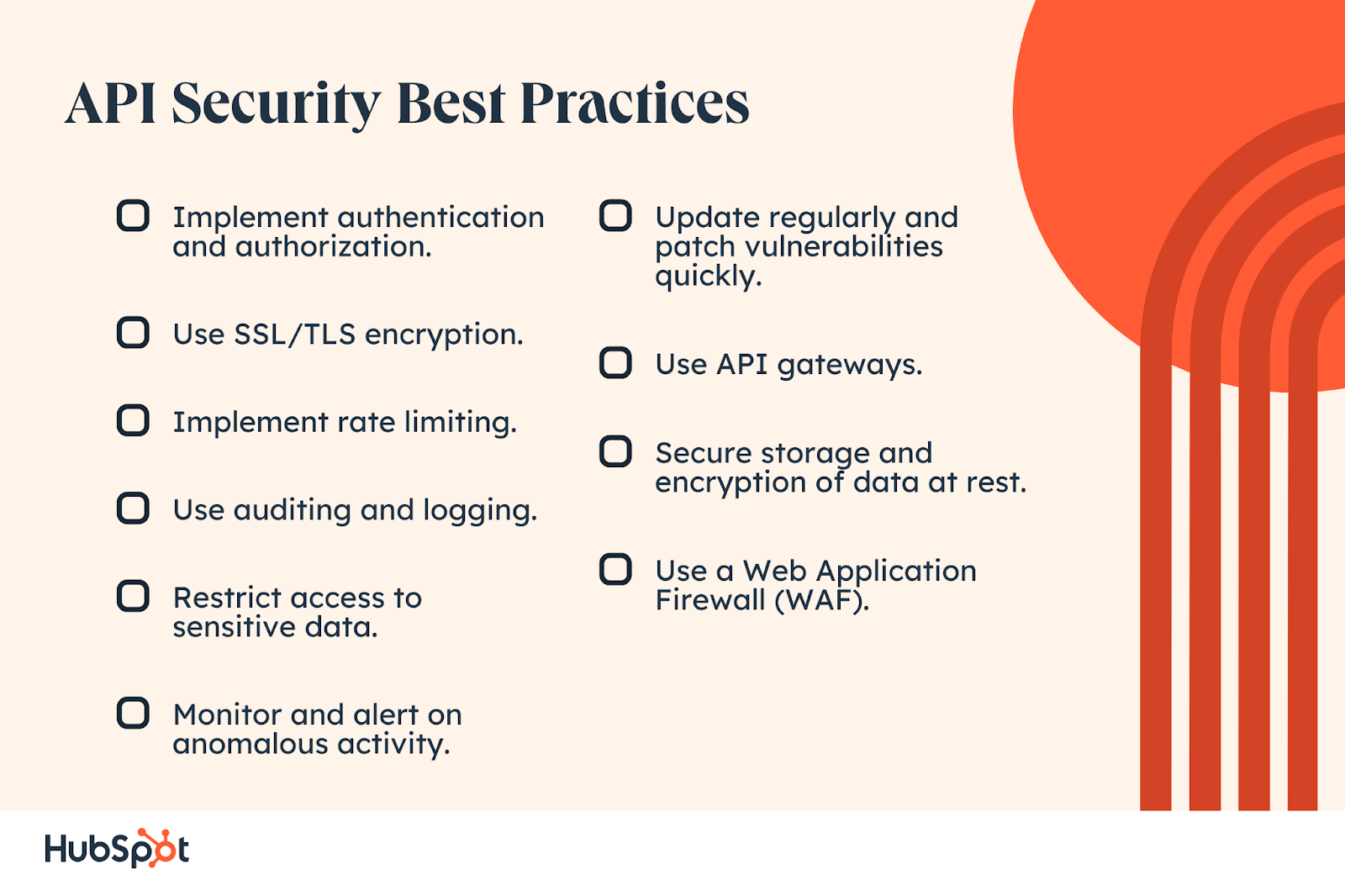
Are API calls encrypted?
Summary of the Article: Are API Calls Encrypted?
1. How is the API encrypted?
By default, the server uses SET AUTHENTICATION ON. The API uses either AES 128-bit or AES 256-bit encryption. AES 256-bit data encryption provides a higher level of data encryption than AES 128-bit data encryption.
2. Does API data need to be encrypted?
Without encryption, an attacker who is able to intercept the communication between an API and its clients could potentially view or modify the data being transmitted (i.e., man-in-the-middle attacks). A common way to encrypt API traffic is to require the use of HTTPS and SSL/TLS.
3. How do I make REST API calls secure?
Use HTTPS/TLS for REST APIs. HTTPS and Transport Layer Security (TLS) offer a secured protocol to transfer encrypted data between web browsers and servers. Apart from other forms of information, HTTPS also helps to protect authentication credentials in transit.
4. What encryption does a REST API use?
Transport Layer Security (TLS) encryption. For instance, REST APIs use HTTP and support Transport Layer Security (TLS) encryption, a standard encryption that keeps your internet connection secure, and checks that the data shared between the two systems and APIs are encrypted and unmodified.
5. How do I know if an API is secure?
To test if parameter tampering is possible, you can examine any API related elements in your site or web app through the development console in your browser. If you change the value in your console, submit it with the included change, and the application accepts it, your API is not secure.
6. Are REST APIs secure?
REST API security is dependent on the adequacy of SSL certificate validation processes. Any exploitable weakness will allow attackers unauthorized access to API keys and authentication credentials. Our API Management solution offers easy access management for your REST APIs.
7. Are AWS API calls encrypted?
All AWS services offer the ability to encrypt data at rest and in transit.
8. Can API calls be intercepted?
A man-in-the-middle (MITM) attack occurs when a hacker intercepts an API request or response between an end-user and an API. They may steal the sensitive contents of this communication (e.g. account login credentials or payment information) or modify the contents of the request/response.
9. Are API calls safe?
An API call is considered safe if it is made with the correct credentials and if it’s not being used for malicious purposes. However, API calls can lead to an attack if they are not properly secured. This is because the API call is made from a different domain than the one that it is being called from.
10. How to secure an API without authentication?
Encryption – Having encryption enabled on the API and using HTTPS using TLS secures the channel as well as the information sent. Rate limiting and throttling – Limiting the number of requests coming into an API helps prevent abuse.
11. How to decrypt API response?
Send the encrypted request: Add the encrypted request, the symmetric key, and IV to the header of the HTTP request. Decrypt the response: On the server side, extract the symmetric key and IV from the header and use them to decrypt the response. Return the decrypted response: Return the decrypted response to the client.
How is the API encrypted
By default, the server uses SET AUTHENTICATION ON . The API uses either AES 128-bit or AES 256-bit encryption. AES 256-bit data encryption provides a higher level of data encryption than AES 128-bit data encryption.
Cached
Does API data need to be encrypted
Without encryption, an attacker who is able to intercept the communication between an API and its clients could potentially view or modify the data being transmitted (i.e., man-in-the-middle attacks). A common way to encrypt API traffic is to require the use of HTTPS and SSL/TLS.
Cached
How do I make REST API calls secure
Use HTTPS/TLS for REST APIs
HTTPS and Transport Layer Security (TLS) offer a secured protocol to transfer encrypted data between web browsers and servers. Apart from other forms of information, HTTPS also helps to protect authentication credentials in transit.
Cached
What encryption does a REST API use
Transport Layer Security (TLS) encryption
For instance, REST APIs use HTTP and support Transport Layer Security (TLS) encryption, a standard encryption that keeps your internet connection secure, and checks that the data shared between the two systems and APIs are encrypted and unmodified.
Cached
How do I know if an API is secure
To test if parameter tampering is possible, you can examine any API related elements in your site or web app through the development console in your browser. If you change the value in your console, submit it with the included change, and the application accepts it, your API is not secure.
Are REST APIs secure
REST API security is dependent on the adequacy of SSL certificate validation processes. Any exploitable weakness will allow attackers unauthorized access to API keys and authentication credentials. Our API Management solution offers easy access management for your REST APIs.
Are AWS API calls encrypted
All AWS services offer the ability to encrypt data at rest and in transit.
Can API calls be intercepted
A man-in-the-middle (MITM) attack occurs when a hacker intercepts an API request or response between an end-user and an API. They may steal the sensitive contents of this communication (e.g. account login credentials or payment information) or modify the contents of the request/response.
Are API calls safe
An API call is considered safe if it is made with the correct credentials and if it's not being used for malicious purposes. However, API calls can lead to an attack if they are not properly secured. This is because the API call is made from a different domain than the one that it is being called from.
How to secure an API without authentication
Encryption — Having encryption enabled on the API and using https using TLS secures the channel as well as the information sent. Rate limiting and throttling — Limiting the number of requests coming into an API helps prevent abuse.
How to decrypt API response
Send the encrypted request: Add the encrypted request, the symmetric key, and IV to the header of the HTTP request. Decrypt the response: On the server side, extract the symmetric key and IV from the header and use them to decrypt the response. Return the decrypted response: Return the decrypted response to the client.
Are APIs a security risk
Like any software, APIs can be compromised and your data can be stolen. Since APIs serve as conduits that reveal applications for third-party integration, they are susceptible to attacks.
Can API calls be tracked
API usage can be tracked using the X-Powered-By HTTP header which includes a unique ID generated for each subscription and a unique ID generated for each user. Once enabled, the X-Powered-By HTTP header is returned for each API request made by a user.
Do API calls use TLS
HTTP is a protocol for transferring data between websites. An HTTPS transfer or API call is simply an HTTP call over a connection secured by TLS.
Can you trace an API call
Be sure the API you wish to trace is deployed. Click Trace to go to the Trace tool view. Use the Deployment to Trace dropdown menu to select which deployment environment and proxy revision you wish to trace. Click Start Trace Session.
What happens when you make an API call
An API call is a term for the request made by the client application that will result in the corresponding application or server providing a predefined response. Typically, an API call transfers information to the client application for user processing or in the other direction for managing and storage.
Do all APIs need authentication
Most APIs require authentication to let you use the API. The Authentication & Authorization process allows APIs to verify your identity and decide what actions you can take using the API. In this article, I will go through four common ways of API authorization.
Does API need authentication
Application Programming Interfaces (API's) are the vital links that allow applications to exchange services and data and require authentication before the exchange can take place.
How do I encrypt and decrypt an API
Execute the application.Type some text and select "Encrypt". Click on the "Submit" button. It generates an encrypted code version of the text.Copy the encrypted code and paste it into the text box and select decrypt. Now click on the "Submit" button. It generates the original text.
How do you encrypt and decrypt data in API
Procedure to encrypt a messagePrepare the content to be encrypted.Generate the AES symmetric key.Encrypt the content.Encrypt the AES key.Configure the header and body.Get the content to be decrypted.Extract the encrypted AES symmetric key.Decrypt the AES key.
What are the risks of API
The OWASP Top 10 API security challenges include broken object-level authorization, broken user authentication, excessive data exposure, lack of resources and rate limiting, broken function-level authorization, mass assignment, security misconfiguration, injection, improper asset management, and insufficient logging …
Do API calls get cached
Caching stores and retrieves data from a software or hardware component. When a client (such as a browser) makes a REST API request, it can save the API response in a cache. The next time the client initiates that request, it gets a faster response because the server doesn't have to process it all over again.
Do API calls use HTTPS
Introduction. All APIs should use and require HTTPS to help guarantee confidentiality, authenticity, and integrity. HTTPS provides a stronger guarantee that a client is communicating with the real API and receiving back authentic contents. It also enhances privacy for applications and users using the API.
How do you authenticate an API call
To authenticate API requests, you can use basic authentication with your email address and password, your email address and an API token, or an OAuth access token. All methods of authentication set the authorization header differently. Credentials sent in the payload or URL are not processed.
How to encrypt web API
Execute the application.Type some text and select "Encrypt". Click on the "Submit" button. It generates an encrypted code version of the text.Copy the encrypted code and paste it into the text box and select decrypt. Now click on the "Submit" button. It generates the original text.



