Why SMS OTP is not safe?
Summary
Bots can bypass OTPs, and attackers can intercept OTPs or use bots to bypass OTP-based two-factor authentication. There are disadvantages to OTP authentication, such as delays or emails ending up in the spam folder. SMS verification is more secure than passwords alone, but it has vulnerabilities. SMS authentication is not encrypted and vulnerable to social engineering scams and MITM attacks. Authenticator apps are faster and more reliable than SMS OTP and provide an additional layer of security. Hackers can access OTPs through email hacking or by hijacking accounts protected solely by a password. One-time passwords offer greater security for users but can be cumbersome to generate. The risks of using SMS include interception of SMS messages containing sensitive information. SMS can be hijacked, and rerouting text messages can lead to easy access to other accounts. SMS two-factor authentication can be hacked using MITM attacks or exploiting vulnerabilities in the account recovery process. SMS 2FA has disadvantages like long OTP lifetime and the ease of removing SIM cards from unguarded phones.
Questions and Answers
1. Can SMS OTP be intercepted?
Yes, attackers can intercept SMS OTPs or bypass them using bots.
2. What is the disadvantage of OTP authentication?
Users may have difficulties accessing OTPs, such as delays or emails ending up in spam folders.
3. Is SMS verification safe?
SMS verification is relatively secure but has vulnerabilities. Hackers need physical access to the phone to gain access to the account.
4. What are the cons of SMS authentication?
SMS authentication is not encrypted and is susceptible to social engineering scams and MITM attacks.
5. Is SMS OTP better than an authenticator?
Authenticator apps are faster, more reliable, and provide an additional layer of security compared to SMS OTP.
6. Can hackers access your OTP?
Yes, hackers can access OTPs through email hacking or by hijacking accounts protected solely by a password.
7. What are the pros and cons of OTP?
| Advantages | Disadvantages |
|---|---|
| No danger that a stolen password can be used for multiple sites or services | Security tokens can fail or break |
| Greater security for users | Process of OTP password generation can be cumbersome |
8. What are the risks of using SMS?
SMS messages are not encrypted and can be intercepted and read by attackers, compromising the targeted account.
9. Can SMS be hijacked?
Yes, if a hacker is able to reroute a target’s text messages, they can easily access accounts associated with that phone number.
10. Can SMS two-factor authentication be hacked?
Yes, hackers can use MITM attacks or exploit vulnerabilities in the account recovery process to access the verification code and hack accounts.
11. What are the disadvantages of SMS 2FA?
SMS OTPs have a long lifetime, giving attackers time to conduct cyberattacks. SIM cards can also be easily removed and installed in another phone.
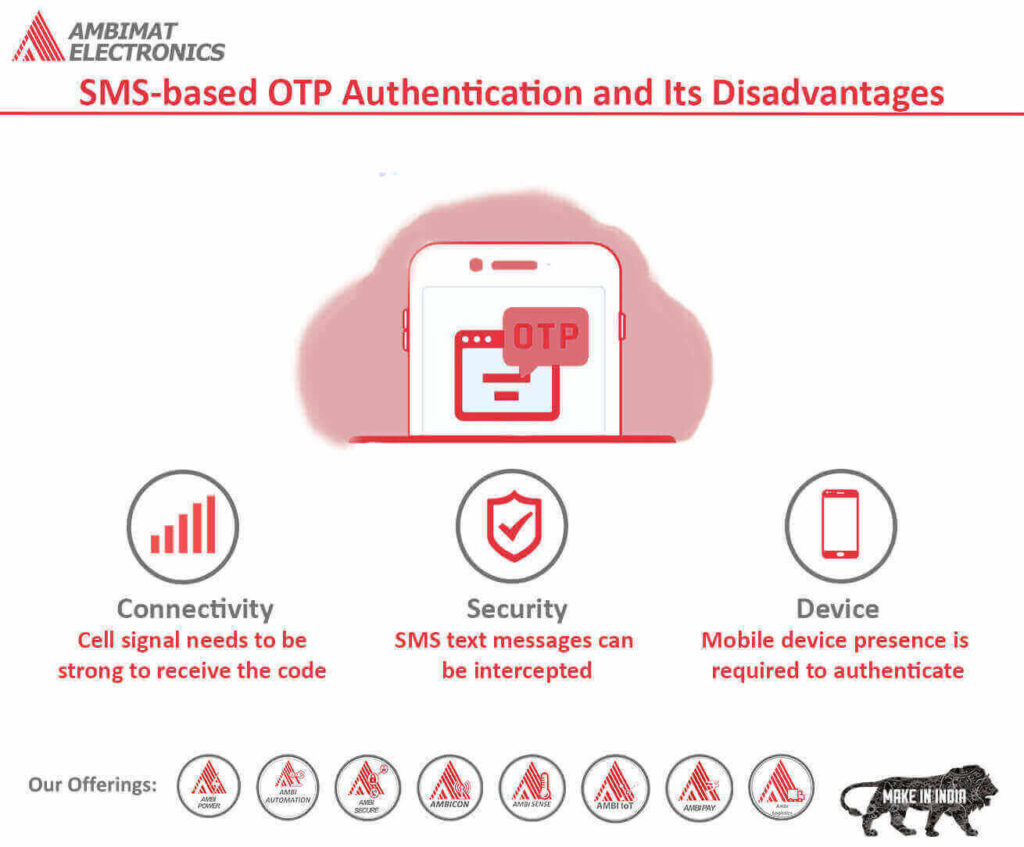
Can SMS OTP be intercepted
Bots can Bypass OTPs
In addition to intercepting OTPs, attackers can use bots to bypass OTP-based two factor authentication verification altogether.
What is the disadvantage of OTP authentication
A user may also be unable to access the OTP. Some emailed OTPs may be delayed or end up in a Spam folder. If a user loses a physical token, they've lost access to their OTP.
Is SMS verification safe
Is SMS secure SMS verification is more secure than passwords alone, although it has its vulnerabilities. Hackers need physical access to your phone to get into your account, but once they have your phone, it becomes that much easier.
What are the cons of SMS authentication
The problem with SMS authentication is that SMS is not encrypted and is highly susceptible to social engineering scams and MiTM attacks. Attackers can even clone or swap user SIM cards to access OTPs. They can also trick phone services providers and users into disclosing secret authentication codes.
Cached
Is SMS OTP better than authenticator
Authenticator apps are not only faster and more reliable than SMS 2FA, they also enforce an additional layer of security, such as a passcode, a password or biometrics (i.e. fingerprint).
Can hackers access your OTP
Email hacking
If an email account is protected solely by a password, attackers can hijack the account using a MitM or social engineering attack and then capture OTPs sent to it. Security is only as strong as the weakest link.
What are the pros and cons of OTP
Pros and cons of one-time passwords at a glance
| Advantages | Disadvantages |
|---|---|
| No danger that a stolen password can be used for multiple sites or services | Security tokens can fail or break |
| Greater security for users | Process of OTP password generation can be cumbersome |
What are the risks of using SMS
SMS messages are not encrypted, and as a result, they can be intercepted and read by attackers. If the SMS message contains sensitive information, such as a six-digit authentication code, it can be used by attackers to gain access to the targeted account.
Can SMS be hijacked
Once the hacker is able to reroute a target's text messages, it can then be trivial to hack into other accounts associated with that phone number. In this case, the hacker sent login requests to Bumble, WhatsApp, and Postmates, and easily accessed the accounts.
Can SMS two-factor authentication be hacked
They could use the same MITM attack technique used to intercept data transfer on the internet. Or, they could use a phishing attack and exploit vulnerabilities in the SMS account recovery process to get hold of the verification code. That's what they did with Coinbase in 2021. More than 6,000 accounts were hacked.
What are the disadvantages of SMS 2FA
Cons of SMS 2FA:
One-time passwords have a long lifetime – SMS OTPs expire after several minutes, which gives attackers time to conduct a cyberattack. SIM card can be easily removed and installed in another phone – An attacker needs only several seconds to remove the SIM card from your unguarded phone.
Is SMS two-factor authentication insecure
SMS has long been regarded as a vulnerable communications protocol by security experts—but where 2FA is concerned, the biggest danger is with the possibility of SIM-swapping attacks. In a SIM swap, the bad guys trick cellular carriers into transfering a phone number to a SIM card that they control.
Which is the safest authentication type
CategoriesThe Three Types of Authentication Factors.Least Secure: Passwords.More Secure: One-time Passwords.More Secure: Biometrics.Most Secure: Hardware Keys.Most Secure: Device Authentication and Trust Factors.
What can someone do with your OTP number
You are duped into revealing the OTP to a fraudster on call/sms/email. Fraudsters will try to lure you by making false promises of helping with a transaction or providing better services and if their attempts succeed, trick you into completing unauthorized transactions or even cause identity theft.
What happens if someone knows my OTP
and once you share the OTP, he would get access to your account. To gain your trust, he might mention that he is from a bank or from a trusted third party. Using an OTP a person can create an account by pretending to be you. That account can be used for the wrong purposes.
Should I give OTP to someone
To not become a victim of OTP fraud, you must not share your OTPs over the phone. Banks or any service provider never ask for your passwords or OTPs. App pin, UPI pin, CVV number, expiry date of debit card and 16 digit debit card number is for personal use. These should never be shared with anyone in any circumstances.
What are the main threats that OTP capable to control
OTP helps in preventing replay attacks, phishing attacks and other attacks which are possible to occur on static passwords.
Can SMS messages get hacked
Yes, it's definitely possible for someone to spy on your text messages and it's certainly something you should be aware of – this is a potential way for a hacker to gain a lot of private information about you – including accessing PIN codes sent by websites used to verify your identity (such as online banking).
Can a phone be hacked by an SMS
This is how it works: Step 1: Attackers send a malicious SMS, which is specifically crafted, consisting of binary code (spyware-like code) like spyware on the phone they want to hack. Step 2: On receiving the SMS, the device is hacked as soon as the person clicks on the malicious link given in the SMS.
Can hackers intercept OTP
Text messages aren't encrypted, and they're tied to your phone number rather than a specific device. Below are two types of common attacks that enable hackers to intercept SMS OTP authentication: SIM swaps. The fraudster harvests personal details from the victim, either via phishing or social engineering.
Can someone steal your SMS messages
Spyware can be used by anyone, not just hackers
The app can be installed remotely on an iPhone if you have the proper iCloud credentials. For Android phones, someone will need to install it on the phone directly. Once that's done, your messages and more can be intercepted.
Is SMS or Authenticator more secure
Authenticator apps are not only faster and more reliable than SMS 2FA, they also enforce an additional layer of security, such as a passcode, a password or biometrics (i.e. fingerprint).
Why 2 step verification is not safe
2FA can be vulnerable to several attacks from hackers because a user can accidentally approve access to a request issued by a hacker without acknowledging it. This is because the user may not receive push notifications by the app notifying them of what is being approved.
Can SMS 2FA be hacked
Social engineering is one of the primary tools hackers use, and bypassing SMS 2FA is no different. As with traditional phishing, smishing can see hackers directly approach users and attempt to socially engineer them into surrendering a 2FA verification code.
Which type of authentication mode is not recommended
If non-authentication is used, any user can be successfully authenticated without the need of entering the user name and password. Therefore, you are not advised to use non-authentication for device or network security purposes.



