What are sensitive breaches?
Summary of the Article
Sensitive data breaches occur when databases storing information are not adequately protected. This can happen due to weak or no encryption, software flaws, or accidental data uploads to incorrect databases.
There are three types of breaches, including material breaches, minor breaches, and repudiation.
Examples of breaches include stolen user credentials, phishing attacks, business email compromise, and supply chain attacks.
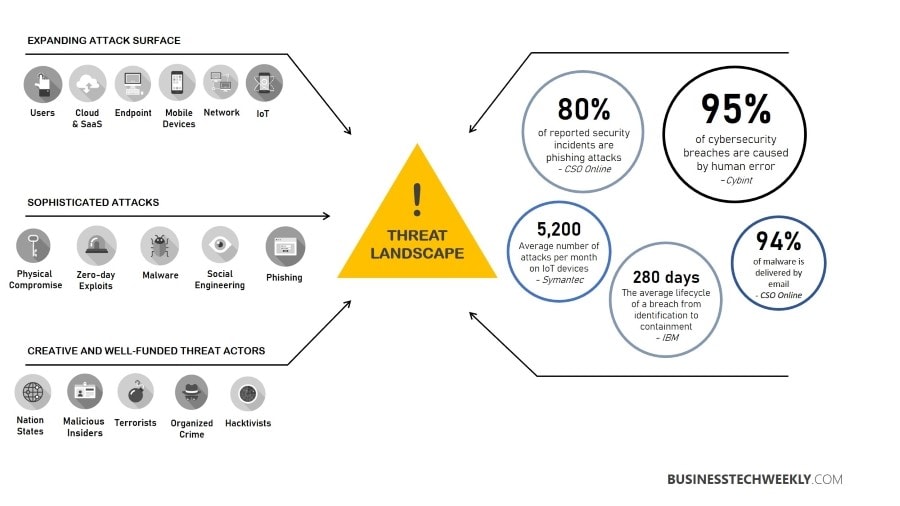
The most common types of data breaches are stolen information, password guessing, recording keystrokes, phishing, malware or virus attacks, and distributed denial of service (DDoS) attacks.
Examples of sensitive data include genetic data, biometric data, health-related data, and data related to a person’s sex life or sexual orientation.
Sensitive information includes biometric data, medical information, personally identifiable financial information (PIFI), and unique identifiers such as passport or Social Security numbers.
There are four types of contract breaches: anticipatory, actual, minor, and material breaches.
The two main types of security breaches are exploit attacks targeting system vulnerabilities and weak passwords or malware attacks through phishing emails or compromised websites.
A breach of contract can either be an actual breach when one party refuses to fulfill the terms or an anticipatory breach when a party states in advance that they will not meet the contract’s terms.
The number one cause of security breaches is weak credentials, such as stolen or easily guessable passwords.
Some of the top five causes of data breaches include weak and stolen credentials, back doors and application vulnerabilities, malware, social engineering, and improper configuration or user error.
Questions:
- What is a sensitive data breach?
A sensitive data breach occurs when a database containing information is not adequately protected, leading to unauthorized access or exposure of sensitive data. - What are the three types of breaches?
The three types of breaches are material breaches, minor breaches, and repudiation breaches. - What are examples of breaches?
Examples of breaches include stolen user credentials, phishing attacks, business email compromise, and supply chain attacks. - What are the most common breaches?
The most common types of data breaches are stolen information, password guessing, recording keystrokes, phishing, malware or virus attacks, and distributed denial of service (DDoS) attacks. - What are examples of sensitive data?
Examples of sensitive data include genetic data, biometric data, health-related data, and data related to a person’s sex life or sexual orientation. - What is an example of sensitive information?
Sensitive information includes biometric data, medical information, personally identifiable financial information (PIFI), and unique identifiers such as passport or Social Security numbers. - What are the 4 types of breach?
The four types of contract breaches are anticipatory, actual, minor, and material breaches. - What are the two main types of security breaches?
The two main types of security breaches are exploit attacks targeting system vulnerabilities and weak passwords or malware attacks through phishing emails or compromised websites. - What are the two types of breach?
The two types of breaches in contract law are actual breach and anticipatory breach. - What is the #1 cause of security breaches?
The number one cause of security breaches is weak credentials, such as stolen or easily guessable passwords. - What are three of the top five causes of breaches?
Three of the top five causes of data breaches are weak and stolen credentials, back doors and application vulnerabilities, and malware.

What is a sensitive data breach
Sensitive data exposure occurs as a result of not adequately protecting a database where information is stored. This might be a result of a multitude of things such as weak encryption, no encryption, software flaws, or when someone mistakenly uploads data to an incorrect database.
Cached
What are the three types of breaches
3 Types of Breach of ContractMaterial Breach. The first and most severe type of breach is a 'material' breach (also known as a 'fundamental breach').Minor Breach. It is important to be clear that not all breaches of a contract will be material.Repudiation.
What are examples of breaches
The IBM report found that stolen user credentials are the most common cause of data breaches. Modern email attacks like phishing, business email compromise, and supply chain attacks rely on social engineering to trick victims into giving up credentials.
Cached
What are the most common breaches
The 7 Most Common Types of Data Breaches and How They Affect Your BusinessStolen Information.Password Guessing.Recording Keystrokes.Phishing.Malware or Virus.Distributed Denial of Service (DDoS)
What are examples of sensitive data
genetic data, biometric data processed solely to identify a human being; health-related data; data concerning a person's sex life or sexual orientation.
What is an example of sensitive information
Such information includes biometric data, medical information, personally identifiable financial information (PIFI) and unique identifiers such as passport or Social Security numbers.
What are the 4 types of breach
Generally speaking, there are four types of contract breaches: anticipatory, actual, minor and material.Anticipatory breach vs. actual breach.Minor breach vs. material breach.What's next: Types of remedies for broken contracts.
What are the two main types of security breaches
Types of security breachesAn exploit attacks a system vulnerability, such as an out of date operating system.Weak passwords can be cracked or guessed.Malware attacks, such as phishing emails can be used to gain entry.Drive-by downloads use viruses or malware delivered through a compromised or spoofed website.
What are the two types of breach
Further, a breach of contract generally falls under one of two categories:Actual breach: When one party refuses to fully perform the terms of the contract.Anticipatory breach: When a party states in advance that they will not be delivering on the terms of the contract.
What is the #1 cause of security breaches
Common vulnerabilities targeted by malicious criminals include the following: Weak credentials. The vast majority of data breaches are caused by stolen or weak credentials. If malicious criminals have your username and password combination, they have an open door into your network.
What are three of the top five causes of breaches
8 Most Common Causes of Data BreachWeak and Stolen Credentials, a.k.a. Passwords.Back Doors, Application Vulnerabilities.Malware.Social Engineering.Too Many Permissions.Insider Threats.Physical Attacks.Improper Configuration, User Error.
What are the 4 types of sensitive data
Answerpersonal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs;trade-union membership;genetic data, biometric data processed solely to identify a human being;health-related data;data concerning a person's sex life or sexual orientation.
What are 10 examples of sensitive personal information
What is sensitive informationracial or ethnic origin.political opinions or associations.religious or philosophical beliefs.trade union membership or associations.sexual orientation or practices.criminal record.health or genetic information.some aspects of biometric information.
What are 3 types of sensitive information
There are three main types of sensitive information:Personal Information. Also called PII (personally identifiable information), personal information is any data that can be linked to a specific individual and used to facilitate identity theft.Business Information.Classified Information.
What are the 4 common causes of data breaches
Six Common Causes of Data BreachesCause 1. Insider Threats Due to Misuse of Privileged Access.Cause 2. Weak and Stolen Passwords.Cause 3. Unpatched Applications.Cause 4. Malware.Cause 5. Social Engineering.Cause 6. Physical Attacks.
How many types of breach are there
A breach is a failure by a party to fulfil the obligations under a contract. It is of two types, namely, anticipatory breach and actual breach.
What is considered a security breach
A security breach is any unauthorized access to a device, network, program, or data. Security breaches happen when network or device security protocols are penetrated or otherwise circumvented.
What are the 4 elements of breach
These types of lawsuits are common in business litigation. There are four elements of a breach of contract claim: a valid contract, performance, breach, and damages.
What are the three main causes of data breaches
In this blog, we explain 5 of the most common causes of data breach and provide advice on how to identify them.Weak and stolen credentials. Stolen passwords are one of the simplest and most common causes of data breaches.Application vulnerabilities.Malware.Malicious insiders.Insider error.
What are three types of sensitive information
There are three main types of sensitive information:Personal Information. Also called PII (personally identifiable information), personal information is any data that can be linked to a specific individual and used to facilitate identity theft.Business Information.Classified Information.
What counts as sensitive information
Sensitive information typically includes personal identifying information such as names, addresses, Social Security numbers, and government-issued IDs, as well as financial and medical information, criminal records, and any other data that could be used to identify or track an individual.
What is an example of sensitive info
genetic data, biometric data processed solely to identify a human being; health-related data; data concerning a person's sex life or sexual orientation.
What are the three biggest data breaches of all time
Top 23 Biggest Data Breaches in US History1. Yahoo! Date: 2013-2016.Microsoft. Date: January 2021.First American Financial Corp. Date: May 2019.4. Facebook. Date: April 2021.LinkedIn. Date: April 2021.JPMorgan Chase. Date: June 2014.Home Depot. Date: April 2014.MySpace. Date: June 2013.



