Can API be intercepted?
Summary of the Article: Are APIs a Security Risk?
Like any software, APIs can be compromised and your data can be stolen. Since APIs serve as conduits that reveal applications for third-party integration, they are susceptible to attacks.
Here are some key points discussed in the article:
1. Are APIs a security risk?
Like any software, APIs can be compromised and your data can be stolen. Since APIs serve as conduits that reveal applications for third-party integration, they are susceptible to attacks.
2. How are APIs attacked?
An API attack is the malicious usage or attempted usage of an API from automated threats such as access violations, bot attacks, or abuse. An API attack can result in mass data losses, stolen private information, and service disruption.
3. How can APIs be hacked?
API Injection Attack: This kind of attack happens on an application running on poorly developed code. The hacker injects malicious code into software, like SQLi (SQL injection) and XSS (cross-site scripting) to gain access to your software.
4. Can APIs be encrypted?
One of the simplest and most effective ways to secure and encrypt your API data and traffic is to use HTTPS, or Hypertext Transfer Protocol Secure. HTTPS is a protocol that adds a layer of encryption and authentication to the standard HTTP protocol.
5. What are the risks of APIs?
The OWASP Top 10 API security challenges include broken object-level authorization, broken user authentication, excessive data exposure, lack of resources and rate limiting, broken function-level authorization, mass assignment, security misconfiguration, injection, improper asset management, and insufficient logging.
6. How are APIs vulnerable?
API vulnerabilities can occur when an API is poorly designed or implemented or is not adequately secured. Hackers can also exploit API vulnerabilities to launch different attacks, such as denial-of-service attacks, or to gain access to confidential information.
7. Can you DDoS an API?
DDoS API attacks focus not only on the server where your API is running but also on each endpoint of your API service. Your API service is attacked on both the server and the API service itself in more advanced attacks. This yields drastic results for the health of your API server in the case of a successful attack.
8. How do I know if an API is secure?
To test if parameter tampering is possible, you can examine any API-related elements in your site or web app through the development console in your browser. If you change the value in your console, submit it with the included change, and the application accepts it, your API is not secure.
9. What can someone do with your API key?
Stolen or accidentally exposed API keys and secrets can easily be exploited by threat actors and used to access sensitive information, impersonate your mobile app, or make API calls on its behalf.
10. How to secure an API without authentication?
Encryption: Having encryption enabled on the API and using HTTPS using TLS secure the channel as well as the information sent. Rate limiting and throttling: Limiting the number of requests coming into an API helps prevent abuse.
Questions and Detailed Answers:
1. Are APIs a security risk?
Like any software, APIs can be compromised and your data can be stolen. Since APIs serve as conduits that reveal applications for third-party integration, they are susceptible to attacks.
2. How are APIs attacked?
An API attack is the malicious usage or attempted usage of an API from automated threats such as access violations, bot attacks, or abuse. An API attack can result in mass data losses, stolen private information, and service disruption.
3. How can APIs be hacked?
API Injection Attack: This kind of attack happens on an application running on poorly developed code. The hacker injects malicious code into software, like SQLi (SQL injection) and XSS (cross-site scripting) to gain access to your software.
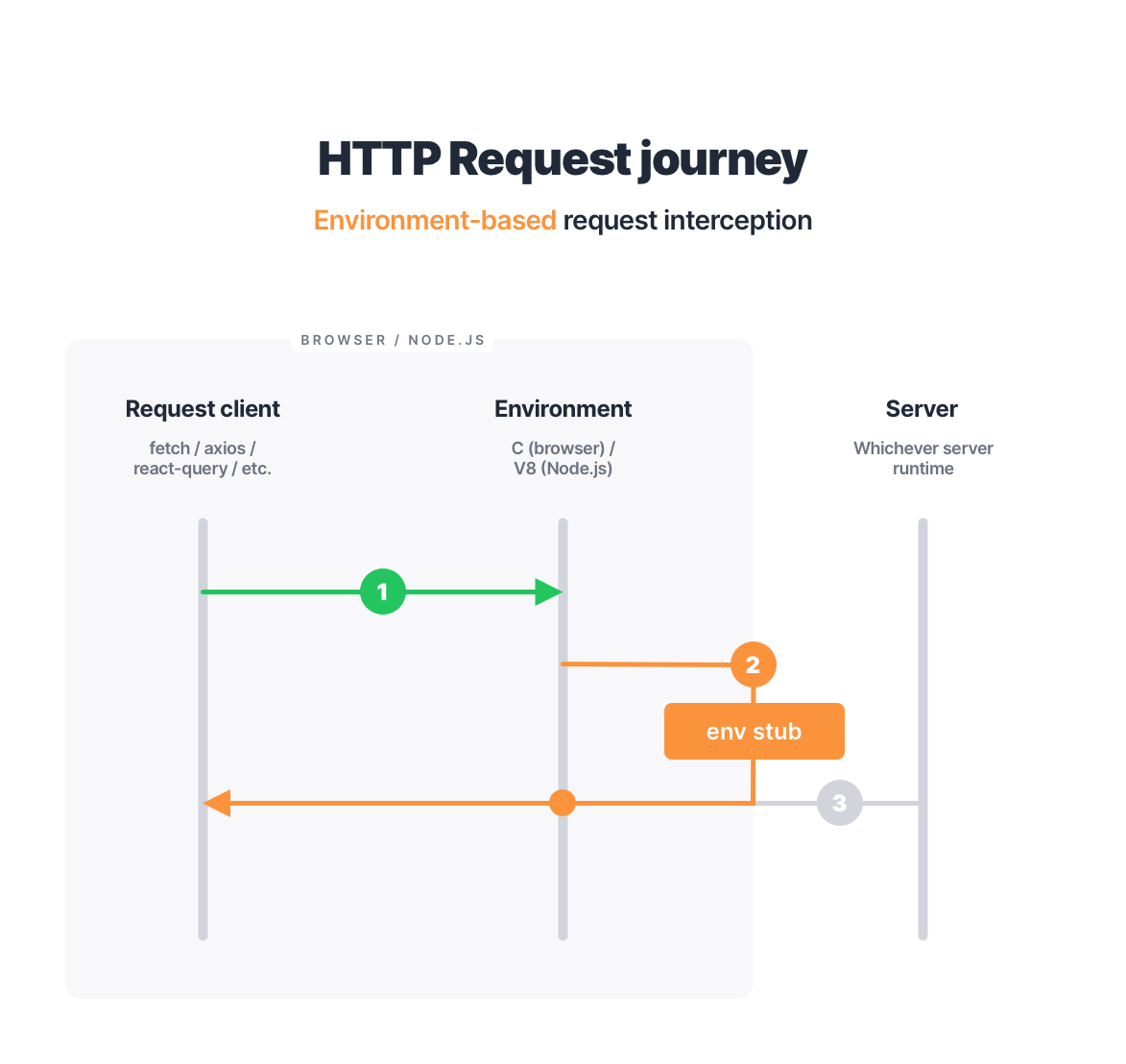
Are APIs a security risk
Like any software, APIs can be compromised and your data can be stolen. Since APIs serve as conduits that reveal applications for third-party integration, they are susceptible to attacks.
How are APIs attacked
An API attack is the malicious usage or attempted usage of an API from automated threats such as access violations, bot attacks or abuse. An API attack can result in mass data losses, stolen private information and service disruption. Examples of API attacks include: DoS/DDoS (Distributed Denial of Service) Attacks.
How API can be hacked
API Injection Attack
This kind of attack happens on an application running on poorly developed code. The hacker injects malicious code into software, like SQLi (SQL injection) and XSS (cross-site scripting) to gain access to your software.
Can API be encrypted
One of the simplest and most effective ways to secure and encrypt your API data and traffic is to use HTTPS, or Hypertext Transfer Protocol Secure. HTTPS is a protocol that adds a layer of encryption and authentication to the standard HTTP protocol.
What are the risks of API
The OWASP Top 10 API security challenges include broken object-level authorization, broken user authentication, excessive data exposure, lack of resources and rate limiting, broken function-level authorization, mass assignment, security misconfiguration, injection, improper asset management, and insufficient logging …
How are APIs vulnerable
API vulnerabilities can occur when an API is poorly designed or implemented or is not adequately secured. Hackers can also exploit API vulnerabilities to launch different attacks, such as denial-of-service attacks, or to gain access to confidential information.
Can you DDoS an API
DDoS API attacks focus not only on the server where your API is running but also on each endpoint of your API service. Your API service is attacked on both the server and the API service itself in more advanced attacks. This yields drastic results for the health of your API server in the case of a successful attack.
How do I know if an API is secure
To test if parameter tampering is possible, you can examine any API related elements in your site or web app through the development console in your browser. If you change the value in your console, submit it with the included change, and the application accepts it, your API is not secure.
What can someone do with your API key
Stolen or accidentally exposed API keys and secrets can easily be exploited by threat actors and used to access sensitive information, impersonate your mobile app or make API calls on its behalf.
How to secure an API without authentication
Encryption — Having encryption enabled on the API and using https using TLS secures the channel as well as the information sent. Rate limiting and throttling — Limiting the number of requests coming into an API helps prevent abuse.
What is the disadvantage of using API
what is a disadvantages of using an api web-server interfaceSecurity Risks. When using an API web-server interface, businesses are exposing their data to potential security risks.Specialized Knowledge.Compatibility Issues.Costs.Maintenance.Time-Consuming.Limitations.Conclusion.
When should you not use API
Here are some reasons not to create a REST API for your system.It already has an API. Your system already has an API. And it is called HTTP.It Will Break. Your API will break.It Will Change. Ha!It Will Be Slow. Your API will be slow.It Will Be Hard To Parse. I am sure many of you parsed JSON documents. “
Can an API be exploited
API vulnerabilities can occur when an API is poorly designed or implemented or is not adequately secured. Hackers can also exploit API vulnerabilities to launch different attacks, such as denial-of-service attacks, or to gain access to confidential information.
What are the weaknesses of API
However, they also come with some drawbacks, such as security concerns, complexity, compatibility issues, dependency on third-party developers, and governance and management issues.
Is it legal to use an API
You can use Open API Services for any purposes in accordance with the Open Government Licence.
How do I secure my API over the internet
API security best practicesAuthenticate and authorize.Implement access control.Encrypt requests and responses.Validate the data.Assess your API risks.Share only necessary information.Choose your web services API.Record APIs in an API registry.
How are APIs monitored
How does API monitoring work An API monitor uses a remote computer to send requests to the API. The computer evaluates the API response for speed, content, and response codes. If anything about the response doesn't meet expectations, the monitoring service records an error.
What are API vulnerabilities
An API vulnerability is a type of security flaw that can allow attackers to gain access to PII and sensitive data or execute other malicious actions. API vulnerabilities can occur when an API is poorly designed or implemented or is not adequately secured.
What can an attacker do with API key
Given that the API key provides access to the API, and thus the data it represents, it should not be a surprise that hackers tend to be interested in stealing them. Getting ahold of an API key enables a malicious actor to breach data and systems fronted by the API.
Should you hide your API key
Do I need to hide my API keys API secret keys should never be put in a client-side code or should be hidden. However, read-only API keys won't pose any risk if you paste them into your JavaScript code that will commit in your browser.
Do all APIs need authentication
Most APIs require authentication to let you use the API. The Authentication & Authorization process allows APIs to verify your identity and decide what actions you can take using the API. In this article, I will go through four common ways of API authorization.
What is the simplest way to secure API
API security best practicesAuthenticate and authorize.Implement access control.Encrypt requests and responses.Validate the data.Assess your API risks.Share only necessary information.Choose your web services API.Record APIs in an API registry.
What are API threats
The most critical API security risks include: Broken object level, user- and function-level authorization, excessive data exposure, lack of resource, security misconfiguration, and insufficient logging and monitoring. The implications of these and other risks are huge.
What is the disadvantage of API
Complexity: APIs can be complex, requiring a significant amount of development effort to implement and maintain. Compatibility Issues: APIs can have compatibility issues between different versions of the same software system or between different systems, which can lead to errors and system failures.
How do you check if an API is being used
API testing flow is quite simple with three main steps:Send the request with necessary input data.Get the response having output data.Verify that the response returned as expected in the requirement.



