What is remote Trojan?
Summary of the Article: What is a Remote Access Trojan?
Remote access Trojans (RATs) are a type of malware that allows attackers to control an infected computer remotely. Once the RAT is running on a compromised system, the attacker can send commands and receive data back. Some examples of remote access Trojans include Sakula, KjW0rm, Dark Comet, AlienSpy, Heseber BOT, and Sub7. The primary difference between a Trojan and a remote access Trojan is that a Trojan is a tool that an organization still has control over, whereas a remote access Trojan allows an attacker to take control of the software. There are various commonly known remote access Trojans, such as SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy, as well as lesser-known ones like CyberGate, DarkComet, Optix, Shark, and VorteX Rat. Trojan viruses can affect both iPhones and Android devices, making them vulnerable to spyware, phishing attacks, and other threats. Trojan viruses not only steal personal information but also put users at risk of identity theft and cybercrimes. A Trojan horse virus is a type of malware that downloads onto a computer disguised as a legitimate program, and it is often used by attackers to gain unauthorized access to users’ systems. Additionally, Trojan viruses can potentially access a device’s camera and microphone, allowing cybercriminals to spy on users. It is possible to identify Trojan infections by looking for unfamiliar apps from unverified developers in the task manager. While Trojan viruses cannot spread through Wi-Fi alone, they can take advantage of network vulnerabilities to infect other devices.
Questions and Answers:
- What does a remote access Trojan do?
- What is an example of a remote access Trojan?
- What is the difference between a Trojan and a remote access Trojan?
- What are the most common remote access Trojans?
- Can a Trojan virus hack your phone?
- Can a Trojan steal your data?
- Is a Trojan a hacker code?
- Can a Trojan virus access the camera?
- Can a Trojan virus spy on you?
- How do I know if I have a Trojan virus?
- Can Trojan viruses spread through Wi-Fi?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
Common Remote Access Trojans include Sakula, KjW0rm, Dark Comet, AlienSpy, Heseber BOT, and Sub7.
The primary difference between a “trojan” and a “tool” is whether or not your organization still has control over the software, but determining that can be tricky.
Some well-known remote access Trojans include SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy, while others like CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Yes, spyware like Pegasus, trojans, phishing attacks, and unsafe Wi-Fi networks can affect both iPhones and Android devices.
Yes, Trojan viruses can steal personal information and put users at risk of identity theft and other cybercrimes.
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. It is often used by attackers to gain access to users’ systems.
Yes, cybercriminals can use Trojan horse malware to remotely control a device’s functions, including the camera and microphone.
Yes, Trojan horses are designed to spy on users’ online activity, control their devices, and steal sensitive data.
A common symptom of Trojan infection is the sudden appearance of unfamiliar apps from unverified developers in the task manager.
Trojan viruses cannot spread through Wi-Fi alone, but they can exploit network vulnerabilities to infect other devices.
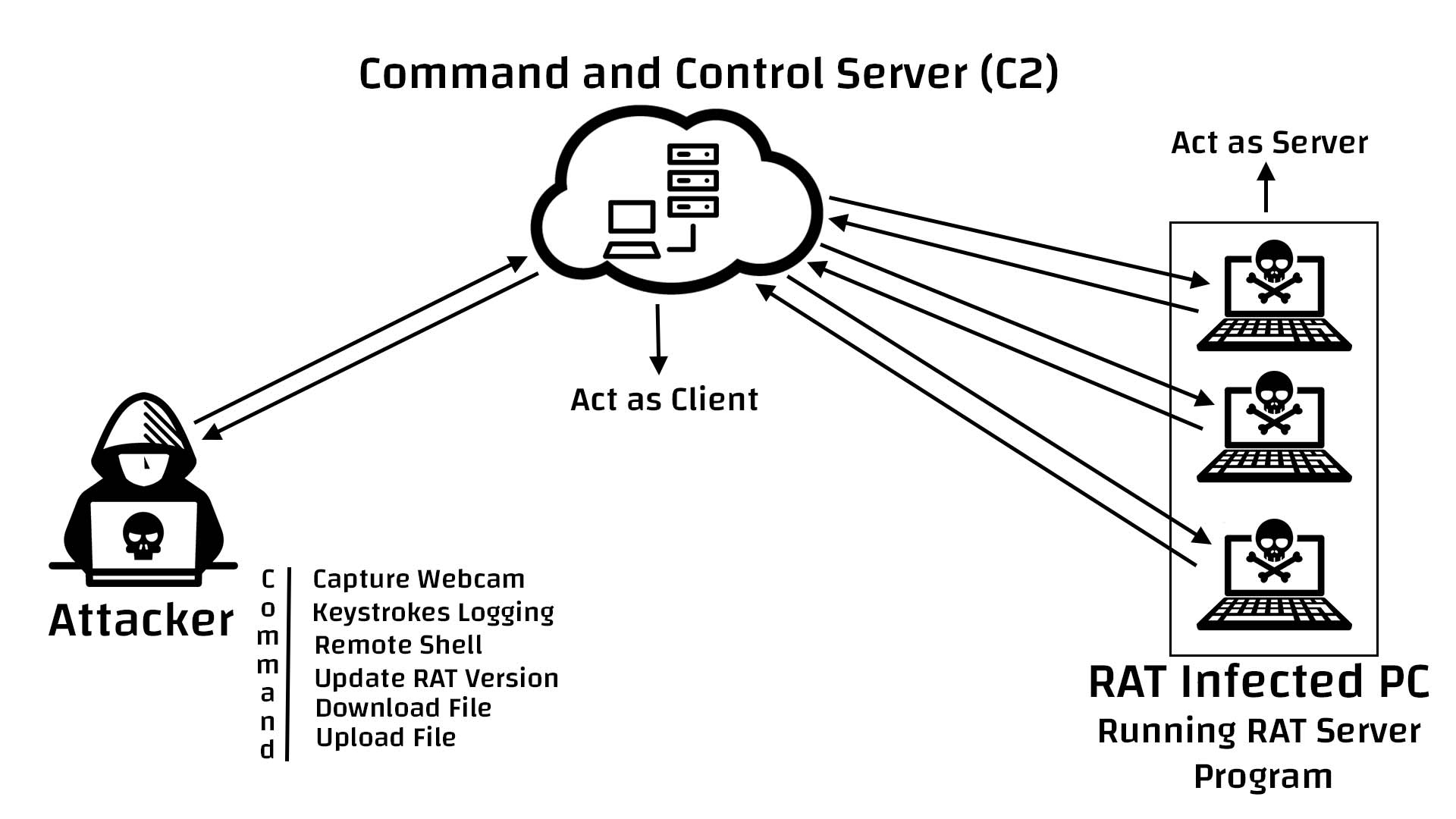
What does a remote access Trojan do
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
Cached
What is an example of remote access Trojan
Common Remote Access TrojansSakula. Sakula is a seemingly benign software with a legitimate digital signature, yet it allows attackers complete remote administration capabilities over a machine.KjW0rm.Havex.Agent.Dark Comet.AlienSpy.Heseber BOT.Sub7.
Cached
What is the difference between a Trojan and a remote access Trojan
RAT. Once an adversary gets their hands on it, a remote administration tool can become a remote access trojan. The primary difference between a “trojan” and a “tool” is whether or not your organization still has control over the software, but determining that can be tricky.
Cached
What are the most common remote access Trojans
There are a large number of Remote Access Trojans. Some are more well-known than others. SubSeven, Back Orifice, ProRat, Turkojan, and Poison-Ivy are established programs. Others, such as CyberGate, DarkComet, Optix, Shark, and VorteX Rat have a smaller distribution and utilization.
Cached
Can a Trojan virus hack your phone
Spyware like Pegasus, trojans (sometimes called “trojan viruses”), phishing attacks, and unsafe Wi-Fi networks are just some of the threats that can affect your iPhone or iPad. Jailbreaking your iPhone — removing Apple's built-in, manufacturer restrictions — makes it just as vulnerable to malware as an Android device.
Can a Trojan steal your data
If you've found yourself in this situation, or even thinking you are, there's a real possibility you could have a Trojan virus on your computer. Trojan viruses can not only steal your most personal information, they also put you at risk for identity theft and other serious cybercrimes.
Is a Trojan a hacker code
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. The delivery method typically sees an attacker use social engineering to hide malicious code within legitimate software to try and gain users' system access with their software.
Can a Trojan virus access camera
Cybercriminals can use so-called Trojan horse malware. You click on an attachment or download a piece of music or video infected with malware, and hey presto! – A cybercriminal can remotely control your PC's functions – including your camera and microphone and may even be able to record images and audio remotely.
Can a Trojan virus spy on you
A trojan horse, or trojan, is malware that invades your computer disguised as legitimate software. Cybercriminals use it to spy on your online activity, control your device, and steal your sensitive data.
How do I know if I have a Trojan virus
A common symptom of Trojan infection is the sudden appearance of apps you don't recall downloading or installing. If you notice an unfamiliar app from an unverified developer in your Windows Task Manager, there's a good chance that it is malicious software installed by a Trojan.
Can Trojan virus spread through WIFI
Trojan Attacks
A trojan attack tricks you into downloading malware hiding a virus that then tramples all over your phone, tablet, or computer. A router virus can ride inside a trojan, waiting to sniff out vulnerable public or home Wi-Fi networks to infect.
Are Trojans easily detected
To find it, the user must initiate a full computer scan with an anti-virus scanner. This should be able to identify all threats and inform the user of the name of the malware. In addition, the scanner usually recommends the necessary measures to completely remove the Trojan and the installed malware from the system.
How can I tell if my phone has a Trojan
7 signs your phone has a virusYour device feels physically hot. Your phone isn't built to support malware.Random messages are sent to your contacts.The device responds slowly.You find fraudulent charges on your accounts.The phone uses excess data.
Can a Trojan virus be removed
Trojan viruses can be removed in various ways. If you know which software contains the malware, you can simply uninstall it. However, the most effective way to remove all traces of a Trojan virus is to install antivirus software capable of detecting and removing Trojans.
Can Trojan virus be removed
You can remove some Trojans by disabling startup items on your computer which don't come from trusted sources. For the best results, first reboot your device into safe mode so that the virus can't stop you from removing it.
How do I know if someone is watching me through my camera
The following signs may indicate that someone is using your phone's camera to watch you:Suspicious background apps.Camera misbehaving.Odd files and inexplicably low storage space.Misbehaving indicator light.Battery draining fast.
How do you know if a camera is watching you
How Do You Know If a CCTV Security Camera Is OnObserve whether the security camera is moving to see if it is on.Check the status of the LEDs in the IP security cameras.Log in to your security camera software.Use electronic bug detectors.Know if a CCTV is recording from its power indicator.
Can a Trojan virus track you
Once a trojan horse is installed on your computer, it can spy on you, steal your personal information, and/or create backdoors that allow other hackers to do the same.
How do I find hidden malware on my phone
Check for Android malware using Play ProtectOpen the Play Store on the Android device you want to scan.Tap on your profile in the upper-right corner.Tap on Play Protect.Tap Scan.Tap on the option to remove any detected malware.
Can someone put a Trojan on my phone
Can a Trojan Virus Infect a Phone Yes, trojans can infect your mobile devices. The malware usually disguises itself within a convincing fake app. Unsuspecting users download this app from unofficial or pirate app markets by unsuspecting users.
Should I worry about a Trojan virus
Trojans can infect your computer and cause enormous problems before you even know what happened. Once a trojan gets onto your system, it can monitor your keyboard, install additional malware and cause a variety of other problems you simply don't want to face.
Can someone hack my phone and watch me through the camera
If a hacker installs spyware on your phone then there is a good chance they will be able to access your camera and turn it on/off as they please. They may also be able to access any photos or videos you have previously taken.
What is the code to know if someone is spying on your phone
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information's status and the number to which the information is transferred.
How do I find hidden listening devices
Download a Smartphone App
Some of the best apps for detecting hidden cameras and microphones include Hidden Camera Detector Free for Android and Hidden Spy Camera Detector for Apple. Most apps scan the area using an infrared scanner and/or visible light emitters.
Can a cell phone detect a hidden camera
Yes, a cell phone can detect a hidden camera. Download a hidden camera detector app. Once the app is installed, open it and scan the area for any hidden cameras. The app will then create an alert if any cameras are found.



