What is encrypt data?
Summary of the Article: What Does it Mean to Encrypt Data
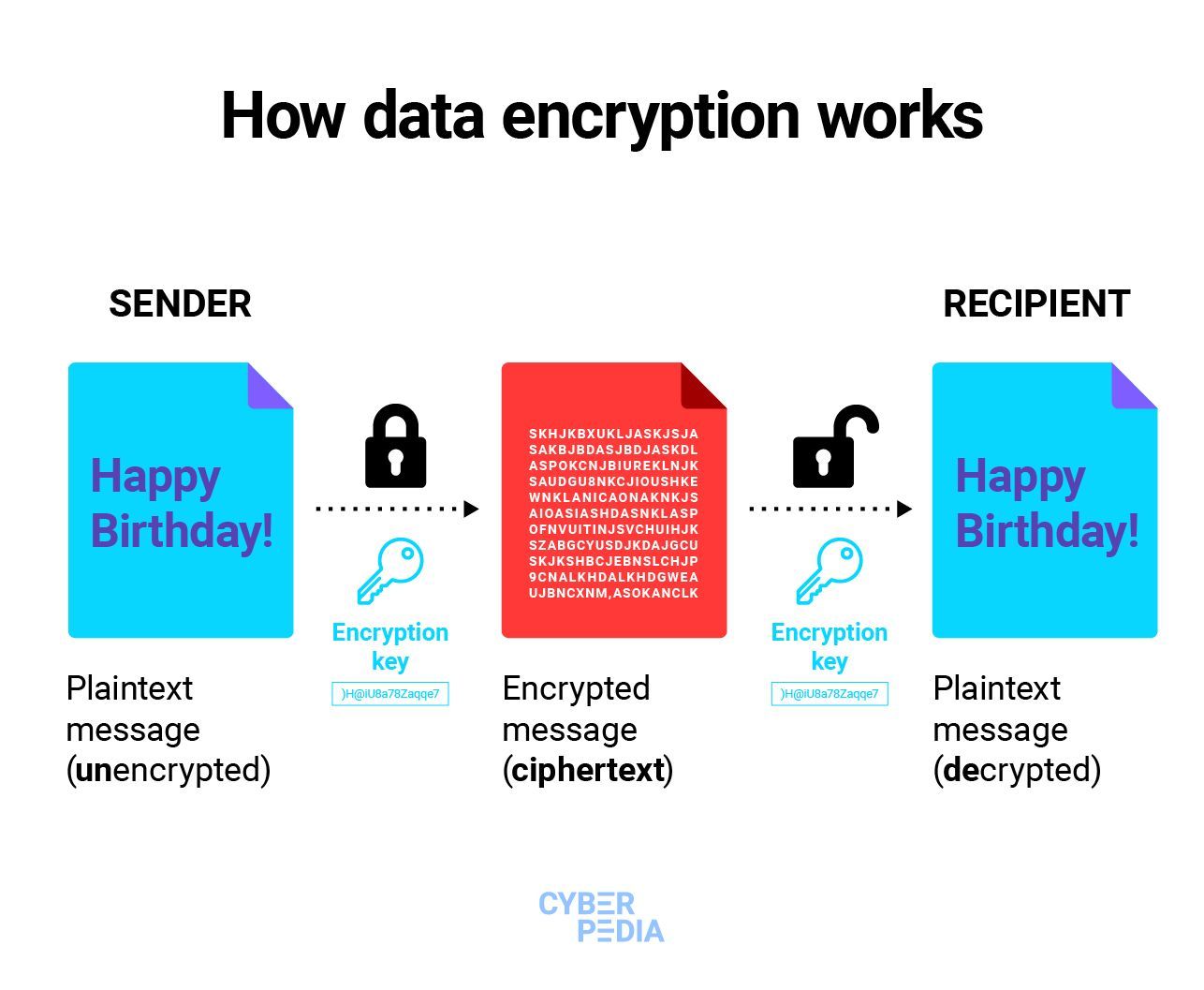
Data encryption is a way of translating data from plaintext (unencrypted) to ciphertext (encrypted). Users can access encrypted data with an encryption key and decrypted data with a decryption key. Encryption is crucial in protecting sensitive information and preventing unauthorized access.
Key Points:
1. What does it mean to encrypt data?
Data encryption is the process of converting data from plaintext to ciphertext using an encryption algorithm and an encryption key. It ensures that sensitive information remains secure and unreadable to unauthorized parties.
2. What is an example of encrypted data?
One example of encrypted data is the transmission of credit card and bank account numbers on websites. By encrypting this information, it becomes extremely difficult for hackers to steal and misuse the data, protecting users from identity theft and fraud.
3. What is encrypted data on iPhone?
On devices like iPhone, messages are encrypted on the device itself, ensuring that they cannot be accessed without the user’s passcode. iMessage and FaceTime are designed in a way that even Apple cannot read the messages during transit between devices.
4. Why would you encrypt data?
Data encryption helps protect private information and sensitive data from unauthorized access. It enhances the security of communication between client apps and servers, ensuring that even if the data is intercepted, it cannot be read without the decryption key.
5. What happens if I encrypt data?
Encrypting data converts it from a readable, plaintext format into an unreadable, encoded format called ciphertext. Only authorized users and processes with the decryption key can access and read the encrypted data, ensuring its confidentiality.
6. How do I encrypt my data?
To encrypt data on your device, you can set a lock screen PIN, pattern, or password. Then, go to the device’s Settings app, navigate to Security & Location, and under “Encryption,” choose to encrypt the phone or tablet. Follow the instructions and enter your lock screen PIN, pattern, or password to complete the encryption process.
7. How can you tell that your data is being encrypted?
To check if your hard drive is encrypted on a Windows device, open the Data Protection window and look for the System Storage section. If you see the text “OSDisk (C)” and “In compliance” underneath, it indicates that your hard drive is encrypted.
8. Can someone access my iPhone from another device?
While it is technically possible for someone to remotely hack an iPhone, it is highly unlikely for most users. Remote hacking requires expensive software and specialized techniques, making it a viable option only for high-value targets.
9. How can I check if someone has access to my iPhone?
To check if someone else has access to your iPhone, sign in to the Apple ID website and review all personal and security information associated with your account. Ensure that there are no unfamiliar devices listed under trusted devices and check for any unauthorized changes made to your account.
10. What happens if you don’t encrypt data?
Without encryption, your data remains vulnerable to unauthorized access and exploitation. Hackers can target databases and exploit unprotected information, potentially leading to identity theft, financial fraud, and other security breaches.
What does it mean to encrypt data
Data encryption is a way of translating data from plaintext (unencrypted) to ciphertext (encrypted). Users can access encrypted data with an encryption key and decrypted data with a decryption key. Protecting your data.
Cached
What is an example of encrypted data
Encryption is an important way for individuals and companies to protect sensitive information from hacking. For example, websites that transmit credit card and bank account numbers encrypt this information to prevent identity theft and fraud.
Cached
What is encrypted data on Iphone
With watchOS, iOS, and iPadOS, your messages are encrypted on your device so they can't be accessed without your passcode. iMessage and FaceTime are designed so that there's no way for Apple to read your messages when they're in transit between devices.
Why would you encrypt data
It helps protect private information, sensitive data, and can enhance the security of communication between client apps and servers. In essence, when your data is encrypted, even if an unauthorized person or entity gains access to it, they will not be able to read it.
Cached
What happens if I encrypt data
Data encryption converts data from a readable, plaintext format into an unreadable, encoded format: ciphertext. Users and processes can only read and process encrypted data after it is decrypted. The decryption key is secret, so it must be protected against unauthorized access.
How do I encrypt my data
If you haven't already, set a lock screen PIN, pattern, or password.Open your device's Settings app.Tap Security & Location.Under "Encryption," tap Encrypt phone or Encrypt tablet.Carefully read the information shown.Tap Encrypt phone or Encrypt tablet.Enter your lock screen PIN, pattern, or password.
How can you tell that your data is being encrypted
In the Data Protection window, click on the icon of the hard drive (aka System Storage). Under System Storage, if you see the following text: OSDisk (C) and In compliance underneath, then your hard drive is encrypted.
Can someone access my iPhone from another device
In conclusion, it is technically possible for someone to remotely hack an iPhone, but it is highly unlikely to happen to most users. The expensive software and specialized techniques required for remote hacking make it a viable option only for high-value targets.
How can I check if someone has access to my iPhone
Sign in to the Apple ID website (https://appleid.apple.com) and review all the personal and security information in your account to see if there is any information that someone else has added. If you have two-factor authentication turned on, review trusted devices for any devices that you don't recognize.
What happens if you don’t encrypt data
Unprotected Data in Use Makes You Vulnerable
A great deal of data is available for hackers to access and exploit. An attacker targeting a specific company's databases could go to LinkedIn and quickly find a few employees who are likely to have admin access to enterprise IT resources.
How do I know if my data is encrypted
In the Data Protection window, click on the icon of the hard drive (aka System Storage). Under System Storage, if you see the following text: OSDisk (C) and In compliance underneath, then your hard drive is encrypted.
Can encrypted data be tracked
No, hackers cannot see encrypted data, as it is scrambled and unreadable until the encryption key (or passphrase) is used to decrypt it. However, if a hacker manages to obtain the encryption key or crack the encryption algorithm, then they can gain access to the data.
What happens when your data is encrypted
Data encryption converts data from a readable, plaintext format into an unreadable, encoded format: ciphertext. Users and processes can only read and process encrypted data after it is decrypted. The decryption key is secret, so it must be protected against unauthorized access.
Can someone access my phone from another device
Yes, unfortunately, people can access and even control your phone remotely. There are plenty of spyware apps and bugs that let people hack into your phone without you even knowing about it. It's usually through certain links or credentials that hackers do this.
How can you tell if someone is connected to your iPhone
Sign in to the Apple ID website (https://appleid.apple.com) and review all the personal and security information in your account to see if there is any information that someone else has added. If you have two-factor authentication turned on, review trusted devices for any devices that you don't recognize.
How do I know if my iPhone is synced to another device
From the Devices section of your Apple ID account page, you can find all of the devices that you're currently signed in to with your Apple ID, including Android devices, consoles, and smart TVs: Sign in to appleid.apple.com,* then select Devices.
Can your iPhone be monitored by someone else
Technically, yes. From your friend, or employer to a cybercriminal – there's a possibility of becoming spied upon. Regardless of what device you use, it is possible for someone to gain remote access and to spy on your iPhone too. With spyware, a person can access a lot of your personal data.
Is encryption good or bad
Internet Security
Consider its role: Encryption helps keep you safe while doing things like browsing the Web, shopping online, and reading email on your computer or mobile device. It's critical to computer security, helps to protect data and systems, and helps to protect you against identity theft.
Can you tell if your phone is being monitored
However, if someone is spying on your phone, there are common signs you can look out for. You may notice a rapid increase in your phone's data usage, suspicious files or applications, or strange text messages that you don't remember sending. Your device may also show signs of malfunctioning behavior.
Can you tell if someone has remote access to your phone
Signs That Someone Has Remote Access to Your Phone
The battery drains quickly even when not in use. Higher data usage than usual. Noises in the background when you're on a phone call. You receive unusual messages, emails, or notifications.
How can I tell if my iPhone is synced to another device
If you connect to a computer, it syncs. Your device may sync with iCloud. There isn't anything else to sync or link. If you log into your Apple ID account appleid.apple.com, you can see all of your active devices.
Can someone connect to your phone without you knowing
Can Someone Access My Phone Remotely Yes, unfortunately, people can access and even control your phone remotely. There are plenty of spyware apps and bugs that let people hack into your phone without you even knowing about it. It's usually through certain links or credentials that hackers do this.
Can my phone be linked to someone else’s
Yes, you can link an Android phone with another Android phone. There are mainly two ways to connect two Android phones. Bluetooth is the most basic way to connect two phones wirelessly. But here is a better way which is to use a third-party Android app to remotely control another phone.
Can you tell if someone has access to your phone
Signs That Someone Has Remote Access to Your Phone
The battery drains quickly even when not in use. Higher data usage than usual. Noises in the background when you're on a phone call. You receive unusual messages, emails, or notifications.
How do I know if my iPhone is linked to another device
From the Devices section of your Apple ID account page, you can find all of the devices that you're currently signed in to with your Apple ID, including Android devices, consoles, and smart TVs: Sign in to appleid.apple.com,* then select Devices.



