What defenses are possible against TCP SYN spoofing attacks?
What Defences are possible against a TCP SYN spoofing attack
Q: How to Protect Against SYN Flood Attacks?
A: There are several defences that can be implemented to protect against SYN flood attacks. One approach is to increase the backlog queue, which allocates memory to hold half-open connections as SYN backlog. Another method is to recycle the oldest half-open connection. Additionally, using SYN cookies and firewall filtering can also provide protection against SYN flood attacks.
Q: How can we protect against SYN attack?
A: SYN floods are a form of DDoS attack that attempts to flood a system with requests in order to consume resources and ultimately disable it. To protect against SYN flood attacks, you can install an IPS (Intrusion Prevention System), configure your firewall, install up-to-date networking equipment, and use commercial monitoring tools.
Q: What is the role of cookies in defending against SYN spoofing attacks?
A: SYN cookies are a technique used to resist SYN flood attacks. They involve particular choices of initial TCP sequence numbers by TCP servers. By using SYN cookies, a server can avoid dropping connections when the SYN queue fills up.
Q: Which of the following measures help reduce the impact of a SYN flooding attack on a server?
A: One measure is to use the sequence number of the ACK packet to cryptographically verify the connection establishment and establish the connection. Another measure is the use of SYN cookies, which offer effective protection against SYN flood attacks.
Q: What is the best method for defending against IP spoofing?
A: Some methods for defending against IP spoofing include using firewalls and spoofing software, encryption protocols, packet filtering, training nudges, and DLP (Data Loss Prevention) techniques.
Q: What are the preventive measures against TCP IP attacks?
A: To prevent TCP/IP attacks, it is important to implement a defense-in-depth strategy that involves multiple layers of protection and controls. Configuring routers and firewalls to filter or drop unwanted or malformed packets is crucial in ensuring the safety of your network.
Q: What protocol is used to carry out a SYN flood attack?
A: SYN floods take advantage of TCP/IP vulnerabilities to overwhelm target systems. These attacks use the TCP three-way handshake process.
Q: What is an example of a TCP SYN attack?
A: An example of a TCP SYN flood attack is when an attacker uses a port scanner tool to identify the list of open TCP ports on the victim host. The attacker then selects an open TCP port number and uses it as the destination port number in the TCP SYN flood attack packets.
Q: What is SYN cookie protection?
A: SYN cookie protection is a feature that protects systems against SYN flood attacks. It allows the system to maintain connections even when the SYN queue begins to fill up during an attack.
Q: What is cookie protection?
A: Cookie protection, specifically Total Cookie Protection, prevents cookies from tracking you across the web. It works by creating a separate “cookie jar” for each website visited, preventing trackers from linking your behavior on multiple sites.
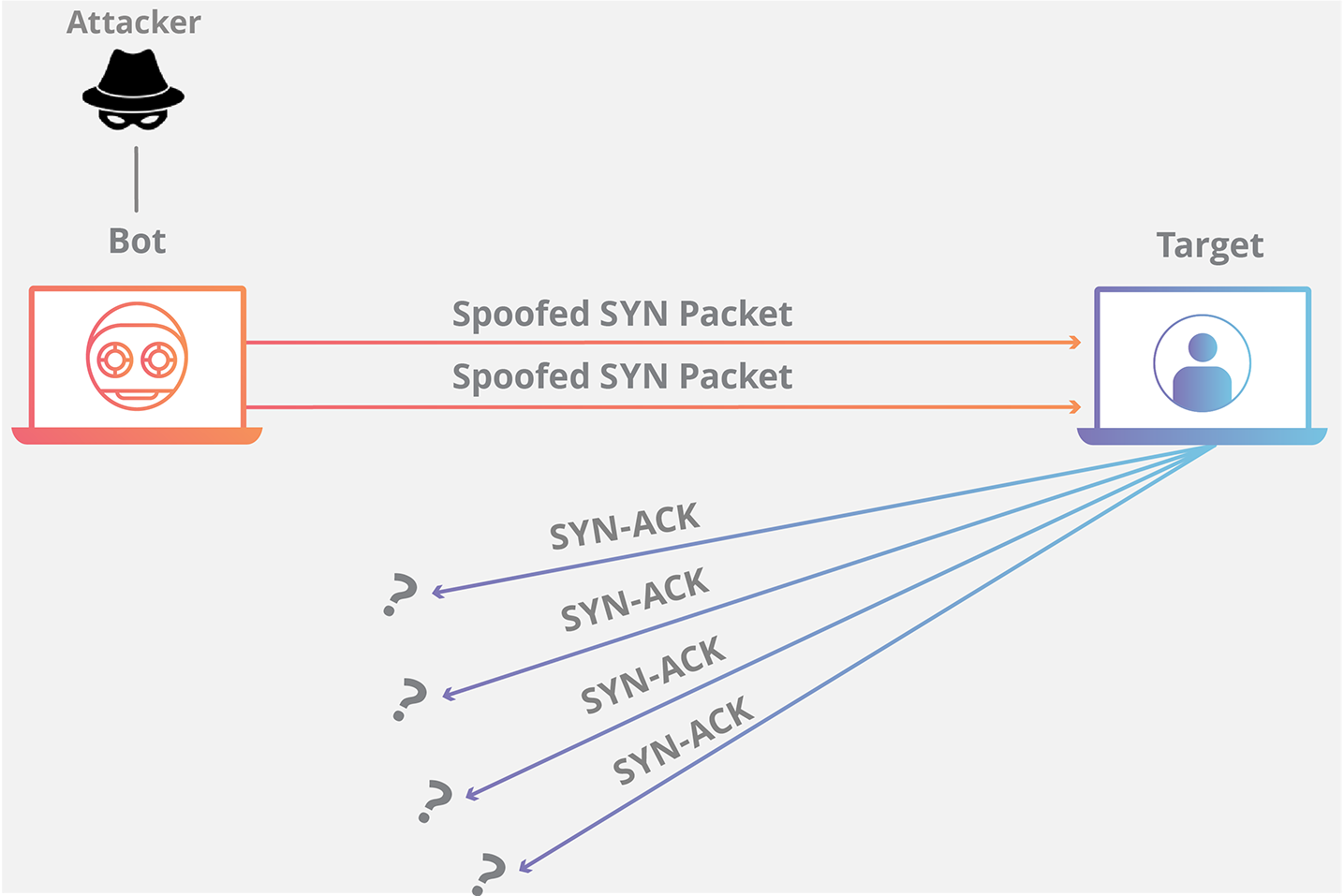
What Defences are possible against a TCP SYN spoofing attack
How to Protect Against SYN Flood AttacksIncrease Backlog Queue. Each OS allocates certain memory to hold half-open connections as SYN backlog.Recycling the oldest half-open connection.SYN Cookies.Firewall Filtering.
Cached
How can we protect against SYN attack
SYN floods are a form of DDoS attack that attempts to flood a system with requests in order to consume resources and ultimately disable it. You can prevent SYN flood attacks by installing an IPS, configuring your firewall, installing up to date networking equipment, and installing commercial monitoring tools.
What is the role of cookies in defending against SYN spoofing attacks
SYN cookie is a technique used to resist SYN flood attacks. The technique's primary inventor Daniel J. Bernstein defines SYN cookies as "particular choices of initial TCP sequence numbers by TCP servers." In particular, the use of SYN cookies allows a server to avoid dropping connections when the SYN queue fills up.
Which of the following measures help reducing the impact of a SYN flooding attack on a server
The server uses the sequence number of the ACK packet to cryptographically verify the connection establishment and to establish the connection. The use of SYN cookies offers effective protection against SYN flood attacks.
What is the best method for defending against IP spoofing
These include:Firewalls and spoofing software. Firewalls are your first line of defense, so make sure they are configured and updated regularly.Encryption protocols. Make use of upper layer protocols that have built-in safeguards against spoofing.Packet filtering.Training nudges.DLP.
What are the preventive measures against TCP IP attacks
How to prevent TCP/IP attacks The best way to prevent TCP/IP attacks is to implement a defense-in-depth strategy that involves multiple layers of protection and controls. To ensure the safety of your network, it is important to configure routers and firewalls to filter or drop unwanted or malformed packets.
What protocol is used to carry out a SYN flood attack
TCP/IP
SYN floods are one of several common vulnerabilities that take advantage of TCP/IP to overwhelm target systems. SYN flood attacks use a process known as the TCP three-way handshake.
What is an example of TCP SYN attack
An example of a TCP SYN flood attack packet The attacker at host "A" can use any port scanner tool to identify the list of open TCP ports at the victim host. Then, the attacker can select one open TCP port number and use it as the destination port number in the TCP SYN flood attack packets.
What is SYN cookie protection
Description. The BIG-IP SYN cookie feature protects the system against SYN flood attacks. SYN cookies allow the BIG-IP system to maintain connections when the SYN queue begins to fill up during an attack.
What is cookie protection
Total Cookie Protection stops cookies from tracking you around the web. Total Cookie Protection works by creating a separate “cookie jar” for each website you visit. Instead of allowing trackers to link up your behavior on multiple sites, they just get to see behavior on individual sites.
What are 3 things that can be done to mitigate or prevent damage from flooding
Elevate major appliances onto concrete blocks. Clean gutters, downspouts, and splash pads, along with any nearby drainage ditches or storm drains; clear snow and ice away from foundations. Deploy temporary flood barriers, such as portable flood gates or shields, sandbags, inflatable floodwalls, and flood skirts.
Does SSL protect against SYN flooding
SYN attacks try to exhaust a system so that no successful TCP handshakes can be done. But the SSL/TLS protocol starts only after a successful TCP handshake, i.e. it requires a successful TCP handshake first. Therefore SSL/TLS does not help against SYN flooding.
What is one example of a control that can reduce the potential of spoofing
Packet filtering can prevent an IP spoofing attack since it is able to filter out and block packets that contain conflicting source address information. Using cryptographic network protocols such as HTTP Secure (HTTPS) and Secure Shell (SSH) can add another layer of protection to your environment.
What is the most effective solution to DNS spoofing security threat
To protect from DNS spoofing, internet providers can use DNSSEC (DNS security). When a domain owner sets up DNS entries, DNSSEC adds a cryptographic signature to the entries required by resolvers before they accept DNS lookups as authentic.
What are the 3 key prevention measures of cyber attacks
4 Things to Keep You Cyber SafeTurn on Multifactor Authentication. Implement multifactor authentication on your accounts and make it significantly less likely you'll get hacked.Update Your Software. Update your software.Think Before You Click. Think before you click.Use Strong Passwords.
What happens if TCP SYN is dropped
If the initial TCP handshake is failing because of packet drops, then you would see that the TCP SYN packet is retransmitted only three times. Source side connecting on port 445: Destination side: applying the same filter, you don't see any packets. For the rest of the data, TCP will retransmit the packets five times.
How is the TCP SYN flood denial-of-service attack carried out
A TCP SYN flood DDoS attack occurs when the attacker floods the system with SYN requests in order to overwhelm the target and make it unable to respond to new real connection requests. It drives all of the target server's communications ports into a half-open state.
What countermeasures can you use to control TCP IP hijacking
VPN: Use a Virtual Private Network (VPN) to stay safe from session hijackers. A VPN masks your IP and keeps your session protected by creating a “private tunnel” through which all your online activities will be encrypted.
What are some TCP vulnerabilities
Mitigations are available, but they do need to be implemented properly to ensure secure TCP/IP use.IP address spoofing.ARP spoofing.Port scanning.ICMP attacks.Packet reassembly and sequence prediction.MitM attacks.DoS and DDoS attacks.
What are the security risks of SYN cookies
These cookies do not present a security threat or risk to either the host or clients and do not cause connectivity issues or problems. The way in which SYN cookies function is built on the basic way by which many servers and users, or host and client systems, connect to each other.
How does its countermeasure using SYN cookies work
SYN cookies is a technical attack mitigation technique whereby the server replies to TCP SYN requests with crafted SYN-ACKs, without inserting a new record to its SYN Queue. Only when the client replies this crafted response a new record is added.
What is the difference between cookie and secure cookie
A secure cookie instructs the browser that the cookie may only be sent to the server when connecting through SSL. An insecure cookie will be sent to both http:// and https:// connections. This mechanism ensures that session cookies (if set as secure) will always be encrypted in order to prevent eavesdropping.
Does clearing cookies protect you
If it's your personal device, it's a good idea to remove all cookies at least once a month to keep your device neat. Also, you should do this if you see a drop in browser performance or after visiting a shady website. This will make you re-enter multiple logins, but doing that for the sake of your privacy is worth it.
What are 4 ways humans prevent and or protect from flooding
Flood-proof StructuresElevate the furnace, water heater, air conditioner and other utilities.Install "check valves" in sewer traps to prevent flood water back ups.Construct interior barriers to stop low level floodwater from entering basements.Seal walls in basements with waterproofing compounds to avoid seepage.
Which of the following can reduce the risk of flooding
∙ Building dams and reservoirs.



