What is rat virus computer?
Summary
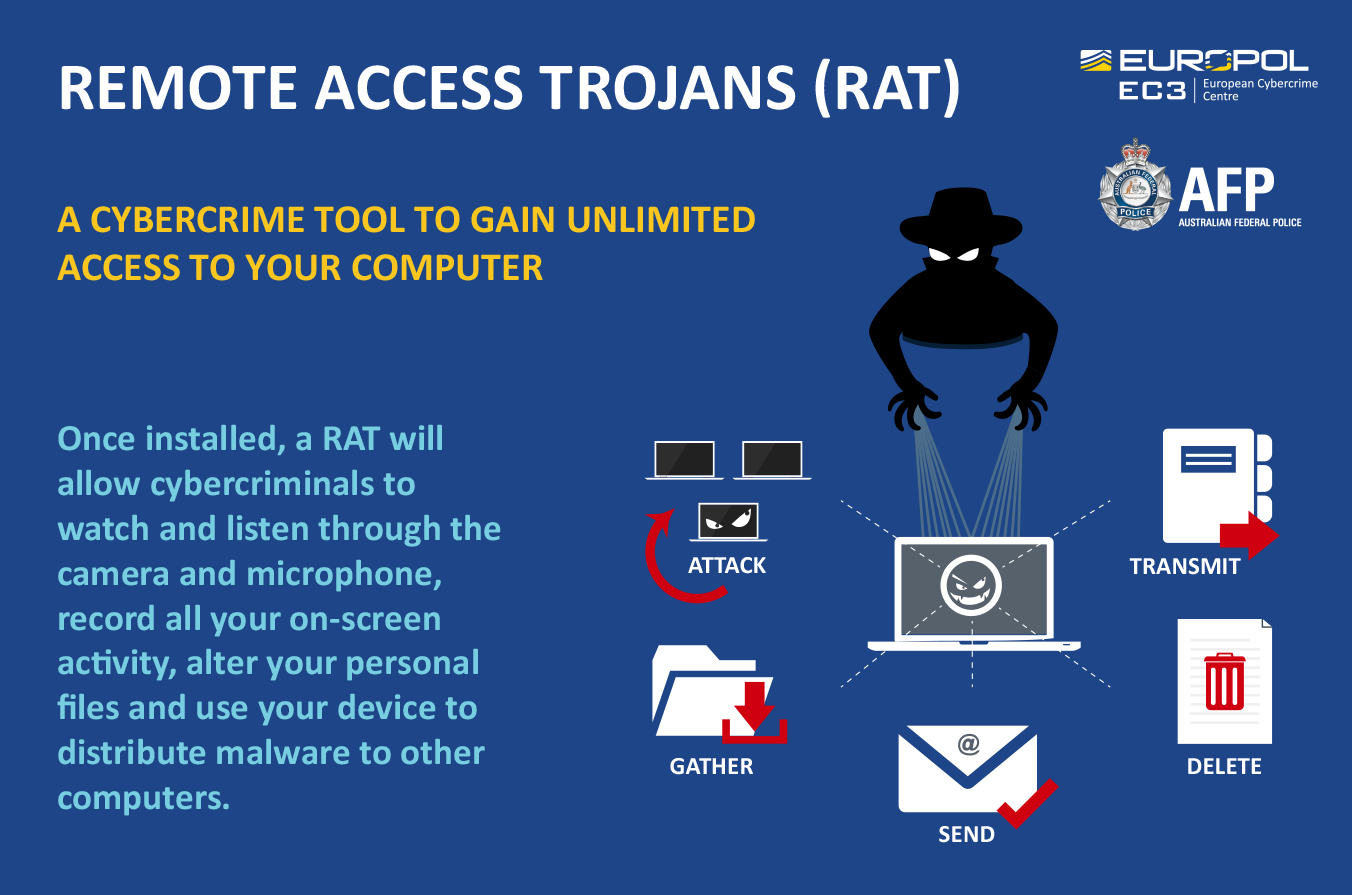
RATs (Remote Access Trojans) are trojans that can present as legitimate applications. They typically comprise malicious functionality connected to a real application. RATs are similar to malware, but the main difference is that RATs are installed on a computer without a user’s knowledge. RATs cannot spread through WiFi and antivirus software can detect them. To get rid of rats in your house, you need to locate and seal entry points, repel rats, remove food and water sources, remove hiding places, and set traps. Zeus is a harmful Trojan that steals personal financial data. While a VPN provides protection, it may not be foolproof against all types of attacks. When a RAT is installed on your computer, an attacker can remotely control it and send commands. Rats can enter through small openings around windows. Back Orifice is an example of a RAT spyware. The survival time of the rat virus depends on factors such as temperature.
Questions and Answers
1. What is the difference between a RAT and a Trojan?
RATs are trojans that can present as legitimate applications. They typically comprise malicious functionality connected to a real application. Monitor applications and systems for unusual behavior that may indicate a RAT.
2. What is the difference between RAT and malware?
A RAT is a type of malware that’s very similar to legitimate remote access programs. The main difference is that RATs are installed on a computer without a user’s knowledge.
3. Can RATs spread through WiFi?
RATs cannot attack other devices across the same WiFi network. As long as your devices are secured and have proper encryption, they should not be affected by RATs.
4. Can antivirus detect RATs?
Antivirus software like Bitdefender, Kaspersky, Webroot, or Norton can detect RATs and other types of malware if they infect your devices. The software may recognize a RAT by its signature or by its actions.
5. How do you get rid of rats?
To get rid of rats in the house fast, you can follow these effective ways: locate all entry points, seal the gaps, repel rats, remove food and water sources, remove hiding places, and set traps.
6. What is the most harmful Trojan?
Zeus is a Trojan horse designed to steal personal financial data such as passwords and bank details. It was discovered in 2007 and used to steal money from major corporations and banks.
7. Does a VPN protect against RAT?
A VPN provides protection, but it may not be foolproof against attacks like DoS and DDoS. If an attacker has a backdoor on your system or has infected it with a RAT, they may be able to find your real IP address.
8. What will happen when a RAT is installed on your computer?
When a RAT is installed on your computer, an attacker can remotely control it. They can send commands to the RAT and receive data back in response.
9. Can rats jump through windows?
Rats can easily enter through small gaps or cracks around windows. It is important to seal any openings and check your window screens for holes.
10. What is an example of a rat spyware?
Back Orifice is a well-known example of a RAT spyware. It was created by a hacker group called the Cult of the Dead Cow to expose security deficiencies in Microsoft’s Windows OS.
11. How long does the rat virus last?
The virus can survive for 2 or 3 days at normal room temperature. Exposure to sunlight will decrease its viability, while freezing temperatures will increase its survival time.
What is the difference between a RAT and a Trojan
RATs are trojans that can present as legitimate applications. RATs typically comprise malicious functionality connected to a real application. Monitor applications and systems for unusual behavior that may indicate a RAT.
Cached
What is the difference between RAT and malware
A RAT is a type of malware that's very similar to legitimate remote access programs. The main difference, of course, is that RATs are installed on a computer without a user's knowledge.
Cached
Can RATs spread through WiFi
RAT or remote access Trojan cannot attack other devices across the same WiFi network and as long as your devices are secured and have proper encryption, we believe that it will not affect your devices.
Can antivirus detect RATs
Antivirus software like Bitdefender, Kaspersky, Webroot, or Norton, can detect RATs and other types of malware if they infect your devices. Depending on the type of software you're buying, it may recognize a RAT by its signature or by its actions. Some antivirus software can do both.
Cached
How do you get rid of rats
How To Get Rid Of Rats In The House Fast: 7 Effective WaysLocate all Entry Points. Before getting rid of rats, you must conduct a complete inspection to determine where they're coming from.Seal The Gaps.Repel Rats.Remove Food And Water Sources.Remove Hiding Places.Set Traps.
What is the most harmful Trojan
Zeus. Zeus is a Trojan horse designed to steal personal financial data such as passwords and bank details. It was first discovered in 2007 and roped infected devices into a botnet, a large network of computers controlled by hackers. Cybercriminals used the botnet to steal money from major corporations and banks.
Does a VPN protect against RAT
Not foolproof against DoS and DDoS
However, a VPN can't do much in a few scenarios. If the attacker has a backdoor on your system or has infected your machine with a Remote Access Trojan (RAT), they may be able to find your real IP address.
What will happen when a RAT is installed on your computer
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
Can rats jump through windows
Rats can easily enter through small gaps or cracks around windows. Seal any openings and check your window screen for holes. Sign-up to receive the latest information from Automatic Trap including discounts and flash sales!
What is an example of a rat spyware
Common examples of remote access Trojans. Back Orifice. This rootkit is one of the best-known examples of a RAT. A hacker group known as the Cult of the Dead Cow created Back Orifice to expose the security deficiencies of Microsoft's Windows OS.
How long does rat virus last
Survival of the virus for 2 or 3 days has been shown at normal room temperature. Exposure to sunlight will decrease the time of viability, and freezing temperatures will actually increase the time that the virus survives.
Is rat a malware
What is Remote Access Trojan (RAT) Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What kills rats permanently
Bait stations using rodenticides (rat poison) are effective ways to get rid of rats permanently.
How do I get rid of rats ASAP
So, what is the fastest way to get rid of rats Pest control is the most efficient method to get rid of rats quickly but the usage of mouse traps, snap traps, chemical baits, and live traps are all effective methods to get rid of rats as quickly and effectively as possible.
Is Trojan virus warning real
Is a Trojan spyware alert legitimate No, a Trojan spyware alert is a pop-up that aims to trick users into believing it's legitimate by pretending to be Windows or Apple. It will ask you to call a number to remove the threat so you can pay for unnecessary software or grant remote access to your laptop.
Are Trojans worse than viruses
Unlike viruses, Trojan Horses do not replicate themselves, but they can be just as destructive. Trojans also open a backdoor entry to your computer, giving command to malicious actor or allowing malicious users/programs access to your system. This leads to confidential and personal information being stolen.
Can police track down VPN
Can police track online purchases made with a VPN There is no way to track live, encrypted VPN traffic. That's why police or government agencies who need information about websites you visited have to contact your internet service provider (ISP for short), and only then your VPN provider.
How do hackers use RATs
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
How do you know if you have a rat virus
Symptoms of HPS usually first look like the flu, with fever, muscle aches, and fatigue. Later symptoms of HPS include shortness of breath, cough, and difficulty breathing. HPS can be fatal, so it's important to take these prevention tips with you anywhere that rodents may live.
Will a rat jump in your bed
If an extremely hefty, overweight, senior pet rat can jump onto a bed, you're practically ensured that a young, lean, muscular rat might do this without issue. As much as you don't want to think about a wild rat curling up in your bed, it is possible.
Will a rat jump on me
Unless they're domesticated, rats are afraid of humans. But if there is no way to escape, a cornered rat would not hesitate to attack a human. For example, the black rat is capable of jumping 70cm into the air. It can climb on a wall and jump on your face.
What do RATs do on your computer
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
How do you treat rat virus
Treatment is with penicillin or doxycycline. Rat-bite fever is transmitted to humans in up to 10% of rat bites. However, there may be no history of rat bite. Rat-bite fever is most commonly caused by rat bites but can be caused by the bite of any rodent or of a carnivore that preys on rodents.
What are the signs of a rat virus
Early symptoms are general and include fever, fatigue, and muscle pain. Other symptoms may include headache, nausea (a feeling of sickness in the stomach), vomiting, diarrhea (loose stool/poop) and dizziness.
How do you prevent RAT malware
How to Prevent Remote Access Trojan AttacksInstall an Anti-Malware Software Program.Harden Access Control.Implement Least Privilege.Monitor Unusual Behavior of Applications.Use an Intrusion Detection System.Update OS, Browser, and Other Commonly Used Software.Adopt Zero-Trust Model.Go through Cybersecurity Training.



