How do I know if a password is hashed?
Summary of Article on Hashed Passwords
What does a hashed password look like
Instead, they just get access to the encrypted “hash” created by your password. A common hash function is md5(), which returns a 32-character string from any input. Below are a few examples of what a hash looks like: md5(helloworld) = fc5e038d38a57032085441e7fe7010b0.
Cached
What verifies that a password matches a hash
To do this, we call check() on the Hash façade. The check() method verifies if the plain-text string entered by the user matches the given hash. The code above uses the Hash facade alongside the check() method.
Cached
How do hackers find hashed passwords
A criminal could use a dictionary attack to run popular and predictable passwords through commonly used hashing algorithms. Instead, an attacker will often use a dictionary attack to crack leaked passwords that have been hashed.
What type of password is hashed
A password hashing algorithm uses a salt, which is unique (not used for any other user or in anybody else’s database). The salt is necessary so that attackers can’t just pre-calculate the hashes of common passwords: with a salt, they have to restart the calculation for every account.
What is the most common password hash
It’s 123456, as hashed using a cryptographic protocol called MD5. The fact we know this hash corresponds to the world’s most commonly used password should not be comforting, and it isn’t, because MD5 has been cracked – the equivalent of thieves in heist films knowing exactly how to break open a safe.
Can you Unhash a password
You can’t “unhash” or “dehash” passwords. You can’t “reverse” or “invert” MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can’t “decode” passwords, “decrypt” password hashes or “reverse” or “unscramble” password hashes at all. There’s no such thing as “hash decryption”.
Can hash password be decrypted
Instead, passwords are “hashed”, or transformed with a one-way function. The result of the transformation, if one is performed correctly, cannot be reversed, and the original password cannot be “decrypted” from the result of a hash function.
Can a hashed password be unhashed
You can’t “reverse” password hashes. You can’t “unhash” or “dehash” passwords. You can’t “reverse” or “invert” MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can’t “decode” passwords, “decrypt” password hashes or “reverse” or “unscramble” password hashes at all.
Is it possible to retrieve a password from a hashed password
At first glance, hashing might look similar to encryption but hashing is a one-way function while encryption is a two-way function. In other words, you cannot revert a hashed password, also known as a hash, back to its original plain-text value while it is possible to do that with encrypted values.
What is the most common password hashing
To protect passwords, experts suggest using a strong and slow hashing algorithm like Argon2 or Bcrypt, combined with salt (or even better, with salt and pepper). (Basically, avoid faster algorithms for this usage.) To verify file signatures and certificates, SHA-256 is among your best hashing algorithm choices.
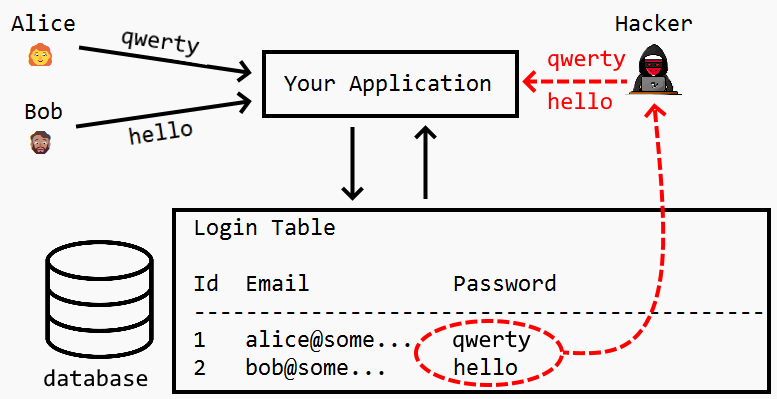
What does a hashed password look like
Instead, they just get access to the encrypted “hash” created by your password. A common hash function is md5(), which returns a 32-character string from any input. Below are a few examples of what a hash looks like: md5(helloworld) = fc5e038d38a57032085441e7fe7010b0.
Cached
What verifies that a password matches a hash
To do this, we call check() on the Hash façade. The check() method verifies if the plain-text string entered by the user matches the given hash. The code above uses the Hash facade alongside the check() method.
Cached
How do hackers find hashed passwords
A criminal could use a dictionary attack to run popular and predictable passwords through commonly used hashing algorithms. Instead, an attacker will often use a dictionary attack to crack leaked passwords that have been hashed.
What type of password is hashed
A password hashing algorithm uses a salt, which is unique (not used for any other user or in anybody else's database). The salt is necessary so that attackers can't just pre-calculate the hashes of common passwords: with a salt, they have to restart the calculation for every account.
What is the most common password hash
It's 123456, as hashed using a cryptographic protocol called MD5. The fact we know this hash corresponds to the world's most commonly used password should not be comforting, and it isn't, because MD5 has been cracked – the equivalent of thieves in heist films knowing exactly how to break open a safe.
Can you Unhash a password
You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all. There's no such thing as "hash decryption".
Can hash password be decrypted
Instead, passwords are “hashed”, or transformed with a one-way function. The result of the transformation, if one is performed correctly, cannot be reversed, and the original password cannot be “decrypted” from the result of a hash function.
Can a hashed password be unhashed
You can't "reverse" password hashes. You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all.
Is it possible to retrieve a password from a hashed password
At first glance, hashing might look similar to encryption but hashing is a one-way function while encryption is a two-way function. In other words, you cannot revert a hashed password, also known as a hash, back to its original plain-text value while it is possible to do that with encrypted values.
What is the most common password hashing
To protect passwords, experts suggest using a strong and slow hashing algorithm like Argon2 or Bcrypt, combined with salt (or even better, with salt and pepper). (Basically, avoid faster algorithms for this usage.) To verify file signatures and certificates, SHA-256 is among your best hashing algorithm choices.
Can you crack a password hash
Hashcat is a powerful tool that helps to crack password hashes. Hashcat supports most hashing algorithms and can work with a variety of attack modes. To enforce security and protect hashes from attacks, use strong passwords and salts before hashing passwords.
What are the common hash examples
Some common hashing algorithms include MD5, SHA-1, SHA-2, NTLM, and LANMAN.
Can a hashed password be decrypted
Instead, passwords are “hashed”, or transformed with a one-way function. The result of the transformation, if one is performed correctly, cannot be reversed, and the original password cannot be “decrypted” from the result of a hash function.
Can a hacker decrypt hash
By using specific attack strategies, hackers may access to this hashed password. In this article, I will give you 5 examples of how hackers can get hashed passwords. They will then use techniques like brute-force or a rainbow table to decrypt the weaker passwords in the database.
Is it possible to Unhash
The principle of hashing is not to be reversible, there is no decryption algorithm, that's why it is used for storing passwords: it is stored encrypted and not unhashable.
Is hashing a password the same as encryption
Hashing is not a type of encryption — it's a form of cryptographic security. Encryption works both ways, while hashing is a one-way function. Hashing boils down the original to a fixed set of characters. This is not the case with encrypted messages.
What is the difference between hashed and encrypted password
Encryption is often used for storing passwords in password managers. Password hashing is useful on the server side when server operators don't need to know the plaintext, only that the user knows the plaintext. Hashing is a one-way process that converts a password to ciphertext using hash algorithms.
Can sha256 be unhashed
SHA-256 is a cryptographic (one-way) hash function, so there is no direct way to decode it. The entire purpose of a cryptographic hash function is that you can't undo it.
Can you brute force a hashed password
Brute force is also used to crack the hash and guess a password from a given hash. In this, the hash is generated from random passwords and then this hash is matched with a target hash until the attacker finds the correct one.
Can hashed passwords be decrypted
Instead, passwords are “hashed”, or transformed with a one-way function. The result of the transformation, if one is performed correctly, cannot be reversed, and the original password cannot be “decrypted” from the result of a hash function.
What is the difference between hash and encryption passwords
Encryption is often used for storing passwords in password managers. Password hashing is useful on the server side when server operators don't need to know the plaintext, only that the user knows the plaintext. Hashing is a one-way process that converts a password to ciphertext using hash algorithms.
What is simple example of hashing
Hashing is an important data structure designed to solve the problem of efficiently finding and storing data in an array. For example, if you have a list of 20000 numbers, and you have given a number to search in that list- you will scan each number in the list until you find a match.
Can two passwords have same hash
The probability that two users with the same password would get identical hashes is negligible; The probability that two users with different passwords will get salts that produce identical hash results is also negligible.
Can hashing be undone
Technically, hashing can be reversed, but the computational power needed to decrypt it makes decryption infeasible. The way hashing works is with a hashing algorithm. This algorithm is most effective when it collision resistant.
Can password hash be reversed
You can't "reverse" password hashes. You can't "unhash" or "dehash" passwords. You can't "reverse" or "invert" MD5, SHA256, bcrypt, SHA1, or similar hashes, salted or unsalted. You (usually) can't "decode" passwords, "decrypt" password hashes or "reverse" or "unscramble" password hashes at all.



