Are API calls safe?
Are API calls secure?
APIs provide users, applications, and IoT devices access to sensitive data and other network resources. But without robust security, they’re highly vulnerable to a variety of attacks that can lead to data breaches and compromised networks.
What are the risks of using an API?
1. Bad coding: Starting off with poor coding exposes you to serious API security risks.
2. Inadequate validation: Failing to properly validate inputs can lead to security vulnerabilities.
3. Hesitating over API utilization: Delaying the adoption of APIs can cause security risks.
4. Accountability: Lack of clear ownership and responsibility for API security can lead to vulnerabilities.
5. Risks of XML: XML-related vulnerabilities can be exploited to compromise API security.
6. API incompetence: Poorly designed or implemented APIs can expose security weaknesses.
7. Lack of security: Neglecting proper security measures is a recipe for disaster.
8. Going overboard with control: Excessive security measures can hinder the usability of APIs.
How do I know if my API is safe?
To test if parameter tampering is possible, you can examine any API-related elements in your site or web app through the development console in your browser. If you change the value in your console, submit it with the included change, and the application accepts it, your API is not secure.
What happens when you make an API call?
An API call is a term for the request made by the client application that will result in the corresponding application or server providing a predefined response. Typically, an API call transfers information to the client application for user processing or in the other direction for managing and storage.
Can API calls be tracked?
API usage can be tracked using the X-Powered-By HTTP header, which includes a unique ID generated for each subscription and a unique ID generated for each user. Once enabled, the X-Powered-By HTTP header is returned for each API request made by a user.
Can API calls be intercepted?
A man-in-the-middle (MITM) attack occurs when a hacker intercepts an API request or response between an end-user and an API. They may steal the sensitive contents of this communication (e.g., account login credentials or payment information) or modify the contents of the request/response.
When should you not use API?
1. It already has an API: If your system already has an API, especially HTTP, there’s no need to create another one.
2. It will break: If your API is prone to breaking or causing disruptions, it may not be worth implementing.
3. It will change: APIs that undergo frequent changes can be difficult to maintain and use.
4. It will be slow: Slow APIs can negatively impact user experiences and overall system performance.
5. It will be hard to parse: APIs with complex data structures can be challenging to parse and work with.
Why would someone use an API?
APIs are needed to bring applications together to perform a designed function built around sharing data and executing predefined processes. They serve as the middle man, allowing developers to build new programmatic interactions between various applications people and businesses use on a daily basis.
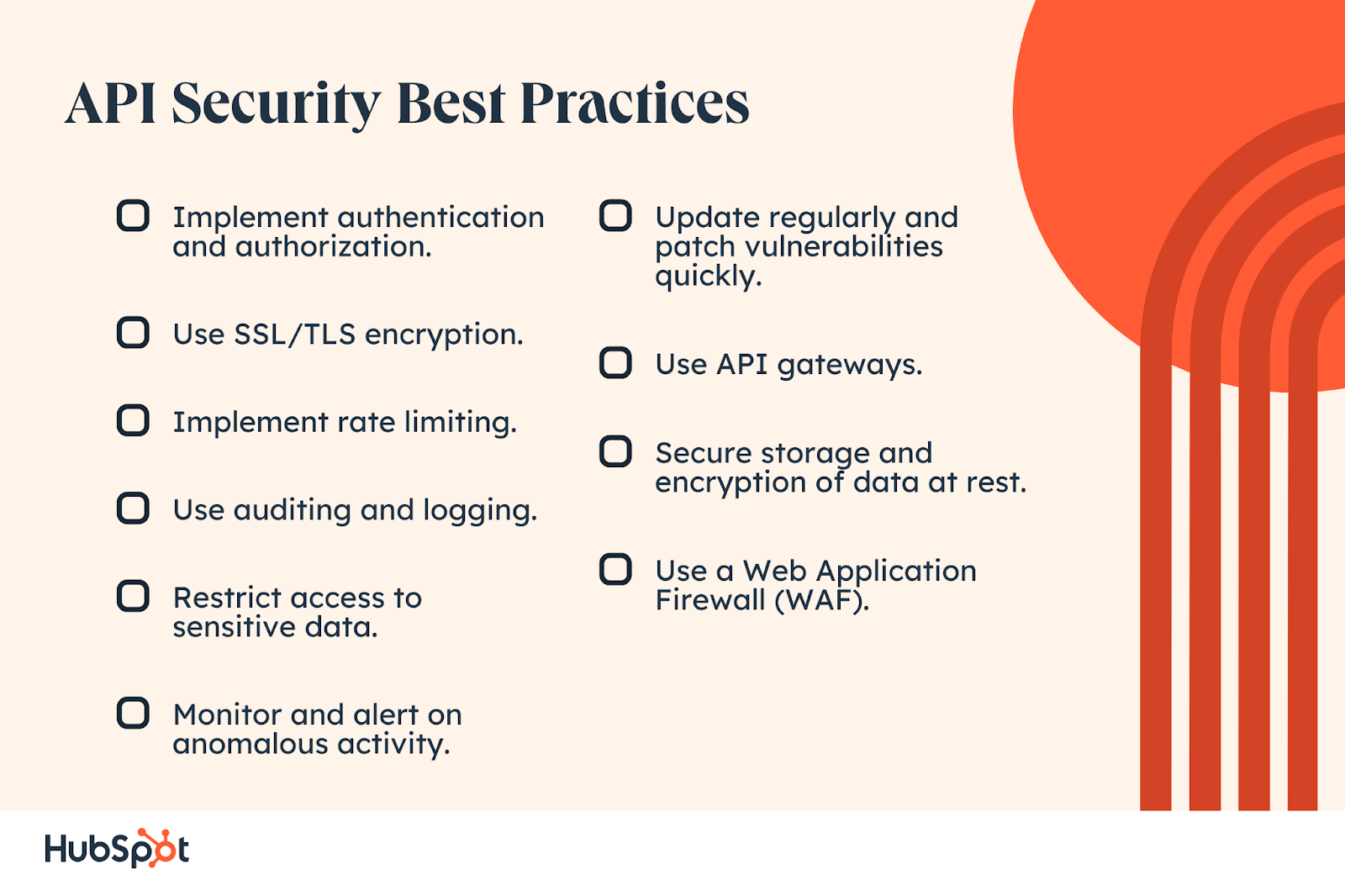
How do I make my API call secure?
Use SSL/TLS encryption. All communications between APIs and clients should be secured through an SSL connection or TLS encryption protocol like HTTPS. This ensures that all data sent over the wire is encrypted and kept safe from malicious third parties.
Is an API call a side effect?
Calling any native Web APIs will be considered a side effect as it’s not within the React universe. Making an HTTPS request to an external API is another example of a side effect.
Should I log API calls?
First, we recommend that you always log the HTTP response code that you get from each request. This will allow you to look back and analyze any potential issues with your API calls. Additionally, you may want to consider logging additional information such as request duration, request and response payloads, and any error messages.
Are API calls secure
APIs provide users, applications and IoT devices access to sensitive data and other network resources. But without robust security, they're highly vulnerable to a variety of attacks that can lead to data breaches and compromised networks.
What are the risks of using an API
Top 10 API Security RisksBad coding. Right off the bat, if you start off with bad coding, you are exposing yourself to serious API security risks.Inadequate validation.Hesitating over API utilization.Accountability.Risks of XML.API incompetence.Lack of security—a terrible idea.Going overboard with control.
How do I know if my API is safe
To test if parameter tampering is possible, you can examine any API related elements in your site or web app through the development console in your browser. If you change the value in your console, submit it with the included change, and the application accepts it, your API is not secure.
Cached
What happens when you make an API call
An API call is a term for the request made by the client application that will result in the corresponding application or server providing a predefined response. Typically, an API call transfers information to the client application for user processing or in the other direction for managing and storage.
Can API calls be tracked
API usage can be tracked using the X-Powered-By HTTP header which includes a unique ID generated for each subscription and a unique ID generated for each user. Once enabled, the X-Powered-By HTTP header is returned for each API request made by a user.
Can API calls be intercepted
A man-in-the-middle (MITM) attack occurs when a hacker intercepts an API request or response between an end-user and an API. They may steal the sensitive contents of this communication (e.g. account login credentials or payment information) or modify the contents of the request/response.
When should you not use API
Here are some reasons not to create a REST API for your system.It already has an API. Your system already has an API. And it is called HTTP.It Will Break. Your API will break.It Will Change. Ha!It Will Be Slow. Your API will be slow.It Will Be Hard To Parse. I am sure many of you parsed JSON documents. “
Why would someone use an API
APIs are needed to bring applications together in order to perform a designed function built around sharing data and executing pre-defined processes. They work as the middle man, allowing developers to build new programmatic interactions between the various applications people and businesses use on a daily basis.
How do I make my API call secure
Use SSL/TLS encryption.
All communications between APIs and clients should be secured through an SSL connection or TLS encryption protocol like HTTPS. This ensures that all data sent over the wire is encrypted and kept safe from malicious third parties.
Is API call a side effect
So calling any native Web APIs will be considered as a side effect as it's not within the React universe. Making a HTTPS request to an external API is another example of a side effect and the list goes on…
Should I log API calls
First, we recommend that you always log the HTTP response code that you get from each request. This will allow you to look back and find out if there was a problem with a particular request, or to trigger automatic retries.
How do you escape an API call
The syntax of some API responses may contain the escape character, \ (backslash). An escape character indicates that the character or string of characters that immediately follow the escaped character have a special value.
Can you trace an API call
Be sure the API you wish to trace is deployed. Click Trace to go to the Trace tool view. Use the Deployment to Trace dropdown menu to select which deployment environment and proxy revision you wish to trace. Click Start Trace Session.
How do you check if an API is being used
API testing flow is quite simple with three main steps:Send the request with necessary input data.Get the response having output data.Verify that the response returned as expected in the requirement.
What is an API call
An API call, or API request, allows one application to request data or services from another application. Most web applications regularly make API calls. API Security. Web application security.
What does an API tell you
APIs are sets of definitions and protocols that allow software components to talk and interact with each other using a simple set of commands. Acting as messengers, APIs deliver one application's request to another and return a response in real time.
What is bad request when calling API
The 400 Bad request status code indicates that the server was unable to process the request due to invalid information sent by the client. In other words, the client request needs modification.
How do I verify an API call
API testing flow is quite simple with three main steps:Send the request with necessary input data.Get the response having output data.Verify that the response returned as expected in the requirement.
How do I validate API calls
How to validate API validation can be accomplished in a variety of ways, but the most common are static analysis, dynamic analysis, and fuzz testing. Static analysis is the process of manually going through an API's code to look for security holes.
What is API calls in malware
Windows API, in short, the WinAPI, is a set of functions and procedures, which can abstract much of the tasks you perform everyday on the Windows OS. The Application Programming Interface (API) calls exposes these functions to programmers to make use of procedures when writing one of your own isn't the most effective.
What is an example of an API call
Simply put, the moment you add an endpoint to a URL and send a request to a server, this is what counts as making an API call. For example, when you log on to any app or ask a question via a browser, you are actually making an API call.
What is an API warning
If something goes wrong in an API request, an error or a warning will be thrown (although the HTTP response will usually still be 200 OK ). Warnings are thrown for non-fatal conditions such as invalid parameters, whereas errors are only thrown for fatal conditions.
How do I track API calls
API MonitoringSign Up for an Account on RapidAPI.Create an API. Download API Spec. Add New API. Build a Test. Inspect Request Generator. Select Assertions. Run Test & View Results. Create Environments.Schedule Tests to Monitor API Performance with RapidAPI Testing.View Execution Reports.Monitor Latency vs. Size.Set Alerts.
What API means
Application Programming Interface
What does API stand for API stands for Application Programming Interface. In the context of APIs, the word Application refers to any software with a distinct function. Interface can be thought of as a contract of service between two applications.
What are the 4 types of API calls
There are four different types of APIs commonly used in web services: public, partner, private and composite.



