Which best practices can help defend against social engineering attacks?
Summary of the Article
Best Practices to Prevent Social Engineering Attacks:
- Set spam filters to high
- Never use the same password for different accounts
- Use two-factor or multi-factor authentication
- When in doubt, change passwords right away
- Educate employees
Questions and Answers
1. What are the three best practices that can help defend against social engineering attacks?
Training and educating organizational personnel is considered the best defense against social engineering attacks.
2. What is a way to protect against social engineering?
The best way is to utilize another method of communication different from where the message is from – like
texting the person to see if they emailed you an urgent message or that was from an attacker. Better be safe than
sorry! Research the sources. Always be careful of any unsolicited messages.
3. Which of the following provides the best protection against social engineering?
One of the best methods of defense against social engineering is placing limits on the access each team member
has in the system. Controlling the entirety of the system is much more manageable when only one component is under
threat.
4. What are the three key prevention measures of cyber attacks?
- Turn on Multifactor Authentication.
- Update Your Software.
- Think Before You Click.
- Use Strong Passwords.
5. What are the three methods used in social engineering?
- Pretexting social engineering attack.
- Phishing attack.
- Baiting attack.
6. What is a good way to reduce the chance of a successful social engineering attack?
Setting up a rogue access point is a good way to prevent social engineering attacks.
7. What is a social engineering attack?
The use of persuasion or influence to deceive personnel into divulging confidential information or allowing the
adversary to perform unauthorized actions. It relies on human weaknesses such as the willingness to help and
unwillingness to question authority.
8. Which of the following would most effectively reduce social engineering incidents?
Social engineering can best be mitigated through periodic security awareness training for users who may be the
target of such an attempt.
9. Which of the following are examples of social engineering attacks?
- Phishing
- Spear Phishing
- Baiting
- Malware
- Pretexting
- Quid Pro Quo
- Tailgating
- Vishing
10. Which of the following provides the best countermeasure against social engineering attacks?
Raising awareness and educating employees is considered to be one of the best countermeasures against social
engineering. Organizations can conduct regular training sessions for their employees, which cover various aspects
of social engineering attacks such as phishing, pretexting, baiting, etc.
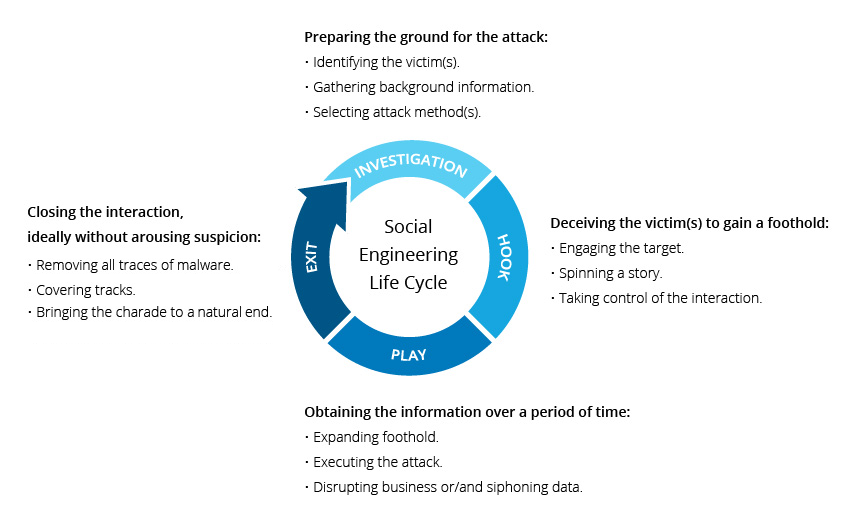
What are the three best practices can help defend against social engineering attack
Best Practices to Prevent Social Engineering AttacksSet spam filters to high. Every email program has spam filters.Never use the same password for different accounts.Use two-factor or multi-factor authentication.When in doubt, change passwords right away.Educate employees.
Cached
What is the best defense against a social engineering attack quizlet
Training and educating organizational personnel is considered the best defense against social engineering attacks.
What is a way to protect against social engineering
The best way is to utilize another method of communication different from where the message is from – like texting the person to see if they emailed you an urgent message or that was from an attacker. Better be safe than sorry! Research the sources. Always be careful of any unsolicited messages.
Cached
Which of the following provides the best protection against social engineering
One of the best methods of defense against social engineering is placing limits on the access each team member has in the system. Controlling the entirety of the system is much more manageable when only one component is under threat.
What are the 3 key prevention measures of cyber attacks
4 Things to Keep You Cyber SafeTurn on Multifactor Authentication. Implement multifactor authentication on your accounts and make it significantly less likely you'll get hacked.Update Your Software. Update your software.Think Before You Click. Think before you click.Use Strong Passwords.
What are the three methods used in social engineering
Types of social engineering attacksPretexting social engineering attack. Pretexting is a sophisticated social engineering technique where the attacker collects information through cleverly-crafted lies in the form of a story or pretext.Phishing attack.Baiting attack.
What is a good way to reduce the chance of a successful social engineering attack quizlet
Setting up a rogue access point is a good way to prevent social engineering attacks.
What is a social engineering attack quizlet
A: The use of persuasion or influence to deceive personnel into divulging confidential information or allowing the adversary to perform unauthorized actions. It relies on human weaknesses such as the willingness to help and unwillingness to question authority.
Which of the following would most effectively reduce social engineering incidents
Social engineering can best be mitigated through periodic security awareness training for users who may be the target of such an attempt.
Which of the following are examples of social engineering attacks
9 Most Common Examples of Social Engineering AttacksPhishing.Spear Phishing.Baiting.Malware.Pretexting.Quid Pro Quo.Tailgating:Vishing.
Which of the following provides the best countermeasure against social engineering attacks
Raising awareness and educating employees is considered to be one of the best countermeasures against social engineering. Organizations can conduct regular training sessions for their employees, which cover various aspects of social engineering attacks such as phishing, pretexting, baiting, etc.
Which of the following is the best example of social engineering
The most common form of social engineering attack is phishing. Phishing attacks exploit human error to harvest credentials or spread malware, usually via infected email attachments or links to malicious websites.
What are the three 3 principles of cyber defense
The CIA triad refers to an information security model made up of the three main components: confidentiality, integrity and availability.
What are the 5 best methods used for cyber security
10 steps to an effective approach to cyber securityRisk management regime.Secure configuration.Network security.Managing user privileges.User education and awareness.Incident management.Malware prevention.Monitoring.
What are the four types of social engineering methods
These are phishing, pretexting, baiting, quid pro quo, tailgating and CEO fraud.Phishing. Phishing is the most common type of social engineering attack.Pretexting.Baiting.Quid Pro Quo.Tailgating.CEO Fraud.
What is the best method of social engineering
Phishing. As one of the most popular social engineering attack types, phishing scams are email and text message campaigns aimed at creating a sense of urgency, curiosity or fear in victims.
Which of the following tactics is used in social engineering attacks
The most common form of social engineering attack is phishing. Phishing attacks exploit human error to harvest credentials or spread malware, usually via infected email attachments or links to malicious websites.
Which three actions are examples of a social engineering attack
The following are the five most common forms of digital social engineering assaults.Baiting. As its name implies, baiting attacks use a false promise to pique a victim's greed or curiosity.Scareware. Scareware involves victims being bombarded with false alarms and fictitious threats.Pretexting.Phishing.Spear phishing.
Which of the following is an example of a social engineering attack
The most common form of social engineering attack is phishing. Phishing attacks exploit human error to harvest credentials or spread malware, usually via infected email attachments or links to malicious websites.
What are the most commonly used and successful techniques of social engineering
Phishing is the most common type of social engineering attack, typically using spoofed email addresses and links to trick people into providing login credentials, credit card numbers, or other personal information.
Which of the following reduces the potential impact of social engineering attacks
Which of the following reduces the potential impact of social engineering attacks Explanation: Because social engineering is based on deception of the user, the best countermeasure or defense is a security awareness program.
What are the 5 social engineering attacks
These are phishing, pretexting, baiting, quid pro quo, tailgating and CEO fraud.Phishing. Phishing is the most common type of social engineering attack.Pretexting.Baiting.Quid Pro Quo.Tailgating.CEO Fraud.
What is the most effective way to detect and stop social engineering attacks
Penetration Testing. The most effective approach among the ways to prevent social engineering attacks is conducting a pen-test to detect and try to exploit vulnerabilities in your organization.
What is the best countermeasure against social engineering quizlet
The best countermeasure to social engineering is user awareness training.
What two security measures will protect the workplace from social engineering attacks
Adopt proper defense systems, such as spam filters, anti-virus software, and a firewall, and keep all systems updated. Social network users should trust no one and reveal only a limited amount of information.



