What is Kerberos in information security?
Summary of the Article
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users’ identities.
Key Points
1. What is Kerberos in computer security?
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet.
2. What is Kerberos with example?
Kerberos is used to authenticate entities requesting access to network resources, especially in large networks to support SSO. The protocol is used by default in many widely used networking systems.
3. What is an example of Kerberos authentication?
Kerberos uses include: Amazon Web Services (AWS) and Google Cloud.
4. What does Kerberos protect against?
Kerberos protocol messages are protected against eavesdropping and replay attacks. Kerberos builds on symmetric-key cryptography and requires a trusted third party.
5. What are the 3 main parts of Kerberos?
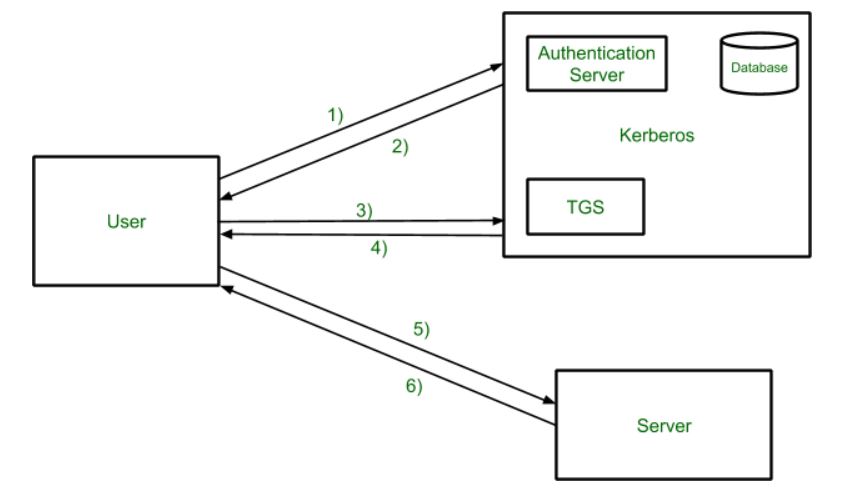
Components of Kerberos: Client-Server, Authentication Server (AS), Key Distribution Center (KDC), and Ticket Granting Server (TGS).
6. What is Kerberos vs SSL?
Kerberos is free and open-source software, executed in Microsoft products like Windows 2000, Windows XP, etc. SSL is patented and does not provide free services.
7. What are two benefits of Kerberos?
Kerberos authentication offers advantages like mutual authentication and reduced risk of password theft.
8. What 4 requirements were defined by Kerberos?
Kerberos requirements: Secure, Reliable, Transparent, and Scalable.
9. What is the difference between Kerberos and LDAP?
Kerberos is a ticket-based authentication protocol for trusted hosts on untrusted networks, while LDAP is an authentication protocol for accessing server resources.
10. What websites use Kerberos?
Microsoft Windows and Microsoft Active Directory are among the widely known products that use Kerberos.
11. What is the advantage of Kerberos?
Kerberos provides strong encryption algorithms to protect passwords and authentication tickets.
Questions and Detailed Answers
1. What is Kerberos in computer security?
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users’ identities.
2. What is Kerberos with example?
Kerberos is used to authenticate entities requesting access to network resources, especially in large networks to support SSO. The protocol is used by default in many widely used networking systems, such as Amazon Web Services (AWS).
3. What is an example of Kerberos authentication?
Kerberos uses include: Amazon Web Services (AWS) and Google Cloud.
4. What does Kerberos protect against?
Kerberos protocol messages are protected against eavesdropping and replay attacks. Kerberos builds on symmetric-key cryptography and requires a trusted third party, and it may also use public-key cryptography during certain phases of authentication.
5. What are the 3 main parts of Kerberos?
The three main parts of Kerberos are the Client-Server, the Authentication Server (AS), the Key Distribution Center (KDC), and the Ticket Granting Server (TGS).
6. What is Kerberos vs SSL?
While SSL uses public-key encryption, Kerberos is not patented and provides free services as open-source software. Kerberos is executed in Microsoft products like Windows 2000, Windows XP, etc.
7. What are two benefits of Kerberos?
Kerberos authentication offers several advantages over other access control methods, such as mutual authentication, which allows both the client and the server to verify each other’s identity. It also reduces the risk of password theft, as passwords are never sent over the network in plain text.
8. What 4 requirements were defined by Kerberos?
Kerberos requirements include being secure (no masquerading), reliable (distributed server architecture), transparent (user unaware authentication is taking place), and scalable (support large number of clients and servers).
9. What is the difference between Kerberos and LDAP?
While Kerberos is a ticket-based authentication protocol for trusted hosts on untrusted networks, Lightweight Directory Access Protocol (LDAP) is an authentication protocol for accessing server resources over an internet or intranet.
10. What websites use Kerberos?
Perhaps the most widely known products which use Kerberos are Microsoft Windows and Microsoft Active Directory. In a Microsoft network/domain, users authenticate using the Kerberos protocol when they logon to their Windows workstation.
11. What is the advantage of Kerberos?
Kerberos is far from obsolete and has proven itself as an adequate security-access control protocol, despite attackers’ ability to crack it. The primary advantage of Kerberos is the ability to use strong encryption algorithms to protect passwords and authentication tickets.
What is Kerberos in computer security
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users' identities.
Cached
What is Kerberos with example
Kerberos is used to authenticate entities requesting access to network resources, especially in large networks to support SSO. The protocol is used by default in many widely used networking systems. Some systems in which Kerberos support is incorporated or available include the following: Amazon Web Services.
What is an example of Kerberos authentication
Kerberos Uses
Kerberos implementations are used on a number of operating systems and networking systems to verify user accounts. Examples include: Amazon Web Services (AWS) Google Cloud.
What does Kerberos protect against
Kerberos protocol messages are protected against eavesdropping and replay attacks. Kerberos builds on symmetric-key cryptography and requires a trusted third party, and optionally may use public-key cryptography during certain phases of authentication.
CachedSimilar
What are the 3 main parts of Kerberos
Components of KerberosClient.Server.Authentication Server (AS)Key Distribution Center (KDC)Ticket Granting Server (TGS)
What is Kerberos vs SSL
While SSL uses public-key encryption. Kerberos is not patented; therefore, it provides free services and is open-source software. SSL is patented; hence, it does not provide free services. Kerberos is executed in Microsoft products like Windows 2000, Windows XP, and so on.
What are two 2 benefits of Kerberos
Kerberos authentication offers several advantages over other access control methods, such as mutual authentication, which allows both the client and the server to verify each other's identity. It also reduces the risk of password theft, as passwords are never sent over the network in plain text.
What 4 requirements were defined by Kerberos
Kerberos RequirementsSecure – no masquerading.Reliable – distributed server architecture.Transparent – user unaware authentication is taking place.Scalable – support large number of clients and servers.
What is the difference between Kerberos and LDAP
While Kerberos is a ticket-based authentication protocol for trusted hosts on untrusted networks, Lightweight Directory Access Protocol (LDAP) is an authentication protocol for accessing server resources over an internet or intranet.
What websites use Kerberos
Perhaps the most widely know products which use Kerberos, are Microsoft Windows and Microsoft Active Directory. In a Microsoft network/domain, users authenticate using the Kerberos protocol when they logon to their Windows workstation.
What is the advantage of Kerberos
Kerberos is far from obsolete and has proven itself an adequate security-access control protocol, despite attackers' ability to crack it. The primary advantage of Kerberos is the ability to use strong encryption algorithms to protect passwords and authentication tickets.
What layer of OSI is Kerberos
Kerberos is a trusted third-party authentication application layer service (Layer 7 of the OSI model).
Is Kerberos a SSO service
Kerberos: Kerberos is an authentication protocol that supports the concept of Single Sign-On (SSO). In the case of HTTP, support for Kerberos is usually provided using the term "SPNEGO" authentication mechanism.
What is the main function of Kerberos
Organizations need a better way to protect their systems and users. This is where Kerberos comes in. A Kerberos is a system or router that provides a gateway between users and the internet. Therefore, it helps prevent cyber attackers from entering a private network.
What is the disadvantage of Kerberos
Tickets in Kerberos have a limited period. If the ticket gets stolen, it is hard to reuse it because of strong authentication needs. Passwords are never sent over the network unencrypted.
What are the 3 heads of Kerberos
Kerberos is another name for the three headed hound that guarded Hades in Greek mythology. Most of us in the US know the mythical beast by the name Cerebos. The mythological Kerberos was the offspring of Echidna and Typhon and was captured by Heracles as one of his twelve labors.
What are the main features of Kerberos
The basic features of Kerberos may be put as:It uses symmetric keys.Every user has a password ( key from it to the Authentication Server )Every application server has a password.The passwords are kept only in the Kerberos Database.The Servers are all physically secure.The user gives the password only once.
Is Kerberos same as SSL
While SSL uses public-key encryption. Kerberos is not patented; therefore, it provides free services and is open-source software. SSL is patented; hence, it does not provide free services. Kerberos is executed in Microsoft products like Windows 2000, Windows XP, and so on.
What is the main difference between SSL and Kerberos
While Kerberos and SSL are both protocols, Kerberos is an authentication protocol, but SSL is an encryption protocol. Kerberos usually uses UDP, SSL uses (most of the time) TCP. SSL authentication is usually done by checking the server's and the client's RSA or ECDSA keys embedded in something called X.
How is Kerberos used today
It is the default authorization technology in Microsoft Windows. It uses third-party ticket authorization and strong cryptography to make it harder for hackers to gain access to a corporate network. With Kerberos, organizations can access the internet without having to worry about compromising their safety.
Is Kerberos a VPN
Kerberos is a network authentication protocol created by MIT, and uses symmetric-key cryptography to authenticate users to network services. And IPSec is a typical security protocol that is used to construct VPN (virtual private network) in network layer of TCP/IP protocol.
Which type of protocol is Kerberos
Kerberos is a network authentication protocol. It is designed to provide strong authentication for client/server applications by using secret-key cryptography. A free implementation of this protocol is available from the Massachusetts Institute of Technology. Kerberos is available in many commercial products as well.
Is Kerberos a SSL
SSL is not part of the Kerberos protocol, but software that uses Kerberos for client and server authentication may use SSL as well.
What is the difference between Kerberos and SSO
Kerberos is still the back-end technology. Kerberos excels at Single-Sign-On (SSO), which makes it much more usable in a modern internet based and connected workplace. With SSO you prove your identity once to Kerberos, and then Kerberos passes your TGT to other services or machines as proof of your identity.
Is Kerberos and SSO same
Kerberos: Kerberos is an authentication protocol that supports the concept of Single Sign-On (SSO). In the case of HTTP, support for Kerberos is usually provided using the term "SPNEGO" authentication mechanism.



