Are cyber threat maps real?
Summary of the Article
How accurate are cyber threat maps?
You will see but a very small percentage of the real attacks as they are carefully curated to make it all “look purdy.” Nice to show to management because it visualizes the problem and makes it very easy to understand, but do not count on any actual accuracy.
Are live cyber threat maps real?
A cyber threat map, also known as a cyber-attack map, is a real-time map of the computer security attacks that are going on at any given time.
How does a cyber threat map work?
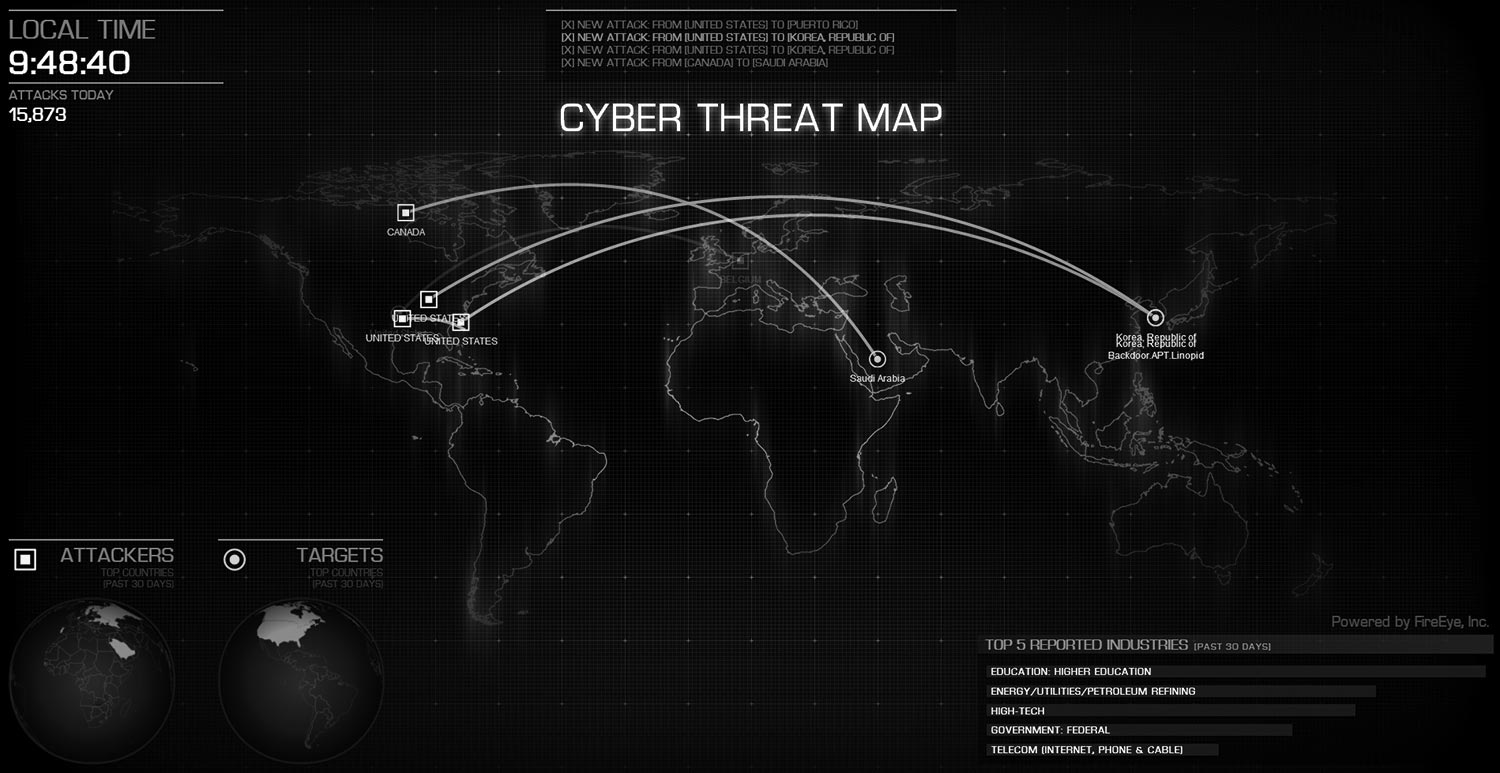
CYBERTHREAT REAL-TIME MAP
The main map color codes its attacks by severity to make it easier to focus on the most critical situations, coded in red. The details of these attacks scroll quickly along the bottom of the map, where the viewer can identify the threat type and location.
Is FireEye map real?
FireEye Cyber Threat Map is a minimal real-time threat visualization that gives quick insights into the current global attacks. It requires a large screen size.
Can 95% of cybersecurity issues be traced to human error?
Businesses, in turn, find themselves facing a reality where 95% of all incidents occur due to human error, with 43% of breaches attributed to insider threats.
Is cyber threat a spy?
Cyber espionage (cyberespionage) is a type of cyber attack that malicious hackers carry out against a business or government entity. The goal of cyber espionage, also referred to as cyber spying, is to provide attackers with information that gives them advantages over rival companies or governments.
Is cyber spying illegal?
More recently, cyber spying involves analysis of public activity on social networking sites like Facebook and Twitter. Such operations, like non-cyber espionage, are typically illegal in the victim country while fully supported by the highest level of government in the aggressor country.
How are cyber criminals tracked down?
Cyber Crime Units
Many police departments are training Internet or Computer Crime units that people can contact for information and assistance. These units support law enforcement in investigating cyber crimes and tracking down cyber criminals.
What is the best real-time cyber threat map?
FireEye is one of the well-known cyber attack maps available on the internet nowadays, as it generally allows you to get a unique summary of whole attacks with the following data.
What is FireEye called now?
Symphony Technology Group companies gain a new name after the merger.
Where do 90% of all cyber incidents begin?
Fend Off Phishing: Learn how more than 90% of all cyber attacks begin with phishing. Find out how attackers leverage phishing attacks to gain access to protected systems, hosts, and networks. Discover how technology can be used to mitigate phishing attacks and train users to better recognize phishing emails.
Are 90% of cyber attacks due to human error?
Researchers from Stanford University and a top cybersecurity organization found that approximately 88 percent of all data breaches result from human error.
How accurate are cyber threat maps
You will see but a very small percentage of the real attacks as they are carefully curated to make it all "look purdy." Nice to show to management because it visualizes the problem and makes it very easy to understand, but do not count on any actual accuracy.
CachedSimilar
Are live cyber threat maps real
A cyber threat map, also known as a cyber-attack map, is a real-time map of the computer security attacks that are going on at any given time.
Cached
How does cyber threat map work
CYBERTHREAT REAL-TIME MAP
The main map color codes its attacks by severity to make it easier to focus on the most critical situations, coded in red. The details of these attacks scroll quickly along the bottom of the map, where the viewer can identify the threat type and location.
Cached
Is FireEye map real
FireEye Cyber Threat Map is a minimal real-time threat visualization that gives quick insights into the current global attacks. It requires a large screen size.
Cached
Can 95% of cybersecurity issues be traced to human error
Businesses, in turn, find themselves facing a reality where 95% of all incidents occur due to human error, with 43% of breaches attributed to insider threats.
Is cyber threat a spy
Cyber espionage (cyberespionage) is a type of cyber attack that malicious hackers carry out against a business or government entity. The goal of cyber espionage, also referred to as cyber spying, is to provide attackers with information that gives them advantages over rival companies or governments.
Is cyber spying illegal
More recently, cyber spying involves analysis of public activity on social networking sites like Facebook and Twitter. Such operations, like non-cyber espionage, are typically illegal in the victim country while fully supported by the highest level of government in the aggressor country.
How are cyber criminals tracked down
Cyber Crime Units
Many police departments are training Internet or Computer Crime units that people can contact for information and assistance. These units support the law enforcement in investigating cyber crimes and tracking down cyber criminals.
What is the best real time cyber threat map
FireEye is one of the well-known cyber attack maps available on the internet nowadays, as it generally allows you to get a unique summary of whole attacks with the following data.
What is FireEye called now
Symphony Technology Group companies gain a new name after merger.
Where do 90% of all cyber incidents begin
Fend Off Phishing : Learn how more than 90% of all cyber attacks begin with phishing. Find out how attackers leverage phishing attacks to gain access to protected systems, hosts, and networks. Discover how technology can be used to mitigate phishing attacks and train users to better recognize phishing emails.
Are 90% of cyber attacks due to human error
Researchers from Stanford University and a top cybersecurity organization found that approximately 88 percent of all data breaches are caused by an employee mistake.
Does the FBI use cyber security
The information that the FBI uniquely collects helps the Cybersecurity and Infrastructure Security Agency (CISA) to identify other networks vulnerable to the same adversary technique, helps Sector Risk Management Agencies assess and mitigate cyber threats to critical infrastructure, provides U.S. Cyber Command or the …
Who is the biggest cyber threat
The Biggest Cybersecurity Issues and Challenges in 2023Ransomware Extortion.Cloud Third-Party Threats.Mobile Malware.Wipers and Destructive Malware.Weaponization of Legitimate Tools.Zero-Day Vulnerabilities in Supply Chains.Global Attacks on Business.
Can someone spy on you through your internet
If someone hacks your Wi-Fi, they can monitor all of your unencrypted traffic. That means they can spy on data sent across your network from all of your devices, including personal information like your name, address, and even financial account details.
Can you go to jail for spying on someone
California's Peeping Tom laws make it a misdemeanor offense to spy on (or to take pictures of) someone in a private place without that person's consent. A conviction carries a potential sentence of up to 6 months in jail and fines of up to $1000.00.
Why hackers never get caught
Hackers will often use secure software such as a proxy server to hide their identity and funnel their communications through lots of different countries in order to evade detection. Other technologies like Tor and encryption enable them to add multiple layers to mask their identity.
Why do cyber criminals never get caught
Oftentimes, cybercriminals use secure software to remain anonymous which are proxy servers that hide their location and route their communications through multiple countries in order to evade direct detection, and commit the crimes in other countries where they cannot be prosecuted.
What are 90% of cyber attacks
Fend Off Phishing : Learn how more than 90% of all cyber attacks begin with phishing. Find out how attackers leverage phishing attacks to gain access to protected systems, hosts, and networks.
What is the biggest cyber threat today
Top 10 Cybersecurity Threats:Social Engineering.Third-Party Exposure.Configuration Mistakes.Poor Cyber Hygiene.Cloud Vulnerabilities.Mobile Device Vulnerabilities.Internet of Things.Ransomware.
Did McAfee buy FireEye
On Jan. 19, the private equity firm that bought FireEye and McAfee Enterprise announced that the two acquisitions would “emerge” to form Trellix, a cybersecurity business with 5,000 employees and 40,000 customers.
Is FireEye a part of Google
Google's acquisition announcement came less than a year after Mandiant and FireEye split. FireEye was sold to Symphony Technology Group last fall for $1.2 billion.
Which email is responsible for 91% of all cyber attacks
phishing email
Research by Deloitte found that 91% of all cyberattacks begin with a phishing email (an email that looks like it's from someone you know but is actually from criminals). That's how web giant Yahoo was targeted a few years ago, exposing the contents of half a billion user accounts to criminals.
What is 91% of successful data breaches
According to reports, 91% of all attacks begin with a phishing email to an unsuspecting victim. On top of that, 32% of all successful breaches involve the use of phishing techniques.
Where do 90% of all cyber attacks come from
Fend Off Phishing : Learn how more than 90% of all cyber attacks begin with phishing. Find out how attackers leverage phishing attacks to gain access to protected systems, hosts, and networks. Discover how technology can be used to mitigate phishing attacks and train users to better recognize phishing emails.



