Which advanced core PAS solution detects Kerberos?
Summary of the Article: Kerberos Authentication in Active Directory
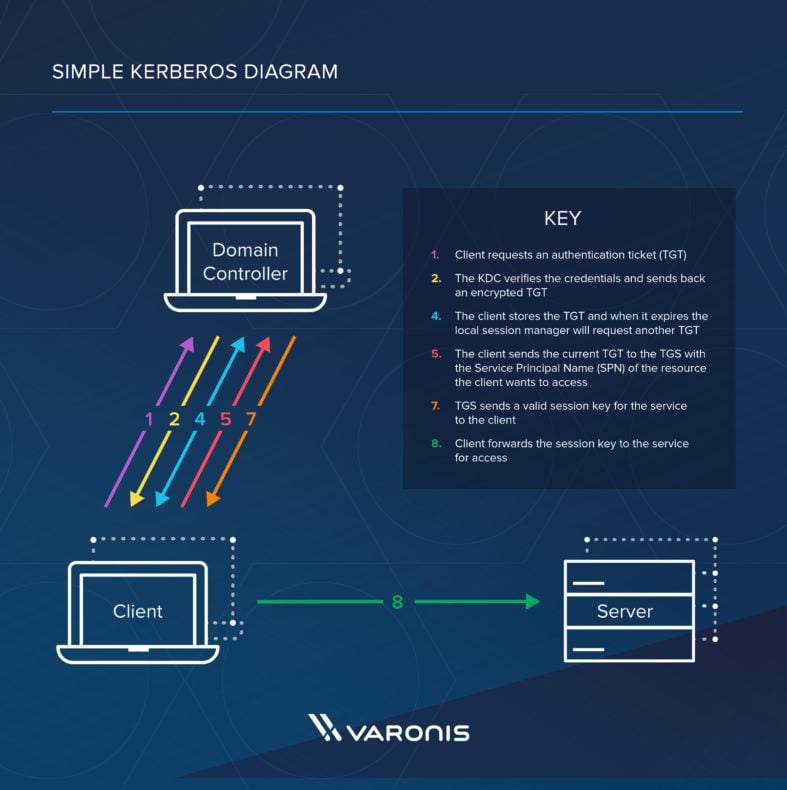
Kerberos authentication is a widely used method for verifying user identities in Active Directory. It employs symmetric key cryptography and a Key Distribution Center (KDC) to authenticate users. Monitoring Kerberos authentication events can be done through the Event Viewer in Windows. LDAP and Kerberos are not the same; while Kerberos is a ticket-based authentication protocol, LDAP is used for accessing server resources.
Implementing Kerberos authentication in Active Directory involves opening Active Directory Users and Computers, searching for the service account used to create the Service Principal Name (SPN), and configuring the Delegation tab. Wireshark can be used to check Kerberos authentication by selecting the KRB5 protocol preferences and decrypting Kerberos blobs.
The Kerberos Configuration Manager is a helpful tool for troubleshooting Kerberos-related connectivity issues with SQL Server. In Active Directory, Kerberos and LDAP work together, with Kerberos managing secure credentials and LDAP holding authoritative account information. Kerberos is used in various technologies, such as Microsoft Windows, Apple OS, FreeBSD, UNIX, and Linux.
Questions about Kerberos Authentication:
1. Which authentication is used for Kerberos?
– Kerberos uses symmetric key cryptography and a Key Distribution Center (KDC) for authentication and user identity verification.
2. How do I monitor Kerberos authentication?
– The Event Viewer can be used to view Kerberos authentication events by navigating to Windows log ⟶ Security.
3. Which component in Active Directory performs authentication for Kerberos?
– Authentication in Kerberos requires the use of a Key Distribution Center (KDC), typically present in Active Directory Domain Services (AD DS).
4. What software uses Kerberos?
– Kerberos is supported by major computer operating systems like Microsoft Windows, Apple macOS, FreeBSD, and Linux. Microsoft has used Kerberos as the default authentication method in Windows since Windows 2000, integrated with Windows Active Directory (AD) service.
5. Is LDAP authentication the same as Kerberos?
– No, LDAP is an authentication protocol for accessing server resources, while Kerberos is a ticket-based authentication protocol used for trusted hosts on untrusted networks.
6. How can I implement Kerberos authentication in Active Directory?
– To implement Kerberos authentication in Active Directory, you need to open Active Directory Users and Computers, search for the service account used to create the Service Principal Name (SPN), and configure the Delegation tab.
7. How can I check Kerberos authentication in Wireshark?
– In Wireshark, you can check Kerberos authentication by selecting the KRB5 protocol preferences, browsing and selecting the keytab file of your Kerberos service, and trying to decrypt Kerberos blobs.
8. What is the Kerberos troubleshooting tool?
– The Kerberos Configuration Manager for SQL Server is a diagnostic tool specifically designed to troubleshoot Kerberos-related connectivity issues with SQL Server, SQL Server Reporting Services, and SQL Server Analysis Services.
9. How do Kerberos and LDAP work together in Active Directory?
– LDAP and Kerberos work together in Active Directory where Kerberos handles secure credential management (authentication) and LDAP holds authoritative information about accounts, including authorization and user details like full name and uid.
10. What technologies rely on Kerberos?
– Kerberos is the default authorization technology used in Microsoft Windows Active Directory, and it is also implemented in various other technologies like Apple OS, FreeBSD, UNIX, and Linux.
11. Is Kerberos used in Active Directory?
– Yes, Kerberos is the native authentication protocol used in Active Directory, and understanding its functioning is crucial for comprehending advanced networking concepts like authentication and delegation.
Which authentication is used for Kerberos
Kerberos uses symmetric key cryptography and a key distribution center (KDC) to authenticate and verify user identities.
How do I monitor Kerberos authentication
Steps to view Kerberos authentication events using Event ViewerPress Start, search for Event Viewer, and click to open it.In the Event Viewer window, on the left pane, navigate to Windows log ⟶ Security.Here, you will find a list of all the Security Events that are logged in the system.
Which component in Active Directory performs authentication for Kerberos
Authentication via Kerberos requires the use of a Key Distribution Center (KDC). This is typically a service running on all Domain Controllers (DCs) as part of Active Directory Domain Services (AD DS).
What software uses Kerberos
Kerberos support is built in to all major computer operating systems, including Microsoft Windows, Apple macOS, FreeBSD and Linux. Since Windows 2000, Microsoft has used the Kerberos protocol as the default authentication method in Windows, and it is an integral part of the Windows Active Directory (AD) service.
Is LDAP authentication same as Kerberos
While Kerberos is a ticket-based authentication protocol for trusted hosts on untrusted networks, Lightweight Directory Access Protocol (LDAP) is an authentication protocol for accessing server resources over an internet or intranet.
How to implement Kerberos authentication in Active Directory
Open Active Directory Users and Computers. Search for the service account which was used to create the Service Principal Name (SPN). Navigate to the Delegation tab. Select Trust this user for delegation to any service (Kerberos only).
How do I check Kerberos authentication in Wireshark
In Wireshark, click Edit > Preferences > Protocols > KRB5. Click Browse, and select the keytab file of your Kerberos service. Select Try to decrypt Kerberos blobs, and click Apply. Click OK.
What is the Kerberos troubleshooting tool
The Kerberos Configuration Manager for SQL Server is a diagnostic tool that helps troubleshoot Kerberos related connectivity issues with SQL Server, SQL Server Reporting Services, and SQL Server Analysis Services.
How Kerberos and LDAP work together in Active Directory
LDAP and Kerberos together make for a great combination. Kerberos is used to manage credentials securely (authentication) while LDAP is used for holding authoritative information about the accounts, such as what they're allowed to access (authorization), the user's full name and uid.
What technologies rely on Kerberos
What is Kerberos Kerberos authentication is currently the default authorization technology used by Microsoft Windows, and implementations of Kerberos exist in Apple OS, FreeBSD, UNIX, and Linux.
Is Kerberos used in Active Directory
Kerberos is the native authentication protocol in Active Directory, and it's essential to understand how it works to get a grasp of more advanced concepts in networking such as authentication and delegation.
Is Active Directory LDAP or Kerberos
Does Active Directory use LDAP or Kerberos Active Directory supports both LDAP and Kerberos for authentication, and more often than not, these two protocols are used together. Kerberos is the default authentication and authorisation protocol used by Active Directory as it is more secure.
Can Kerberos and LDAP work together
LDAP and Kerberos together make for a great combination. Kerberos is used to manage credentials securely (authentication) while LDAP is used for holding authoritative information about the accounts, such as what they're allowed to access (authorization), the user's full name and uid.
Does Active Directory support Kerberos
Kerberos is the native authentication protocol in Active Directory, and it's essential to understand how it works to get a grasp of more advanced concepts in networking such as authentication and delegation.
How Kerberos and LDAP work together
LDAP and Kerberos together make for a great combination. Kerberos is used to manage credentials securely (authentication) while LDAP is used for holding authoritative information about the accounts, such as what they're allowed to access (authorization), the user's full name and uid.
How do I know if my authentication is NTLM or Kerberos
If you need to identify what is being used at this moment the only way to recognize this is from the logs at log level 4. Once Kerberos authentication is enabled in EasySSO settings – the server and the browser will start exchanging "Negotiate" headers.
How to check Kerberos ticket in CMD
At a command prompt on your Windows machine, typing klist will display information about the Kerberos tickets on the machine.
How to check Kerberos Wireshark
In Wireshark, click Edit > Preferences > Protocols > KRB5. Click Browse, and select the keytab file of your Kerberos service. Select Try to decrypt Kerberos blobs, and click Apply. Click OK.
How is Kerberos a solution to network security problems
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users' identities.
What are the three servers used in Kerberos
Key Distribution Center (KDC): In a Kerberos environment, the authentication server logically separated into three parts: A database (db), the Authentication Server (AS), and the Ticket Granting Server (TGS). These three parts, in turn, exist in a single server called the Key Distribution Center.
Does Kerberos rely on DNS
All machines in your domain that will participate in your Kerberos realm need to have working DNS entries, both forward and reverse. This means that, for every machine, a DNS entry exists that maps the hostname to an IP address, and a reverse entry exists for that IP address mapping it back to the original hostname.
Does Active Directory use LDAP or Kerberos
Active Directory (AD) supports both Kerberos and LDAP – Microsoft AD is by far the most common directory services system in use today. AD provides Single-SignOn (SSO) and works well in the office and over VPN.
How do I enable Kerberos in Active Directory
Open Active Directory Users and Computers. Search for the service account which was used to create the Service Principal Name (SPN). Navigate to the Delegation tab. Select Trust this user for delegation to any service (Kerberos only).
Does Kerberos use NTLM
NTLM was replaced as the default authentication protocol in Windows 2000 by Kerberos. However, NTLM is still maintained in all Windows systems for compatibility purposes between older clients and servers.
How do I change my authentication from NTLM to Kerberos
Steps To Setup Kerberos For Windows Authentication :Open Active Directory Users and Computers.Search for the service account which was used to create the Service Principal Name (SPN).Navigate to the Delegation tab.Select Trust this user for delegation to any service (Kerberos only).



