What is UTM appliance?
Summary of the Article: What is UTM Appliance?
Unified Threat Management (UTM) appliances are powerful hardware devices that provide network systems with antivirus solutions and comprehensive data protection. They offer multiple security functions in a single appliance, eliminating the need for standalone products, and simplifying security management. UTM appliances play a crucial role in securing networks and protecting users from security threats.
Key Points:
1. What is the difference between UTM appliance and firewalls?
UTM appliances are only available as hardware devices and provide network systems with antivirus solutions and data protection. Firewalls, on the other hand, can be both hardware and software solutions and focus primarily on controlling network traffic.
2. What is the role of UTM?
UTM systems consolidate multiple security functions into a single appliance, providing comprehensive protection against various cyber threats. They simplify security visibility and management, eliminating the need for separate security products.
3. Is UTM hardware or software?
UTM can be either a hardware or software solution, offering firewall capabilities integrated with other security services such as intrusion prevention systems (IPS).
4. What is UTM in a router?
Originally known as Unified Threat Management (UTM), these capabilities are now commonly referred to as Next-Generation Firewalls (NGFW). They provide multiple security features and services in a single device or service on the network, protecting users from various security threats.
5. What are the two types of UTM parameters?
The two types of UTM parameters are utm_source and utm_medium. Utm_source identifies the traffic source, and utm_medium specifies the medium used for the URL, such as CPC or a newsletter. These parameters help track and analyze campaign performance.
6. Is UTM a next-generation firewall?
UTM appliances provide multiple layers of network protection, including next-generation firewalls, antivirus software, intrusion and detection prevention systems (IDPS), website and spam filtering, and virtual private network (VPN) functionality.
7. What does UTM stand for?
UTM stands for “Universal Transverse Mercator,” which is a coordinate grid system used for plane maps. The UTM system consists of 60 zones, each 6-degrees of longitude in width.
8. What is the benefit of UTM?
UTM allows for quicker detection of incoming security threats as it operates on a centralized system that is regularly updated and offers a consolidated platform for detecting multifaceted threats.
9. What is UTM platform?
UTM platform refers to a digital platform for collecting and processing ultrasonic thickness measurements (UTM) data and reports. It enables efficient data collection and reporting for ship owners, UTM companies, and surveyors.
10. What is UTM in Windows?
UTM is a free virtualization software that allows the running of Windows/ARM on Apple Silicon Macs.
11. How do I connect to UTM?
To connect to UTM, visit Google’s free Campaign URL Builder page, insert the website URL, and campaign information. Create a unique UTM tracking code (campaign URL) for every ad or link and use these tracking codes in your marketing campaigns.
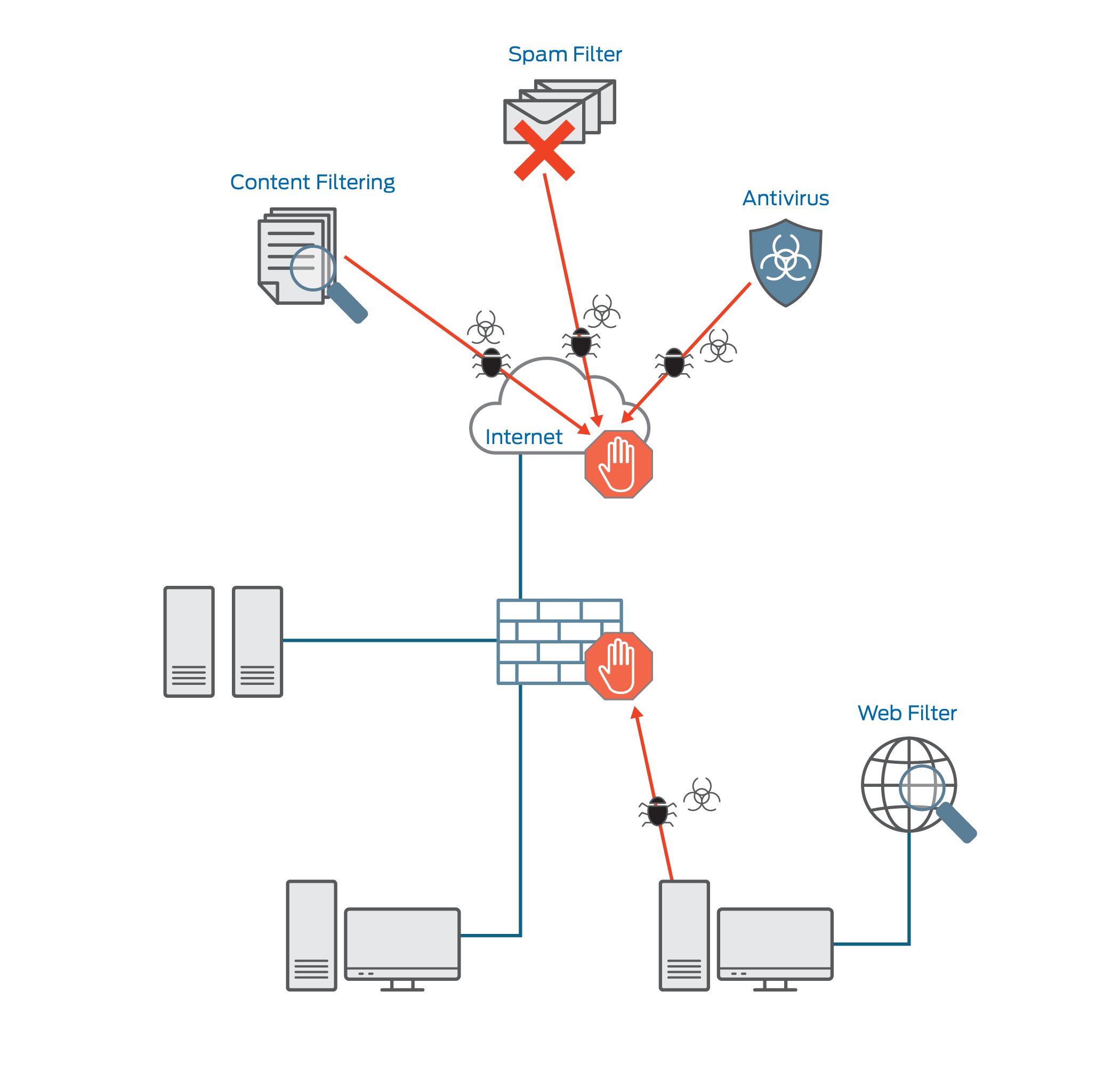
What is the difference between UTM appliance and firewalls
However, a significant difference between UTM vs firewall is that appliances are only available as hardware. It provides network systems with antivirus solutions and prevents appliance reporting. UTM appliances are way bigger and much more powerful than UTM firewalls for data protection and privacy.
Cached
What is the role of UTM
What is Unified Threat Management (UTM) Unified threat management (UTM) systems consolidate multiple security functions into a single appliance. By doing so, UTM eliminates the need for sprawling standalone products and simplifies security visibility and management.
Cached
Is UTM hardware or software
Unified threat management (UTM) is a universal software or hardware firewall solution integrated with an IPS (intrusion prevention system) and other security services.
What is UTM in router
Originally called unified threat management (UTM), these capabilities better known as a Next-Generation Firewall (NGFW) today, provide multiple security features and services in a single device or service on the network, protecting users from security threats in a simplified way.
Cached
What are the two types of UTM
The five types of UTM parametersutm_source. This tag identifies the source of your traffic (e.g. Facebook, search engine, etc.).utm_medium. This UTM code specifies the medium, like CPC or newsletter, for example.utm_campaign. This parameter indicates the campaign that the URL is part of.utm_content.utm_term.
Is UTM a next generation firewall
A UTM appliance provides several layers of network protection. These layers consist of next-generation firewalls, antivirus software, intrusion and detection prevention systems (IDPS), website and spam filtering, and virtual private network (VPN) functionality.
What does UTM stand for
UTM is the acronym for Universal Transverse Mercator, a plane coordinate grid system named for the map projection on which it is based (Transverse Mercator). The UTM system consists of 60 zones, each 6-degrees of longitude in width.
What is benefit of UTM
UTM allows for the quicker detection of incoming security threats. This is because the centralized system is more up to date, operates faster, and offers a common consolidated platform where multi-faceted threats can be detected.
What is UTM platform
A digital platform for collecting and processing ultrasonic thickness measurements (UTM) data and reports. Bureau Veritas' UTM Data Platform is a fully digital web platform that enables ship owners, UTM companies and surveyors to efficiently collect, process and report UTM data.
What is UTM in Windows
UTM is a free virtualization software that runs Windows/ARM on Apple Silicon Macs.
How do I connect to UTM
Visit Google's free Campaign URL Builder page. Insert the website URL and campaign information. Create a unique UTM tracking code (aka campaign URL) for every ad or link. Use the UTM tracking codes in your marketing campaigns.
What is a UTM example
The “source” UTM tag = the referrer (Facebook, Twitter, LinkedIn, YouTube, etc.) The “medium” UTM tag = how the traffic gets to you (for most social media links, this will just be “social”) The “campaign” UTM tag = why the traffic is coming to you (launch, persona, promotion, etc.)
What is UTM and how is it used
UTM or Urchin Tracking Module is a simple code that can be attached to any URL to generate Google Analytics data for digital campaigns. Specific to Google Analytics, UTM helps track the progress of the campaign on all online platforms.
What does UTM stand for in firewall
Unified threat management
Unified threat management (UTM) refers to when multiple security features or services are combined into a single device within your network. Using UTM, your network's users are protected with several different features, including antivirus, content filtering, email and web filtering, anti-spam, and more.
What is the difference between UTM and VPN
UTM refers to the ability of a single device to perform the functions of an NGFW, firewall and virtual private network (VPN), while an NGFW is a network security platform that provides a gateway between internal and external networks.
What is an example of a UTM coordinate system
For locations north of the equator, give the zone number, the letter “N”, and the distance from the central meridian in meters. For example, Port-au-Prince, Haiti, which is located at lat/long 18.5425*, – 72.3386*, has UTM coordinates of 18N 780950E 2052283N.
What is the disadvantage of UTM
Components within an UTM appliance may not have settings as granular, or rules as powerful as dedicated appliances. There is also the possibility of degraded performance when the UTM appliance handles a large of number of applications / clients with many UTM features enabled.
What is the disadvantage of using a UTM
Some of the key disadvantages of UTM tagging include: Limited accuracy: UTM tags rely on the visitor clicking on a specific link that contains the UTM tag. If a visitor comes to your site from a different source, the UTM tag will not accurately reflect the source of the traffic.
What is UTM for dummies
UTM (Urchin Tracking Module) parameters, also called UTM tags or UTM code, are small bits of code you can add at the end of your normal URL to track the traffic that clicks that specific link.
How do I turn on wifi on UTM
Configuration: Connect LAN port of wifi router to network switch. You can also connect LAN port of router to UTM LAN port directly if switch is not available. Leave WAN port of WIFI router disconnected. Assign a LAN IP address to wifi router. Disable DHCP feature of wifi router. Now you are ready to go.
Does UTM have WIFI
University of Toronto Campus Wi-Fi
The campus wireless network is available to faculty, students, staff and guests across all three campuses.
What do UTM terms mean
A UTM (Urchin Tracking Module) code is a snippet of text added to the end of a URL to track the metrics and performance of a specific digital marketing campaign. UTM codes can contain up to five parameters: Campaign, source, medium, content, and term.
What is the difference between UTM and next generation firewall
They are both used to protect your network from new and emerging threats. However, they differ in a few minor instances. For instance, with UTM, you may have pre-determined services added that you do not need. NGFW, on the other hand, allows you to choose the services you want to integrate with your network.
What is the advantage of using UTM
UTM allows for the quicker detection of incoming security threats. This is because the centralized system is more up to date, operates faster, and offers a common consolidated platform where multi-faceted threats can be detected.
What are the disadvantages of UTM firewall
Components within an UTM appliance may not have settings as granular, or rules as powerful as dedicated appliances. There is also the possibility of degraded performance when the UTM appliance handles a large of number of applications / clients with many UTM features enabled.



