Do we have a way to monitor and detect security incidents continuously?
Do we have a way to monitor and detect security incidents continuously?
Summary
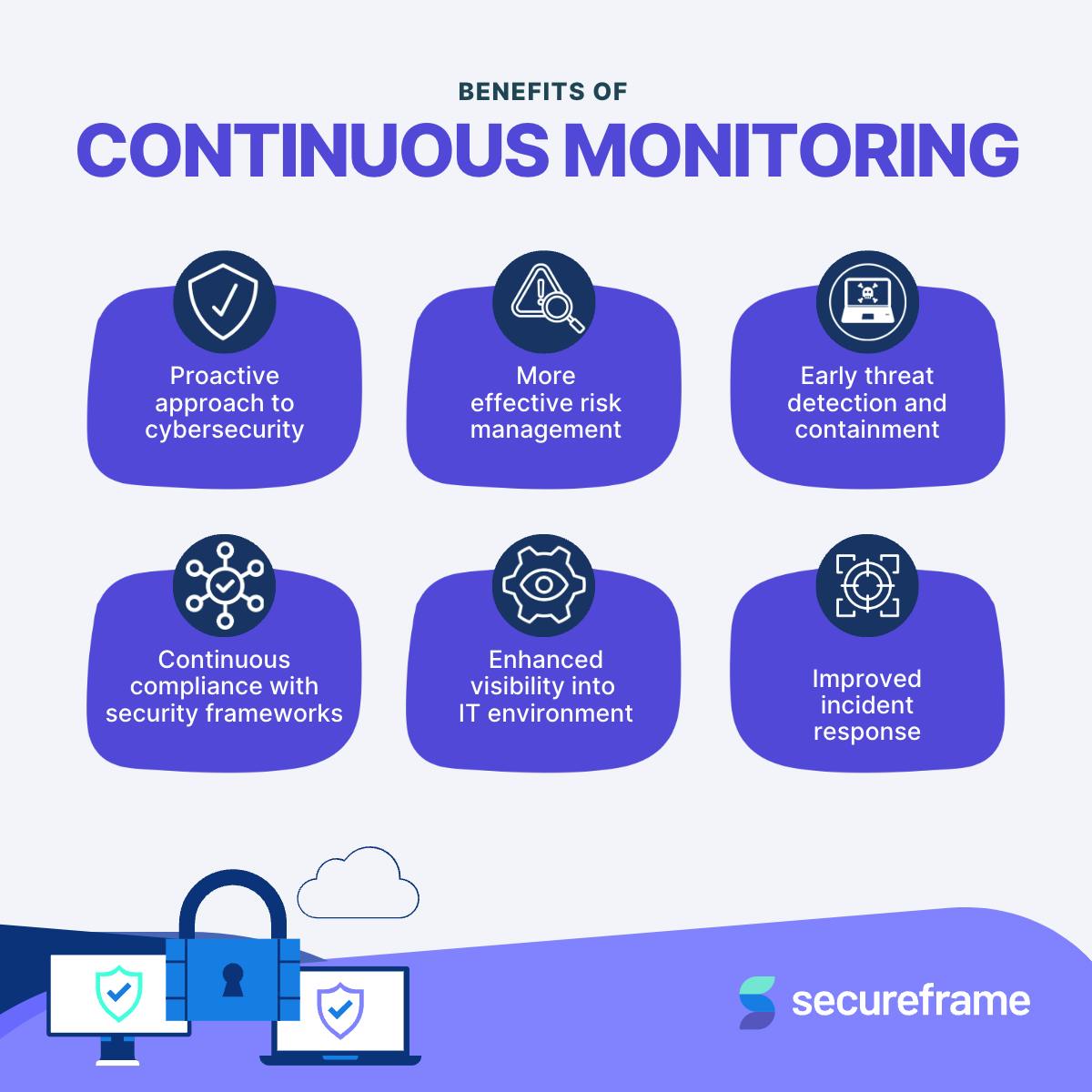
Continuous monitoring is an approach where an organization constantly monitors its IT systems and networks to detect security threats, performance issues, or non-compliance problems in an automated manner. The goal is to identify potential problems and threats in real time to address them quickly.
Key Points
- What is continuous monitoring in security?
- What is an example of continuous monitoring?
- How do you implement continuous monitoring?
- Why is continuous monitoring an important element of security?
- Which tool can be used for continuous monitoring?
- What is continuous process monitoring?
- What are the types of continuous monitoring?
- What are the steps in information security continuous monitoring?
- What are the basic principles for continuous monitoring?
- What are the three monitoring methods?
- Why do we perform continuous monitoring?
Continuous monitoring is an approach where an organization constantly monitors its IT systems and networks to detect security threats, performance issues, or non-compliance problems in an automated manner. The goal is to identify potential problems and threats in real time to address them quickly.
An example of continuous monitoring is when an organization monitors the network and system to detect malicious threats or non-compliance issues.
5 Tips to Get Continuous Monitoring Right:
– Involve all stakeholders in your continuous monitoring strategy.
– Identify your particular needs.
– Make sure all parties are on the same page.
– Choose the right tool for your needs.
– Don’t only use continuous monitoring.
When done correctly, continuous security monitoring provides real-time visibility into an organization’s IT environment. Here are the best practices for building a CSM program. Continuous security monitoring can help refine an organization’s threat detection and response.
AppDynamics is a continuous monitoring tool that supports infrastructure, network, and application monitoring of both cloud and on-premises computing environments.
Continuous monitoring is the process and technology used to detect compliance and risk issues associated with an organization’s financial and operational environment. The financial and operational environment consists of people, processes, and systems working together to support efficient and effective operations.
There are three main types of continuous monitoring: infrastructure, application, and network.
– Infrastructure monitoring: the process of monitoring the physical components of a system, such as servers, storage, and networking equipment.
– Application monitoring
– Network monitoring
A process to:
– Define an ISCM strategy
– Establish an ISCM program
– Implement an ISCM program
– Analyze data and Report findings
– Respond to findings
– Review and Update the ISCM strategy and program
Here are the primary objectives of CM:
– Increased visibility and transparency into network activity
– Reduction of cyber-attack risks by identifying suspicious network activity and timely alerting system
– Monitor the operational issues in the performance of the application
In the world of monitoring and evaluation (M&E) three approaches can be identified: result-oriented, constructivist and reflexive (see table p. 32). Every approach includes principles, methods and tools that can be used for projects that have the ambition to contribute to (system) innovation.
Continuous monitoring is performed to detect security incidents and threats in real time, allowing organizations to respond quickly and mitigate potential damage. It helps ensure the ongoing security and compliance of IT systems and networks.

What is continuous monitoring in security
Continuous monitoring is an approach where an organization constantly monitors its IT systems and networks to detect security threats, performance issues, or non-compliance problems in an automated manner. The goal is to identify potential problems and threats in real time to address them quickly.
Cached
What is an example of continuous monitoring
What is an example of continuous monitoring An example of continuous monitoring is when an organization monitors the network and system to detect malicious threats or non-compliance issues.
How do you implement continuous monitoring
5 Tips to Get Continuous Monitoring RightInvolve all stakeholders in your continuous monitoring strategy.Identify your particular needs.Make sure all parties are on the same page.Choose the right tool for your needs.Don't only use continuous monitoring.
Why is continuous monitoring an important element of security
When done correctly, continuous security monitoring provides real-time visibility into an organization's IT environment. Here are the best practices for building a CSM program. Continuous security monitoring can help refine an organization's threat detection and response.
Which tool can be used for continuous monitoring
AppDynamics is a continuous monitoring tool that supports infrastructure, network, and application monitoring of both cloud and on-premises computing environments.
What is continuous process monitoring
Continuous monitoring is the process and technology used to detect compliance and risk issues associated with an organization's financial and operational environment. The financial and operational environment consists of people, processes, and systems working together to support efficient and effective operations.
What are the types of continuous monitoring
There are three main types of continuous monitoring: infrastructure, application, and network.Infrastructure monitoring. Infrastructure monitoring is the process of monitoring the physical components of a system, such as servers, storage, and networking equipment.Application monitoring.Network monitoring.
What are the steps in information security continuous monitoring
A process to: • Define an ISCM strategy; • Establish an ISCM program; • Implement an ISCM program; • Analyze data and Report findings; • Respond to findings; and • Review and Update the ISCM strategy and program.
What are the basic principles for continuous monitoring
Here are the primary objectives of CM. Increased visibility and transparency into network activity. Reduction of cyber-attack risks by identifying suspicious network activity and timely alerting system. Monitor the operational issues in the performance of the application.
What are the three monitoring methods
In the world of monitoring and evaluation (M&E) three approaches can be identified: result-oriented, constructivist and reflexive (see table p. 32). Every approach includes principles, methods and tools that can be used for projects that have the ambition to contribute to (system) innovation.
Why do we perform continuous monitoring
The goal of continuous monitoring is to provide IT organizations with near-immediate feedback and insight into performance and interactions across the network, which helps drive operational, security, and business performance.
What are the four types of continuous process control
What are the types of continuous process controlRegulatory control.Feed forward control.Steady state optimization.Adaptive control.
What are the 4 types of monitoring
Four basic types of monitoring can be readily distinguished by the nature of questions that the particular monitoring effort is designed to address—(1) surveillance monitoring, (2) implementation monitoring, (3) effectiveness monitoring, and (4) ecological effects monitoring (Table 1).
What is the primary purpose for continuous monitoring of security controls ensure
The goal of continuous monitoring and the reason that organizations implement continuous monitoring software solutions is to increase the visibility and transparency of network activity, especially suspicious network activity that could indicate a security breach, and to mitigate the risk of cyber attacks with a timely …
What is the principle of continuous monitoring
Continuous monitoring enables management to continually review business processes for adherence to and deviations from their intended levels of performance and effectiveness. Continuous auditing enables internal audit to continually gather from processes data that supports auditing activities.
What are the steps of information security continuous monitoring
A process to: • Define an ISCM strategy; • Establish an ISCM program; • Implement an ISCM program; • Analyze data and Report findings; • Respond to findings; and • Review and Update the ISCM strategy and program.
What are the four 4 types of monitoring indicators
According to this typology, there are four types of indicators: input, output, outcome and impact.
What is an example of a continuous process control system
A continuous physical system is represented through variables that are smooth and uninterrupted in time. The control of the water temperature in a heating jacket, for example, is an example of continuous process control. Some important continuous processes are the production of fuels, chemicals and plastics.
What is a continuous control process
Continuous Controls Monitoring (CCM) is a set of technologies that automate processes to reduce business losses and increase operating effectiveness through continuous monitoring of business functions.
What are 7 types of monitoring
7 types of monitoring to get you startedProcess monitoring. This is often referred to as 'activity monitoring.Compliance monitoring.Context monitoring.Beneficiary monitoring.Financial monitoring.Organisational monitoring.Results monitoring.
What are the three common monitoring methods
In the world of monitoring and evaluation (M&E) three approaches can be identified: result-oriented, constructivist and reflexive (see table p.
Why is continuous monitoring of controls important choose the best answer
The fundamental advantage of continuous control monitoring is that it automates anomaly detection and directs it to appropriate business users. It saves auditors time on follow-up, resulting in cost and time savings.
What are the 7 types of monitoring
7 types of monitoring to get you startedProcess monitoring. This is often referred to as 'activity monitoring.Compliance monitoring.Context monitoring.Beneficiary monitoring.Financial monitoring.Organisational monitoring.Results monitoring.
What are continuous process types examples
Some common continuous processes are the following:Oil refining.Chemicals.Synthetic fibers.Fertilizers.Pulp and paper.Blast furnace (iron)Metal smelting.Power stations.
What are types of continuous processing
What is a continuous process The continuous process moves raw material from the start of the process through each production step to a final product. Rather than waiting until the unit of product is complete, raw material is fed and processed continuously to produce additional units of product.



