How do DoS attacks happen?
Unfortunately, the provided text does not follow the requested format. However, I can help you format the content in the desired way. Here’s an example of how it can be structured:
Summary of the Article
DoS attacks occur when a targeted machine is overwhelmed with requests, resulting in denial-of-service for other users. These attacks can be intentional or unintentional, and they are typically stopped by rerouting traffic, adding firewalls, and strengthening network security. High-profile organizations, such as banking and media companies, are often targeted by DoS attacks. Preventive measures include IP blocking and rate limiting. The likelihood of a DoS attack varies across industries, with telecommunications and financial services being particularly vulnerable. Using a VPN can help protect against DoS attacks. The duration of these attacks can vary, with the average recorded attack lasting around 10 minutes. Tracing DoS attacks can be challenging due to their distributed nature, but cybersecurity tools can help in identification. DoS attacks are relatively common, and organizations face an average of 29.3 attacks per day globally.
Questions and Answers
- How does a DoS attack occur?
A DoS attack occurs when a targeted machine is flooded with requests, overwhelming its capacity to process normal traffic. - Can a DoS attack be produced unintentionally?
Yes, unintentional DoS attacks can occur when servicing low-bandwidth areas, such as streaming content to regions with slow internet connections. - How are DoS attacks stopped?
DoS attacks can be stopped by rerouting traffic through firewalls, adding device firewalls, imposing stronger rate limits, and enhancing network security. - Who are DoS attacks targeted at?
DoS attacks target high-profile organizations such as banking, commerce, media companies, government organizations, and trade organizations. - Can you prevent a DoS attack?
Yes, preventive measures for DoS attacks include IP blocking and rate limiting to prevent malicious traffic from overwhelming a server or resource. - Who is typically targeted in a DoS attack?
High-profile organizations, particularly those in the banking, commerce, media, government, and trade sectors, are often targeted in DoS attacks. - What is the likelihood of a DoS attack?
According to statistics, about 20% of companies with 50 or more employees have experienced at least one DoS or DDoS attack. The likelihood varies across industries, with telecommunications and financial services having higher chances of being targeted. - Will a VPN stop DoS attacks?
Generally, using a VPN can help prevent DDoS attacks by hiding the network’s IP address and making it harder for attackers to target it. - How long does a DDoS attack last?
DDoS attacks can vary in duration, ranging from short-term actions of a few minutes to longer strikes that last over an hour. The average duration of documented attacks is around 10 minutes. - Can DoS attacks be traced?
Tracing DoS attacks can be challenging due to their distributed nature and the efforts of attackers to remain unidentified. However, cybersecurity tools can assist in identifying such attacks by analyzing traffic patterns. - How common are DoS attacks?
DoS attacks are relatively common, with global organizations facing an average of 29.3 attacks per day during the fourth quarter of [insert relevant year].
Note: This is just a sample structure, and the answers provided above are placeholders. You should replace them with accurate information or content from the actual article.
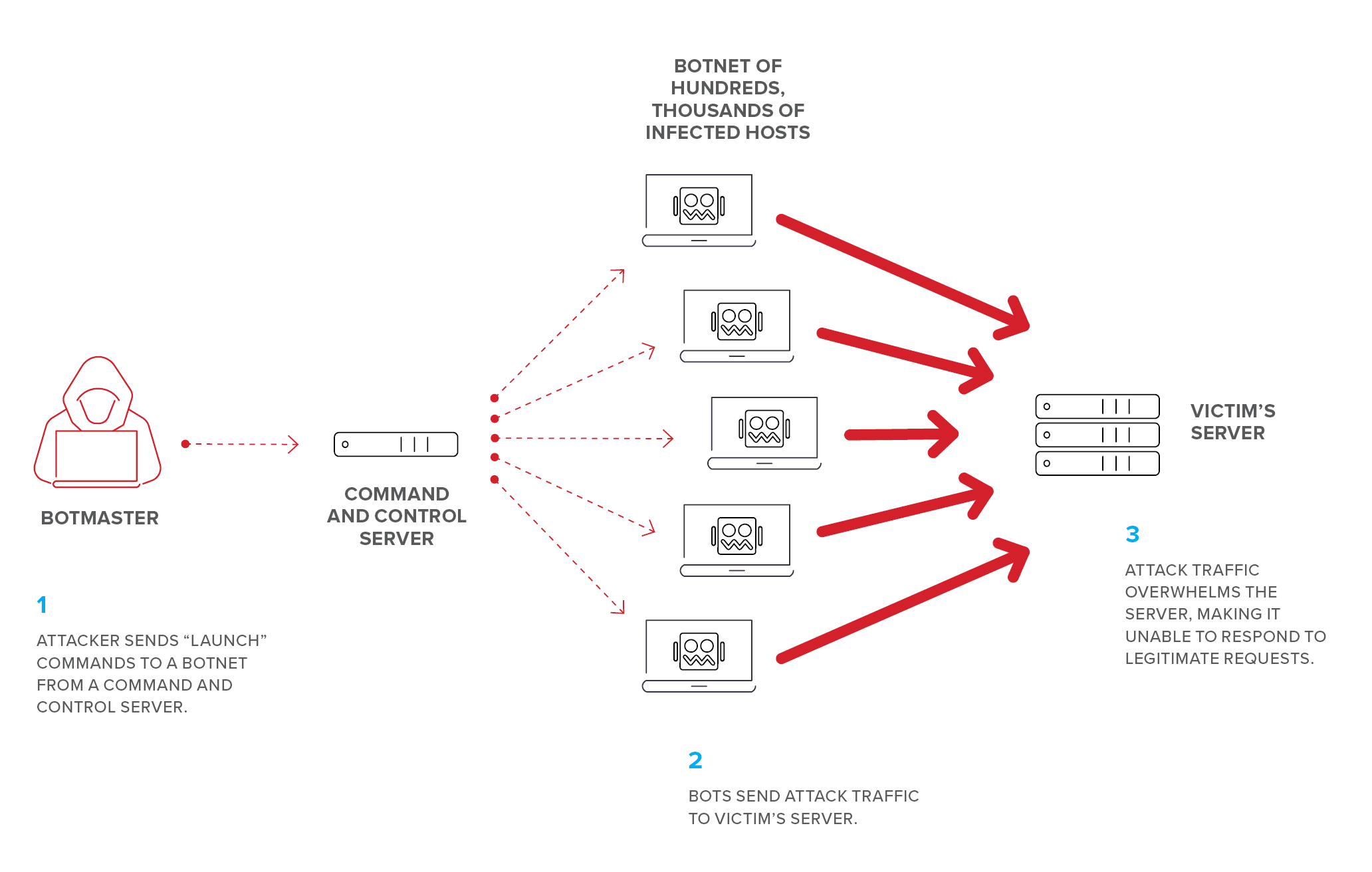
How does DoS attack occur
DoS attacks typically function by overwhelming or flooding a targeted machine with requests until normal traffic is unable to be processed, resulting in denial-of-service to addition users. A DoS attack is characterized by using a single computer to launch the attack.
Can DoS attack be produced unintentionally
Another type of unintentional DoS attack can occur when servicing low bandwidth areas. For instance, streaming content internationally means that people in certain areas of the world with slow or bad internet connections might cause problems.
How are DoS attacks stopped
Reroute traffic through firewalls or add device firewalls to block attacks. Apply stronger rate limits to firewalls, servers, and other resources protecting and servicing the router or server. Add or strengthen network security products, network intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Cached
Who are DoS attacks targeted at
In both instances, the DoS attack deprives legitimate users (i.e. employees, members, or account holders) of the service or resource they expected. Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations.
Can you prevent a DoS attack
IP blocking – Blocking traffic from known or suspected malicious sources can prevent DoS traffic from reaching its target. Rate limiting – Limiting the rate of traffic to reach a server or resource can prevent a DoS attack from overwhelming it.
Who is typically targeted in a DoS attack
Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations.
What is the likelihood of a DoS attack
20% of companies with 50 or more employees admitted to at least one DoS or DDoS attack. This proportion varies from industry to industry, and those with the highest chances of being hit with such an attack are telecommunications companies (24%) and financial services organizations (22%).
Will a VPN stop DoS attacks
Generally speaking, yes, VPNs can stop DDoS attacks. A primary benefit of a VPN is that it hides IP addresses. With a hidden IP address, DDoS attacks can't locate your network, making it much harder to target you.
How long does a DDoS last
This type of sporadic attack can vary in length, from short-term actions that last for a few minutes to longer strikes that exceed an hour. According to the DDoS Threat Landscape Report 2021 from Swedish telecom Telia Carrier, documented attacks average a 10-minute duration.
Can DoS attacks be traced
DDoS attacks are pretty difficult to trace because most of them are distributed over hundreds and thousands of other devices. Also, those who initiate such attacks usually make an effort not to be found. It's possible to identify DDoS attacks when they happen by using certain cybersecurity tools to analyze the traffic.
How common are DoS attacks
Attack frequency: The frequency of DDoS attacks also saw a significant and concerning uptick. Globally, organizations mitigated an average of 29.3 attacks per day during the fourth quarter of 2022, 3.5 times more compared to 8.4 attacks per day at the end of 2021.
Who is usually targeted by a DoS attack
Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations.
Are DoS attacks traceable
DDoS attacks are pretty difficult to trace because most of them are distributed over hundreds and thousands of other devices. Also, those who initiate such attacks usually make an effort not to be found. It's possible to identify DDoS attacks when they happen by using certain cybersecurity tools to analyze the traffic.
How quickly can a DoS attack be resolved
However, a DoS attack can cause a significant loss of time and resources to the targeted service since it can last anywhere between a few hours and several months.
What is the best defense against a DoS attack
A Web Application Firewall (WAF) is the best defense against all DDoS attacks. It thwarts malicious traffic trying to block vulnerabilities in the application.
Does resetting your router stop a DDoS
Does changing your IP stop DDoS attacks No, if you are already under a DDoS attack, resetting your IP address won't help much. However, resetting your IP address every few days is a good habit to develop if you've been the target of multiple DDoS attacks, or if you're a streamer or a highly visible gamer.
Can DDoS shut down Internet
DDoS attacks happen when a significant information overload hits a targeted server, website, or network service. If the attack successfully overloads the target, then the impact effectively shuts down a website, takes a network offline, or makes access to anything on the internet exceedingly slow or even impossible.
Is DDoS threat illegal
Participating in Distributed Denial of Service attacks (DDoS) and DDoS-for-hire services is illegal. The FBI and other law enforcement agencies investigate DDoS attacks as cyber crimes.
How illegal is DDoS
DDoSing is an Illegal cybercrime in the United States. A DDoS attack could be classified as a federal criminal offense under the Computer Fraud and Abuse Act (CFAA). The use of booter services and stressers also violates this act.
How do I know if I got DDoS attacked
Simple signs of a DDoS attackSlow or unresponsive website.Files, images, content and videos load slower than normal.Slow or unresponsive servers that display “Too many connections” or “503” errors.Irregular or abnormal traffic patterns, including spikes for no apparent reason.
What is most likely to detect a DoS attack
The best way to detect and identify a DoS attack would be via network traffic monitoring and analysis. Network traffic can be monitored via a firewall or intrusion detection system.
Does the FBI investigate DDoS attacks
Participating in Distributed Denial of Service attacks (DDoS) and DDoS-for-hire services is illegal. The FBI and other law enforcement agencies investigate DDoS attacks as cyber crimes.
How long does a DDoS usually last
Depending on the severity of the attack, DDoS attacks can last up to a day or more. But with robust planning and good security partners, you can usually manage small to mid-sized attacks in a matter of hours or minutes.
How long will a DDoS last
DDoS attacks can exploit security vulnerabilities and target any endpoint that is reachable, publicly, through the internet. Denial-of-service attacks can last hours, or even days.
What can someone do if they DDoS you
In a DoS or DDoS attack, an attacker floods the IP address of the targeted device (such as a console or a computer) with superfluous communication requests. These requests can overload a system and create a jam that blocks network connections on the targeted device.



