Why is PAM needed?
Why is PAM solution needed?
PAM helps organizations protect against the accidental or deliberate misuse of privileged access by streamlining the authorization and monitoring of privileged users. Controlling and monitoring privileged user access to your most critical data and systems is the best way to prevent attacks.
What is a PAM and why is it important?
PAM provides administrators with the functionality, automation, and reporting they need to manage privileged accounts. In addition, it supports the principle of least privilege as it allows for the necessary management and oversight to mitigate the risk of accounts that have capabilities beyond the standard user.
What are the risks of not having PAM?
Without a PAM solution, organizations may struggle to gain visibility into the access and permissions of their employees and third parties. This can make it difficult to identify potential security risks and take steps to mitigate them.
What is the business value of privileged access management?
Through PAM, organizations can easily detect and monitor suspicious activities that could put customer and company data at risk. It allows organizations to establish a comprehensive risk management strategy, ensure regulatory adherence, and avoid hefty sanctions due to non-compliance.
How does PAM work?
PAM software and tools work by gathering the credentials of privileged accounts, also known as system administrator accounts, into a secure repository to isolate their use and log their activity. The separation is intended to lower the risk of admin credentials being stolen or misused.
What is the difference between IAM and PAM?
While IAM identifies each user and allows them access to an array of applications and services, PAM manages access and user’s actions on highly sensitive systems that are often limited to those with administrative privileges. This difference also means the level of risk each system manages is vastly different.
What is PAM for dummies?
Privileged Access Management for Dummies is written for IT and systems administrators, along with security professionals responsible for protecting your organization from security threats.
Which activities typically require privileged access?
Activities typically requiring privileged access include granting and revoking access for other users, connecting to sensitive data, and configuring, provisioning, and managing infrastructure.
How does implementing least privilege minimize privileged access abuse?
The principle of least privilege works by allowing only enough access to perform the required job. In an IT environment, adhering to the principle of least privilege reduces the risk of attackers gaining access to critical systems or sensitive data by compromising a low-level user account, device, or application.
Why are privileged access devices important?
A Privileged Access Workstation (PAW) is a dedicated computing environment for sensitive tasks that is protected from Internet attacks and other threat vectors. A PAW separates these sensitive tasks and accounts from non-administrative computer use, such as email and web browsing.
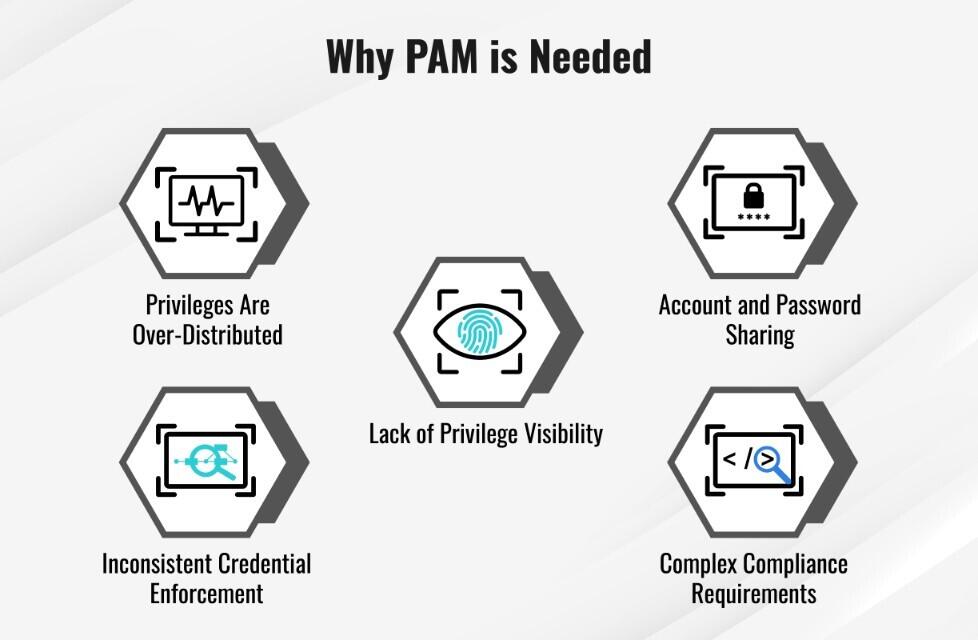
Why is PAM solution needed
Why PAM PAM helps organizations protect against the accidental or deliberate misuse of privileged access by streamlining the authorization and monitoring of privileged users. Controlling and monitoring privileged user access to your most critical data and systems is the best way to prevent attacks.
What is a PAM and why is IT important
PAM provides administrators with the functionality, automation and reporting they need to manage privileged accounts. In addition, it supports the principle of least privilege as it allows for the necessary management and oversight to mitigate the risk of accounts that have capabilities beyond the standard user.
Cached
What are the risks of not having PAM
Without a PAM solution, organizations may struggle to gain visibility into the access and permissions of their employees and third parties. This can make it difficult to identify potential security risks and take steps to mitigate them.
What is the business value of privileged access management
Through PAM, organizations can easily detect and monitor suspicious activities that could put customer and company data at risk. It allows organizations to establish a comprehensive risk management strategy, ensure regulatory adherence, and avoid hefty sanctions due to non-compliance.
How does PAM work
PAM software and tools work by gathering the credentials of privileged accounts, also known as system administrator accounts, into a secure repository to isolate their use and log their activity. The separation is intended to lower the risk of admin credentials being stolen or misused.
What is the difference between IAM and PAM
While IAM identifies each user and allows them access to an array of applications and services, PAM manages access and user's actions on highly sensitive systems that are often limited to those with administrative privileges. This difference also means the level of risk each system manages is vastly different.
What is PAM for dummies
Privileged Access Management for Dummies is written for IT and systems administrators, along with security professionals responsible for protecting your organization from security threats.
Which activities typically require privileged access
Activities typically requiring privileged access include:granting and revoking access for other users.connecting to sensitive data, and.configuring, provisioning, and managing infrastructure.
How does implementing least privilege minimize privileged access abuse
The principle of least privilege works by allowing only enough access to perform the required job. In an IT environment, adhering to the principle of least privilege reduces the risk of attackers gaining access to critical systems or sensitive data by compromising a low-level user account, device, or application.
Why are privileged access devices important
A Privileged Access Workstation (PAW) is a dedicated computing environment for sensitive tasks that is protected from Internet attacks and other threat vectors. A PAW separates these sensitive tasks and accounts from non-administrative computer use, such as email and web browsing.
How are privileged accounts usually stolen
How Privileged Account Passwords are Stolen. Up to 80 percent of breaches result from stolen passwords. Hackers' most preferred pathway to privilege exploitation is to steal account credentials. Hackers may use malware or social engineering to steal account information for gaining unauthorized access.
How do you implement PAM
Here are the steps of the PAM Lifecycle:Define. Define and classify privileged accounts.Discover. Discover your privileged accounts.Manage and protect. Protect your privileged account passwords.Monitor.Detect abnormal usage.Respond to incidents.Review and audit.
Is PAM the same as MFA
PAM ensures these accounts can only access the assets they have privileges for. MFA, as part of a broader IAM solution, adds another layer of security, ensuring PAM is only allowing privileged access to verified users.
What are the 3 types of IAM principals
Principalsa principal is an IAM entity allowed to interact with AWS resources, and can be permanent or temporary, and represent a human or an application.three types of principals.Root User.IAM Users.Roles/Temporary Security Tokens.
Is Active Directory a PAM tool
The answer is no—at least, not on its own. Active Directory allows administrators to manage permissions and control access to network resources, but you will need additional support to implement a comprehensive PAM strategy.
Why is privileged access important
Privileged access allows organizations to secure their infrastructure and applications, run business efficiently and maintain the confidentiality of sensitive data and critical infrastructure. Privileged access can be associated with human users as well as non-human users such as applications and machine identities.
Why is implementing least privilege important
The principle of least privilege prevents the spread of malware on your network. An administrator or superuser with access to a lot of other network resources and infrastructure could potentially spread malware to all those other systems.
What is least privilege and why is IT so important in security
The principle of least privilege (PoLP) is an information security concept which maintains that a user or entity should only have access to the specific data, resources and applications needed to complete a required task.
How does PAM works
PAM works through a combination of people, processes, and technology and gives you visibility into who is using privileged accounts and what they are doing while they are logged in.
Why do we need to protect privileged accounts
Privileged accounts have the highest level of protection because they represent a significant or material potential impact on the organization's operations if compromised. Privileged accounts always include IT Admins with access to most or all enterprise systems, including most or all business critical systems.
Why is it important to secure privileged accounts
Privileged access allows organizations to secure their infrastructure and applications, run business efficiently and maintain the confidentiality of sensitive data and critical infrastructure. Privileged access can be associated with human users as well as non-human users such as applications and machine identities.
How does PAM differ from IAM
While IAM identifies each user and allows them access to an array of applications and services, PAM manages access and user's actions on highly sensitive systems that are often limited to those with administrative privileges. This difference also means the level of risk each system manages is vastly different.
What are the 4 components of IAM
IAM components can be classified into four major categories: authentication, authorisation, user management, and central user repository.
What are the five pillars of IAM
We'll cover the key components of an IAM strategy. You'll learn about: The five pillars of IAM: Lifecycle and governance; federation, single sign-on and multi-factor authentication; network access control; privileged account management; and key encryption. Example scenarios of each pillar.
How does PAM work with LDAP
The pam_ldap module provides the ability to specify a list of hosts a user is allowed to log into, in the "host" attribute in LDAP. The host attribute can be specified multiple times for each user. If any of the entries match the hostname of the machine logging in to, login is succesful.



