What are the 3 main security purposes of TLS?
Article Summary: The Main Functions and Security of TLS
What are the main functions of TLS?
Transport Layer Security (TLS) encrypts data sent over the Internet to ensure that eavesdroppers and hackers are unable to
see what you transmit, which is particularly useful for private and sensitive information such as passwords, credit card
numbers, and personal correspondence.
What are three different
applications of TLS?
A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers
loading a website. TLS can also be used to encrypt other communications such as email, messaging, and voice over IP (VoIP).
What security does TLS provide?
Transport Layer Security (TLS) is a protocol that provides security for digital communications between two parties. When
a server and client communicate, well-configured TLS ensures that no third party can eavesdrop or tamper with any message.
What are the three essential
services TLS protocol is designed to provide to all applications running above it?
Encryption, authentication, and data integrity. The TLS protocol is designed to provide three essential services to all
applications running above it: encryption, authentication, and data integrity.
What are the two main protocols
of TLS?
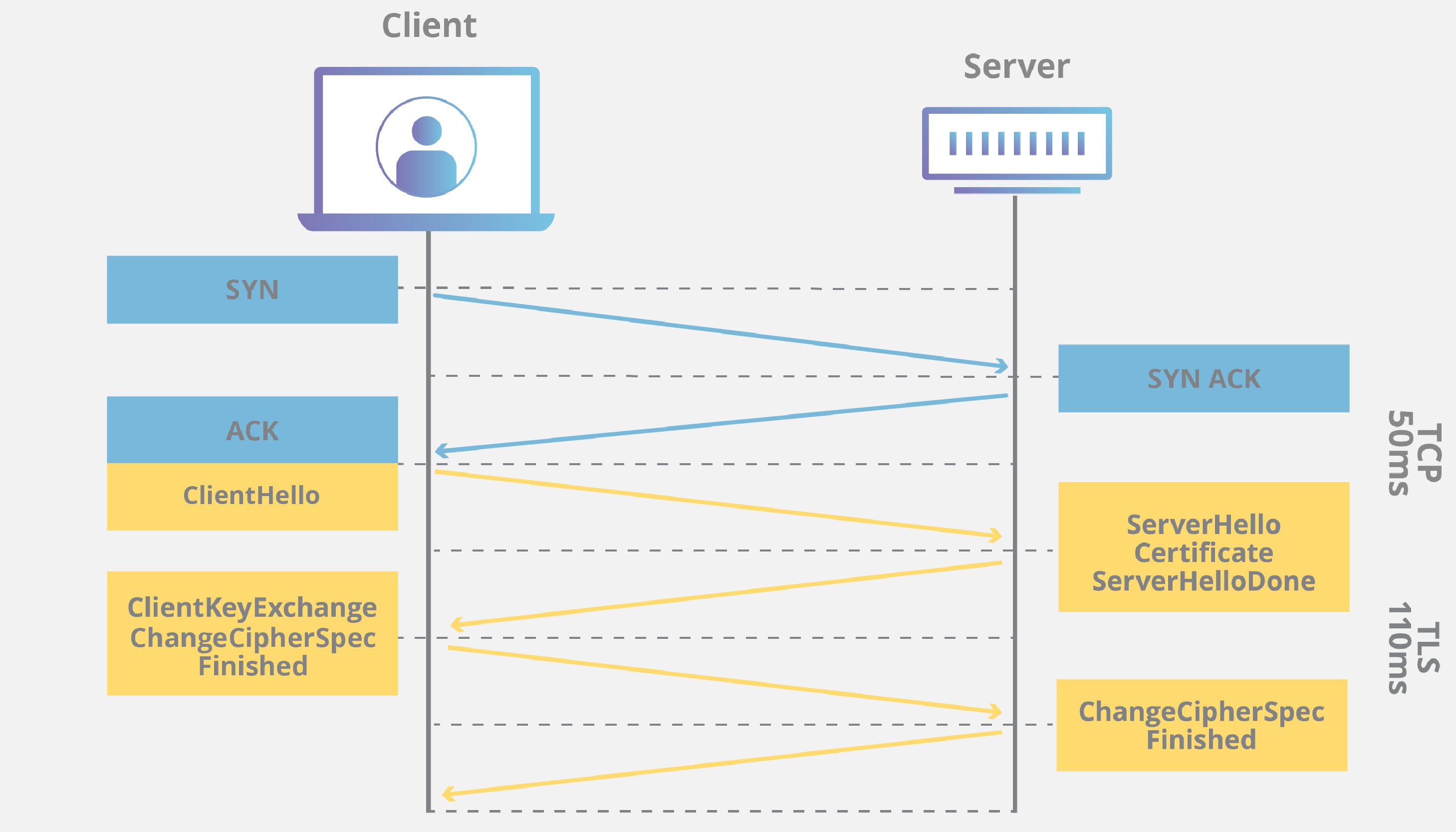
According to the protocol specification, TLS is composed of two layers: the TLS record protocol and the TLS handshake protocol.
What are the different types of
TLS?
There are three types of TLS certificates: Domain Validation (DV), Organization Validation (OV), and Extended Validation (EV).
What is the most used TLS?
The Latest TLS Versions in Use:
TLS Version 1.2. Based on TLS 1.1, TLS 1.2 was released by the IETF in 2008 with the RFC-5246. To date, it’s the most commonly used TLS protocol version. TLS Version 1.3. This is the most recent TLS protocol version.
What does TLS security stand for?
Transport Layer Security (TLS). TLS is an updated, more secure version of SSL.
What security features does TLS
1.2 provide?
Benefits:
– Encrypt data communication between server and client.
– Information and data are secured.
– Prevent vulnerable access points from cyber attackers.
– Third parties do not have access to data.
What are the three application
layer protocols?
Application Layer Protocols:
– The SMTP (Simple Mail Transfer Protocol) is the TCP/IP protocol that handles email.
– The FTP (File Transfer Protocol) is a standard internet protocol for transferring data from one computer to another.
– The TFTP (Trivial File Transfer Protocol) is a simple file transfer protocol.
How does TLS protect data?
SSL/TLS uses both asymmetric and symmetric encryption to protect the confidentiality and integrity of data-in-transit.
Asymmetric encryption is used to establish a secure session between a client and a server, and symmetric encryption is used
to exchange data within the secured session.
What two aspects of TLS provide
security in any network?
TLS uses both symmetric and asymmetric encryption to protect data during transmission and prevent unauthorized access or
modification of data.
What are the main functions of TLS
Transport Layer Security (TLS) encrypts data sent over the Internet to ensure that eavesdroppers and hackers are unable to see what you transmit which is particularly useful for private and sensitive information such as passwords, credit card numbers, and personal correspondence.
Cached
What are three different applications of TLS
A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website. TLS can also be used to encrypt other communications such as email, messaging, and voice over IP (VoIP).
What security does TLS provide
Transport Layer Security (TLS) is a protocol that provides security for digital communications between two parties. When a server and client communicate, well-configured TLS ensures that no third party can eavesdrop or tamper with any message.
What are the three essential services TLS protocol is designed to provide to all applications running above it
encryption, authentication, and data integrity
The TLS protocol is designed to provide three essential services to all applications running above it: encryption, authentication, and data integrity.
CachedSimilar
What are the two main protocols of TLS
According to the protocol specification, TLS is composed of two layers: the TLS record protocol and the TLS handshake protocol.
What are the different types of TLS
There are three types of TLS certificates: Domain Validation (DV), Organization Validation (OV) and Extended Validation (EV).
What is the most used TLS
The Latest TLS Versions in UseTLS Version 1.2. Based on TLS 1.1, TLS 1.2 was released by the IETF in 2008 with the RFC-5246. To date, it's the most commonly used TLS protocol version.TLS Version 1.3. This is the most recent TLS protocol version.
What does TLS security stand for
Transport Layer Security
TLS: Transport Layer Security
TLS is an updated, more secure version of SSL.
What security features does TLS 1.2 provide
BenefitsEncrypt data communication between server and client.Information and data is secured.Prevent vulnerable access points from cyber attackers.Third parties do not have access to data.
What are the three application layer protocols
Application Layer ProtocolsThe SMTP (Simple Mail Transfer Protocol) is the TCP/IP protocol that handles email.The FTP (File Transfer Protocol) is a standard internet protocol for transferring data from one computer to another.The TFTP (Trivial File Transfer Protocol) is a simple file transfer protocol.
How does TLS protect data
SSL/TLS uses both asymmetric and symmetric encryption to protect the confidentiality and integrity of data-in-transit. Asymmetric encryption is used to establish a secure session between a client and a server, and symmetric encryption is used to exchange data within the secured session.
What two aspects of TLS provide security in any network
TLS uses both symmetric encryption and public key encryption for securely sending private data, and adds additional security features, such as authentication and message tampering detection.
How is TLS more secure
While SSL provides keyed message authentication, TLS uses the more secure Key-Hashing for Message Authentication Code (HMAC) to ensure that a record cannot be altered during transmission over an open network such as the Internet.
How does TLS authentication work
How TLS provides authentication. For server authentication, the client uses the server's public key to encrypt the data that is used to compute the secret key. The server can generate the secret key only if it can decrypt that data with the correct private key.
Is TLS authentication or authorization
The Transport Layer Security (TLS) is a protocol designed to provide secure communication over the Internet and includes authentication, confidentiality and integrity. When a TLS connection is established the server provides a certificate that the client validates before trusting the server's identity.
Is TLS 1.2 a security risk
While TLS 1.2 can still be used, it is considered safe only when weak ciphers and algorithms are removed. On the other hand, TLS 1.3 is new; it supports modern encryption, comes with no known vulnerabilities, and also improves performance.
What is the difference between TLS 1.2 and TLS 1
Performance. TLS 1.2 is faster than TLS 1.1 due to several improvements in the protocol. TLS 1.2 reduces the number of round trips required during the handshake process, which reduces latency and improves performance. In addition, TLS 1.2 uses more efficient cipher suites, which also contribute to better performance.
What is the most important layer 3 security protocol
The most significant protocol at layer 3 (also called the network layer) is the Internet Protocol, or IP. IP is the standard for routing packets across interconnected networks–hence, the name internet. It is an encapsulating protocol similar to the way Ethernet is an encapsulating protocol.
What are the most common layer 3 protocols
The protocols used in Layer 3 include:Internet Protocols IPv4/v6.Internet Control Message Protocol (ICMP)Distance Vector Multicast Routing Protocol (DVMRP)Internet Group Management Protocol (IGMP)Address Resolution Protocol (ARP)Internet Protocol Security (IPsec)Routing Information Protocol (RIP)
How does TLS protect integrity
TLS provides data integrity by calculating a message digest. For more information, refer to Data integrity of messages. Use of TLS does ensure data integrity, provided that the CipherSpec in your channel definition uses a hash algorithm as described in the table in Enabling CipherSpecs.
Does TLS protect data at rest
TLS does not offer any of these security benefits to data that is at rest. Transport layer protection is necessary for back-end connections and any other connection where sensitive data is exchanged or where user identity is established.
What are the 3 aspects of security in network security
An effective system satisfies all three components: confidentiality, integrity, and availability. An information security system that is lacking in one of the three aspects of the CIA triad is insufficient.
Which TLS encryption is most secure
One of the key reasons why TLS 1.3 is considered more secure than any of its predecessors is because of how it approaches forward secrecy, an encryption implementation method. Although forward secrecy was possible in older TLS versions, it was only optional. But with TLS 1.3, forward secrecy is mandatory.
What are the different types of TLS authentication
There are three types of TLS certificates: Domain Validation (DV), Organization Validation (OV) and Extended Validation (EV).
How does TLS communicate between client and server
The TLS server sends the client a finished message, which is encrypted with the secret key, indicating that the server part of the handshake is complete. For the duration of the TLS session, the server and client can now exchange messages that are symmetrically encrypted with the shared secret key.



