What are the Linux tools?
The Linux tools are essential for sysadmins to effectively manage and administer Linux servers. Here are 10 key Linux tools that every sysadmin should know:
1. Zenmap: Used to discover network-related issues and vulnerabilities.
2. Webmin: A web-based interface for administering all aspects of a Linux server.
3. Cockpit: Provides a user-friendly interface for managing Linux servers.
4. gping: A tool for measuring ping latency to multiple hosts simultaneously.
5. Shorewall: A firewall tool for configuring and managing network security policies.
6. Nagios: A monitoring tool for checking the health and performance of servers and network devices.
7. phpMyAdmin: A web-based tool for managing MySQL databases.
8. Puppet: A configuration management tool for automating server setup and maintenance.
Linux systems consist of three main components: the kernel, the shell, and the programs. The kernel is the core of the operating system that manages resources, communicates with hardware, and provides essential services. The shell is the command-line interface that allows users to interact with the system and run commands. Programs are the applications and services that users run on top of the operating system.
Kali Linux is a popular Linux distribution specifically designed for cybersecurity professionals, ethical hackers, and penetration testers. It provides over 600 tools for penetration testing and security auditing, making it a comprehensive platform for testing and securing systems.
There are well over 100 Unix commands shared by the Linux kernel and other Unix-like operating systems. Linux sysadmins and power users often use a subset of these commands that are frequently used for system administration tasks, scripting, and automation.
Linux distributions come in various flavors, each with its own set of features and characteristics. Some popular examples include Debian, Fedora Linux, and Ubuntu. Commercial distributions like Red Hat Enterprise Linux and SUSE Linux Enterprise are also widely used in enterprise environments.
Linux is an operating system, not just a software or tool. It is an open-source OS that manages a system’s hardware and resources, providing the framework for running applications and services. The OS acts as a bridge between software and hardware, managing the interactions and ensuring the system functions smoothly.
Linux has five basic components in its architecture: the kernel, hardware layer, system library, shell, and system utility. The kernel is the core of the OS, interacting directly with the hardware. The hardware layer consists of the physical components of the system. The system library provides essential functions and libraries for software development. The shell provides the command-line interface, allowing users to interact with the system. System utilities are the additional tools and applications that aid in system administration tasks.
In Linux, every project begins by obtaining, customizing, and deploying four essential elements: the toolchain, the bootloader, the kernel, and the root filesystem. The toolchain includes the necessary compilers and libraries for building software. The bootloader is responsible for starting the system. The kernel is the core of the operating system. The root filesystem contains essential files and directories needed for booting and running the system.
Kali Linux offers a wide range of tools for hacking and cybersecurity purposes. Some of the top 10 tools in Kali Linux are:
1. Wireshark: A network traffic analyzer.
2. Metasploit Framework: A powerful tool for penetration testing and exploiting vulnerabilities.
3. Aircrack-ng: A set of tools for testing and cracking wireless network security.
4. Netcat: A versatile networking utility for port scanning, file transfer, and more.
5. John the Ripper: A password-cracking tool for recovering lost or forgotten passwords.
6. sqlmap: A tool for detecting and exploiting SQL injection vulnerabilities.
7. Autopsy: A digital forensics platform for analyzing and investigating computer systems.
8. Social Engineering Toolkit: A collection of tools for performing social engineering attacks.
Kali Linux is favored by hackers due to its comprehensive collection of tools that can be used for both offensive and defensive purposes. It allows hackers to identify and potentially exploit security vulnerabilities, while security administrators can use it to prevent and detect breaches.
The most used command in Linux varies depending on the context and user’s requirements. However, some commonly used commands include:
1. ls: Lists files and directories.
2. pwd: Prints the current working directory.
3. cd: Changes the current directory.
4. mkdir: Creates a new directory.
5. mv: Moves or renames files and directories.
These commands are essential for navigating the file system and performing basic file management tasks in Linux.
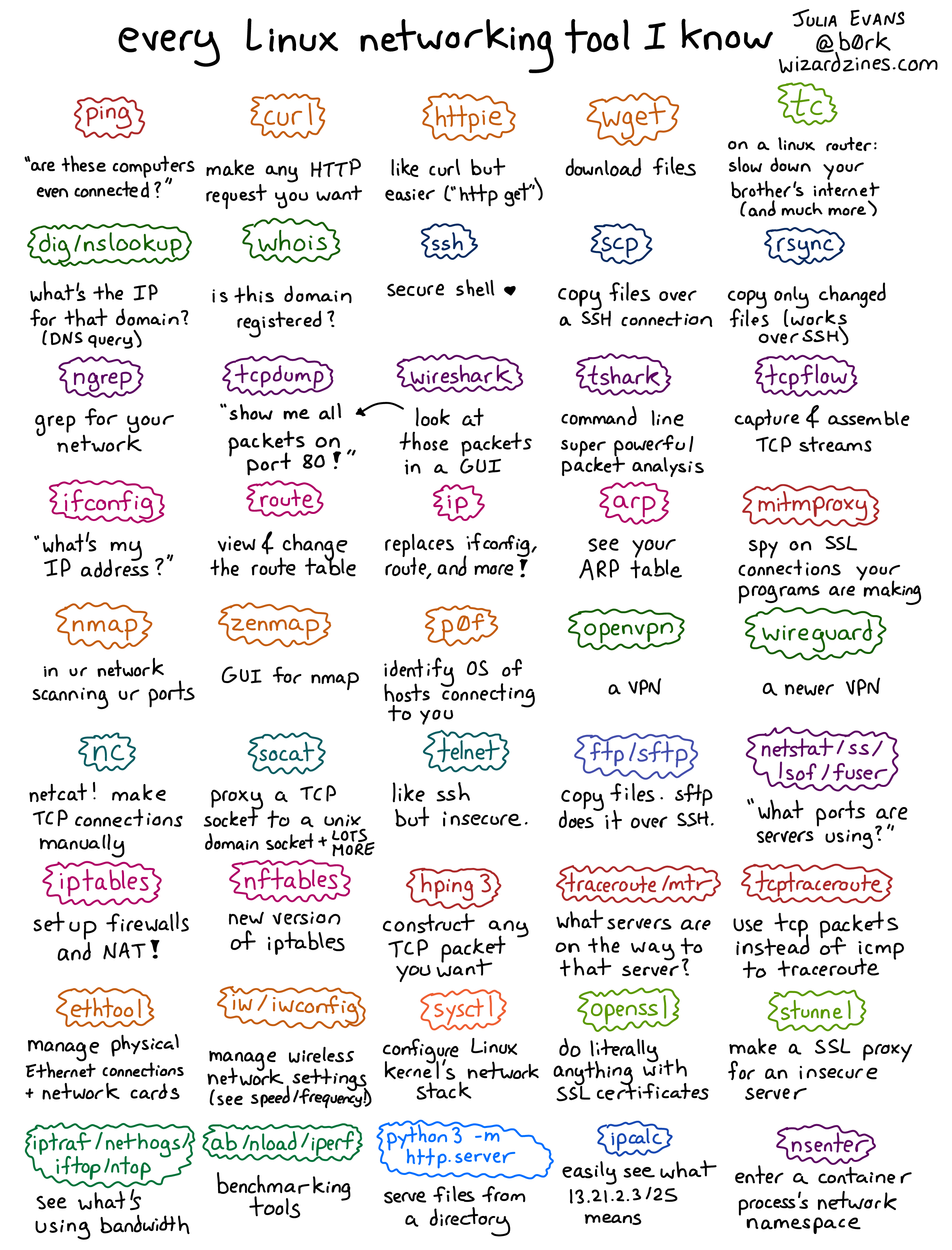
What are tools used in Linux
10 Linux Tools to Know as SysadminZenmap. When you need to discover network-related issues, Zenmap will come to the rescue.Webmin. This one-stop-shop tool offers a web-based interface for administering every aspect of a Linux server.Cockpit.gping.Shorewall.Nagios.phpMyAdmin.Puppet.
Cached
What are the three main components of a Linux system
In general, the Linux operating system is made up of three parts; the kernel, the shell, and the programs.
How many tools are in Kali Linux
600 tools
Kali Linux is an open-source distribution designed for cybersecurity professionals, ethical hackers, and penetration testers. It is Debian-derived and focused on providing over 600 tools for penetration testing and security auditing.
Cached
How many Linux commands are there
There are well over 100 Unix commands shared by the Linux kernel and other Unix-like operating systems. If you are interested in the commands frequently used by Linux sysadmins and power users, you've come to the place.
What are 3 examples of Linux
Popular Linux distributions include Debian, Fedora Linux, and Ubuntu, the latter of which itself consists of many different distributions and modifications, including Lubuntu and Xubuntu. Commercial distributions include Red Hat Enterprise Linux and SUSE Linux Enterprise.
Is Linux a software or tool
Linux® is an open source operating system (OS). An operating system is the software that directly manages a system's hardware and resources, like CPU, memory, and storage. The OS sits between applications and hardware and makes the connections between all of your software and the physical resources that do the work.
What are the 5 basic components of Linux
The Kernel, Hardware layer, System library, Shell, and System utility are the main components of the Linux Operating System's architecture.
What are the 4 elements of Linux
Every project begins by obtaining, customizing, and deploying these four elements: the toolchain, the bootloader, the kernel, and the root filesystem.
What are the top 10 tools in Kali Linux
The following is the list of the top 10 Kali Linux tools for hacking:Wireshark.Metasploit Framework.aircrack-ng.Netcat.John the Ripper.sqlmap.Autopsy.Social Engineering Toolkit. The Social Engineering Toolkit is a set of tools which we can use to perform social engineering attacks.
Why do hackers use Kali Linux
Kali Linux is a one-of-a-kind operating system that is used openly by both the bad and good guys. This operating system is widely used by both black hat hackers and security administrators. One prevents and detects security breachers, while the other identifies and potentially exploits security breachers.
What is the most used command in Linux
Top 50 Linux Commands You Must Know as a Regular Userls – The most frequently used command in Linux to list directories.pwd – Print working directory command in Linux.cd – Linux command to navigate through directories.mkdir – Command used to create directories in Linux.mv – Move or rename files in Linux.
How do I get a list of commands in Linux
Syntax-c − used to list all the commands you could run.-a − used to list all the aliases you could run.-k − used to list all the keywords you could run.-b − used to list all the built-ins you could run.-A function − used to list all the functions you could run.
What are the 2 types of Linux
Enterprise vs.
Linux distributions are available as community versions or enterprise versions. A community distro is a free Linux distro primarily supported and maintained by the open source software development community.
What is an example of a Linux device
Examples include iPods, PlayStations, Xbox, TiVo, and WRT54G.
Is Windows a Linux system
Windows 10 was not based on Linux or Unix, it was written by Microsoft and runs on their kernel, the Windows NT kernel. A kernel is the program at the core of an operating system, that has total control of the computer's hardware. It is the underlying framework for the OS.
What are the 7 fundamental files in Linux
Types of Files:Block file (b)Character device file (c)Named pipe file (p)Symbolic link file (l)Socket file (s)
Is it legal to use Kali Linux
Kali Linux is not illegal by itself. After all, it is just an OS. It is however a tool for hacking too and when someone uses it especially for hacking, it is illegal.
What is more powerful than Kali Linux
When it comes to general tools and functional features, ParrotOS takes the prize when compared to Kali Linux. ParrotOS has all the tools that are available in Kali Linux and also adds its own tools. There are several tools you will find on ParrotOS that is not found on Kali Linux. Let's look at a few such tools.
Is it illegal to use Kali Linux
Is Kali Linux illegal Kali Linux is not illegal by itself. After all, it is just an OS. It is however a tool for hacking too and when someone uses it especially for hacking, it is illegal.
Can you really hack with Kali Linux
Yes. Kali Linux has been specifically designed for penetration testing tasks and ethical hacking.
What are the four types of commands in Linux
These commands are entered into the terminal, which is a command-line interface that allows users to enter and execute commands.Types of Linux Commands.System Commands.File Management Commands.Networking Commands.Process Management Commands.Shell Built-in Commands.Advanced Linux Commands.
What are common Linux commands
Linux Commands FAQpwd (Prints the working directory)cat (Prints file contents)cp (Copies files and directories)mv (Moves and renames files and directories)rm (Remove files and directories)touch (Creates empty files)mkdir (Creates directories)
How do I get a list of all commands
Syntax-c − used to list all the commands you could run.-a − used to list all the aliases you could run.-k − used to list all the keywords you could run.-b − used to list all the built-ins you could run.-A function − used to list all the functions you could run.
What are the 3 types of files in Linux
The types of files recognized by the system are either regular, directory, or special. However, the operating system uses many variations of these basic types. All file types recognized by the system fall into one of these categories. However, the operating system uses many variations of these basic types.
What are 2 examples of Linux operating system
Ubuntu. Ubuntu is a Linux distribution based on Debian.Debian. Debian is an open source operating system.CentOS Linux. CentOS Linux is a distribution based on the source code of the commercial distribution Red Hat Enterprise Linux (RHEL).CentOS Stream.Gentoo.Fedora.OpenSUSE.Scientific Linux.



