What is the difference between SAML and Kerberos?
Summary
In this article, we will explore the difference between SAML and Kerberos. We will cover their functionalities, authentication processes, and their respective use cases. Let’s dive in!
Does Kerberos support SAML?
In a Windows Active Directory (AD) environment, you can enable SAML single sign-on (SSO) to Tableau Server, along with Kerberos database delegation. This provides authorized users direct access to Tableau Server, as well as to the underlying data defined in their published workbooks and data sources.
What is the difference between SSO and Kerberos?
Kerberos is still the back-end technology. Kerberos excels at Single-Sign-On (SSO), which makes it much more usable in a modern internet-based and connected workplace. With SSO, you prove your identity once to Kerberos, and then Kerberos passes your TGT to other services or machines as proof of your identity.
What is the difference between SAP SSO Kerberos and SAML?
SAML 2.0 requires the use of an identity provider from an external product. SAP Single Sign-On offers an identity provider. During logon, Kerberos (or SPNego) authentication requires access to an issuing system (for example, Microsoft Active Directory).
Can Kerberos be used for SSO?
Kerberos is an authentication protocol that supports the concept of Single Sign-On (SSO). In the case of HTTP, support for Kerberos is usually provided using the term “SPNEGO” authentication mechanism.
Which authentication is used for Kerberos?
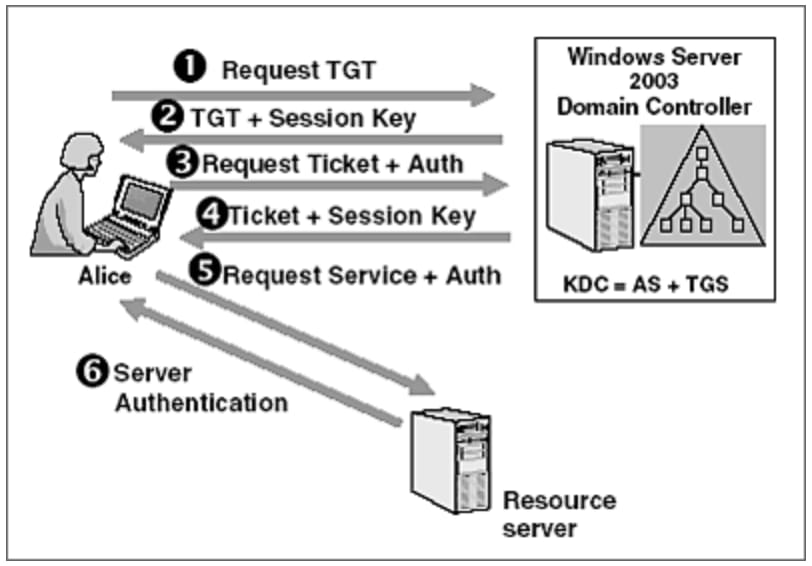
Kerberos uses symmetric key cryptography and a key distribution center (KDC) to authenticate and verify user identities.
Which type of protocol is Kerberos?
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users’ identities.
What type of authentication is Kerberos?
Kerberos uses symmetric key cryptography and a key distribution center (KDC) to authenticate and verify user identities. A KDC involves three aspects: A ticket-granting server (TGS) that connects the user with the service server (SS) A Kerberos database that stores the password and identification of all verified users.
What is an example of Kerberos?
Kerberos implementations are used on a number of operating systems and networking systems to verify user accounts. Examples include: Amazon Web Services (AWS) Google Cloud.
Is SAML and SSO the same?
The difference between SAML and SSO: However, while they’re related, they’re not the same. SAML is the standard through which SPs and IdPs communicate with each other to verify credentials. SSO is an authentication process intended to simplify access to multiple applications with a single set of credentials.
What type of authentication is SAML?
SAML is an open standard used for authentication. Based upon the Extensible Markup Language (XML) format, web applications use SAML to transfer authentication data between two parties – the identity provider (IdP) and the service provider (SP).
What is the primary purpose of Kerberos?
Kerberos is used to authenticate clients and servers over a non-secure network. It provides a secure method of authentication by using encryption keys and a trusted third-party authentication server.
Does Kerberos support SAML
In a Windows Active Directory (AD) environment, you can enable SAML single sign-on (SSO) to Tableau Server, along with Kerberos database delegation. This provides authorized users direct access to Tableau Server, as well as to the underlying data defined in their published workbooks and data sources.
Cached
What is the difference between SSO and Kerberos
Kerberos is still the back-end technology. Kerberos excels at Single-Sign-On (SSO), which makes it much more usable in a modern internet based and connected workplace. With SSO you prove your identity once to Kerberos, and then Kerberos passes your TGT to other services or machines as proof of your identity.
Cached
What is the difference between SAP SSO Kerberos and SAML
SAML 2.0 requires the use of an identity provider from an external product. SAP Single Sign-On offers an identity provider. During logon, Kerberos (or SPNego) authentication requires access to an issuing system (for example, Microsoft Active Directory).
Cached
Can Kerberos be used for SSO
Kerberos: Kerberos is an authentication protocol that supports the concept of Single Sign-On (SSO). In the case of HTTP, support for Kerberos is usually provided using the term "SPNEGO" authentication mechanism.
Cached
Which authentication is used for Kerberos
Kerberos uses symmetric key cryptography and a key distribution center (KDC) to authenticate and verify user identities.
Which type of protocol is Kerberos
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users' identities.
What type of authentication is Kerberos
Kerberos uses symmetric key cryptography and a key distribution center (KDC) to authenticate and verify user identities. A KDC involves three aspects: A ticket-granting server (TGS) that connects the user with the service server (SS) A Kerberos database that stores the password and identification of all verified users.
What is an example of Kerberos
Kerberos Uses
Kerberos implementations are used on a number of operating systems and networking systems to verify user accounts. Examples include: Amazon Web Services (AWS) Google Cloud.
Is SAML and SSO the same
The difference between SAML and SSO
However, while they're related, they're not the same. SAML is the standard through which SPs and IdPs communicate with each other to verify credentials. SSO is an authentication process intended to simplify access to multiple applications with a single set of credentials.
What type of authentication is SAML
SAML is an open standard used for authentication. Based upon the Extensible Markup Language (XML) format, web applications use SAML to transfer authentication data between two parties – the identity provider (IdP) and the service provider (SP).
What is the primary purpose of Kerberos
Kerberos is used to authenticate entities requesting access to network resources, especially in large networks to support SSO. The protocol is used by default in many widely used networking systems. Some systems in which Kerberos support is incorporated or available include the following: Amazon Web Services.
Is LDAP authentication same as Kerberos
While Kerberos is a ticket-based authentication protocol for trusted hosts on untrusted networks, Lightweight Directory Access Protocol (LDAP) is an authentication protocol for accessing server resources over an internet or intranet.
What are the 3 main parts of Kerberos
Key Distribution Center (KDC): In a Kerberos environment, the authentication server logically separated into three parts: A database (db), the Authentication Server (AS), and the Ticket Granting Server (TGS). These three parts, in turn, exist in a single server called the Key Distribution Center.
What is the purpose of Kerberos
What is Kerberos used for Kerberos is used to authenticate entities requesting access to network resources, especially in large networks to support SSO. The protocol is used by default in many widely used networking systems.
What is Kerberos in simple terms
In our world, Kerberos is the computer network authentication protocol initially developed in the 1980s by Massachusetts Institute of Technology (MIT) computer scientists. The idea behind Kerberos is to authenticate users while preventing passwords from being sent over the internet.
What are the disadvantages of SAML
SAML is a complex protocol that comes with several drawbacks and limitations. It requires a lot of configuration and coordination between the IdP and the SP, as well as XML parsing, encryption, signing, and validation. Debugging and troubleshooting can be difficult when dealing with multiple IdPs or SPs.
What are three key components of a SAML system
SAML's standards provide a request/response for exchanging XML messages between these roles. The standard specifies four main components: profiles, assertions, protocol, and binding.
What are two 2 benefits of Kerberos
Kerberos authentication offers several advantages over other access control methods, such as mutual authentication, which allows both the client and the server to verify each other's identity. It also reduces the risk of password theft, as passwords are never sent over the network in plain text.
Is Active Directory LDAP or Kerberos
Does Active Directory use LDAP or Kerberos Active Directory supports both LDAP and Kerberos for authentication, and more often than not, these two protocols are used together. Kerberos is the default authentication and authorisation protocol used by Active Directory as it is more secure.
How do you explain Kerberos
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users' identities.
What is SAML mostly used for
SAML is an open standard used for authentication. Based upon the Extensible Markup Language (XML) format, web applications use SAML to transfer authentication data between two parties – the identity provider (IdP) and the service provider (SP).
What is the main drawback of using Kerberos
The primary weakness of Kerberos is that the KDC stores the keys of all principals (clients and servers). A compromise of the KDC (physical or electronic) can lead to the compromise of every key in the Kerberos realm. The KDC and TGS are also single points of failure: if they go down, no new credentials can be issued.
What is the disadvantage of Kerberos
Tickets in Kerberos have a limited period. If the ticket gets stolen, it is hard to reuse it because of strong authentication needs. Passwords are never sent over the network unencrypted.
Is LDAP and Kerberos the same
Kerberos is used to manage credentials securely (authentication) while LDAP is used for holding authoritative information about the accounts, such as what they're allowed to access (authorization), the user's full name and uid.
What is an example for Kerberos
Kerberos Uses
Kerberos implementations are used on a number of operating systems and networking systems to verify user accounts. Examples include: Amazon Web Services (AWS) Google Cloud.